Contents
- What is Active Directory?
- How Active Directory Works?
- Active Directory Backup Recommendations
- Back up your Active Directory regularly
- Keep at least one of the domain controllers backed up
- Prioritize software that provides data consistency
- Your disaster recovery plan must include AD backup
- Look for granular recovery option, if possible
- Native Active Directory Backup Tools and Services
- Windows Server Backup
- System Center Data Protection Manager
- Third-party Active Directory Backup Methods
- NAKIVO Backup & Replication
- Quest Recovery Manager
- MSP360 (formerly Cloudberry Lab)
- EaseUS Todo Backup Enterprise
- Acronis Cyber Protect
- Vembu BDR Suite
- Arcserve Backup
- Veeam Backup & Replication
- Zmanda
- Physical and virtual domain controller
- Active Directory Backup with Bacula Enterprise
- Conclusion
 What is Active Directory?
What is Active Directory?
Active Directory from Microsoft (MS AD) is one of the most widely used user authentication and network permissions management tools in the world. It allows for federated login across an entire corporate network and management of user roles and permissions from a single point across multiple services.
This service is extremely valuable for larger and more developed business structures, since system administrators would be more efficient managing computers that were added to the domain centrally. Services like Microsoft Exchange and Microsoft SQL Server also need Active Directory to operate properly. Any instance of Active Directory Domain Controller going offline is a significant problem since all users won’t be able to log in and the overall system would be unable to work properly in general.
Even as companies move to the cloud and SaaS offerings, integration with the existing AD infrastructure is often considered a requirement for success of the project. With this said, the complexity of Active Directory as well as its ability to be maintained at nearly perfect uptime means that a viable Active Directory backup and disaster recovery solution is an absolute necessity.
Worth noting: AD Disaster Recovery (DR) is something that should not be done – or confused with – directory server backups because those plans should include ways to get back to before the oldest tombstone. Similarly, single-item granularity directory server data restores must not be confused with DR. See the last paragraph of this blog for more details.
How Active Directory Works?
The core of Active Directory as a management system is a database that holds both transaction logs and individual objects. This database is split into multiple parts – and each part holds a different type of information, either domain names context (groups of users or individual ones) or configuration/schema partition (AD structure info and AD design info respectively). The structure of Active Directory database is hierarchical and its shape looks a lot like a tree. The main file that’s used for Active Directory database storage is Ntds.dit.
Active Directory works through several protocols to ensure the security of the network it’s operating with. Those protocols are the following:
- LDAP protocol (Lightweight Directory Access Protocol) is used for directory access (Active Directory and others) and directory authentication services through both username and password, it’s also open and cross-platform;
- Kerberos protocol is a cryptography-based protocol that’s used for single sign-on and secure authentication operations, it checks usernames and passwords before storing them within LDAP directory.
Active Directory is also deeply integrated with Windows-protected system files, DNS Server, COM+ Class Registration Database, Sysvol directory, cluster service information and several others. This amount of integrations also directly influences the overall Active Directory backup strategy.
Active Directory Backup Recommendations
Next we’ll talk about several general usage recommendations while backing up your Active Directory server.
Back up your Active Directory regularly
The recommended backup frequency for Active Directory is no more than 60 days. The reason for this is one of the specifics of Active Directory database management – AD tombstone objects.
When the object in the Directory is deleted (meaning most of the object’s attributes, or all of them, are deleted) – it’s marked as a tombstone object and doesn’t get physically deleted until the expiration of the tombstone lifetime span, which is 60 days exactly. If you have several domain controllers operating at the same time and the Active Directory replication function is enabled – all those tombstone files would be copied at each and every one of your controllers and is kept there until its expiration time. There’s also the fact that if you’re restoring a domain controller backup that’s been created more than 60 days before today – you’re bound to get lots of inconsistencies due to one of the domain controllers having info about objects that don’t even exist anymore.
One more reason for the “60 days or less” mark is that any software or driver installed after the last backup would not work at all in the case of data restoration since there’ll be no information in the registry about said drivers or software.
There are far more potential problems that can arise due to the data not being backed up frequently enough. The most “safe” recommendation is to do Active Directory backup on a daily basis.
Keep at least one of the domain controllers backed up
This advice is mostly for larger companies that have more than one domain controller in their infrastructure. You should back up at least one of your domain controllers if you have several of them to ensure at least partial data recovery in the case of some sort of hardware or software failure. Also if you have FSMO (Flexible Single Master Operation) roles installed on one of your controllers – you should prioritize backing it up first. That way, if you lose all of your controllers, you can recover one of them – the one with FSMO – that will be considered “primary”, and after that, if you deploy another controller – you’ll be able to, essentially, copy all of the changes from the “primary” domain controller to “secondary” one.
Prioritize software that provides data consistency
It’s quite a common knowledge that any backup should be done in a way to ensure that its’ consistency is preserved. The same goes for Active Directory backup. The best option is to backup the data while the server is turned off, or when VSS is used on a running server. On the contrary – trying to back up data from the server that’s working 24/7 is not the best idea. That’s why it’s highly recommended to use VSS-compatible services for any of your Active Directory backup needs. VSS creates a snapshot of the data, which essentially freezes the system and its’ info until the backup process is complete. That way you won’t lose or corrupt files that were rewriting themselves on the server at the time the backup was creating itself.
Your disaster recovery plan must include AD backup
Having a disaster recovery plan is a must in general, and the more scenarios you can predict and prevent or prepare for – the better you’ll be in the case of disaster of some kind. AD backup in this case is important because essentially you can’t use any AD-related services if you restore them before you restore your AD backup. You can backup your domain controller to several different storage locations:cloud, local or remote site. Having more than one copy of your Active Directory is highly recommended, as well.
Look for granular recovery option, if possible
While the process of recovering and rewriting all of your Active Directory data is a good idea most of the time – you may want to look for services that provide granular recovery option as well. That way if you want to recover only one or a few files from your backup – you’ll be able to do so quite easily. This also reduces the overall data restore time, especially when your Active Directory is bigger than the average one.
Native Active Directory Backup Tools and Services
There are several native backup tools for Active Directory created by Microsoft for backing up Windows Servers, including the ones that are running Active Directory domain controllers.
Windows Server Backup
Windows Server Backup is a program that replaced NTBackup in Windows Server 2008 and newer versions. WSB comes with a new interface and the ability to create incremental backups with the usage of VSS (Microsoft Volume Shadow Copy Service). The data that’s been backed up is saved in VHD format. After backing it up you will be able to mount such VHD disks to a machine – both virtual and physical – to access the data you’ve backed up. The difference between this VHD and the one that’s created using MVMC (Microsoft Virtual Machine Converter) is that this VHD isn’t bootable. The command for backing up the whole volume or the system state is the following: wbadmin start systemstatebackup .
The main advantages of this backup method for Active Directory backup are the following: it’s affordable, it can work with VSS, and you can either back up the entire system or back up nothing but Active Directory files. The main disadvantage is that working with WSB requires a lot of prior knowledge and understanding to reach the program’s full potential in regards to both backup and recovery process.
System Center Data Protection Manager
The other backup service created by Microsoft is System Center Data Protection Management (SC DPM). Creating both the usual data backups and the Active Directory backups is within the program’s capabilities. SC DPM is an enterprise-level backup/recovery service that can be used for Windows Server data protection (which includes Active Directory backups). The difference between WSB and SC DPM is that the former is free, while the latter is a paid software that’s installed separately and not included in the basic Microsoft system package. It’s also somewhat harder to set up compared to WSB. But it’s still highly recommended to use it to ensure your device’s complete protection. The list of SC DPM features includes VSS support, incremental backup support, Microsoft Azure cloud backup support and the inability to recover singular files from backed up Active Directory. The most practical usage of SC DPM is to protect a number of Microsoft Exchange/Microsoft SQL servers and other Windows-based devices.
Third-party Active Directory Backup Methods
Even though both WSB and SC DPM are the native solutions for backing up Active Directory – there are a lot of other possible solutions for this. In fact, almost every enterprise-level backup service should be capable of backing up Active Directory with little to no problems. The difference between all those services in that case is the way some of them provide more capabilities while dealing with both backing up and restoring the Active Directory.
The main point of backups in general works with Active Directory as well – the data backup has to be done in a specific way to ensure that the data is consistent enough. Most of the third-party backup services uses VSS to create a snapshot of the copied data to prevent said data from being in any way modified in the middle of the backup process. There’s also the possibility of another issue happening: if the backup of Active Directory is written to a physical disc – the snapshot that was created will be used for the write operation, but if it’s based on the live Active Directory database copy – inconsistencies are bound to arise one way or another.
Each backup provider has their own specific way of dealing with said problem, some more effective than others.
Plus, some of the third-party backup services can provide very specific object restoration for Active Directory backups. One of the examples of that is the ability to restore individual user accounts rather than the whole database. But not all backup products can do that; most of them can only provide full backup-and-restore service for Active Directory backups.
To make this particular topic easier to discuss, we show here several different examples of enterprise backup solutions and their Active Directory-related capabilities:
NAKIVO Backup & Replication

NAKIVO is one of the more well-known faces on the enterprise backup market, and NAKIVO Backup & Replication is a great multifunctional solution suitable for many use cases, be it physical environments, cloud environments, or some form of hybrid system. The solution itself is fast, reliable and packs a variety of features, including low backup size, file recovery on-demand, incremental backup and many others.
NAKIVO Backup & Replication offers host-level backups to both Hyper-V and VMware VMs that run Active Directory Domain Controllers. It can offer instant AD object recovery, as well as the ability to create complete application-aware backups of VM domain controllers (VSS is used to perform backups of VMs that are still running). The solution itself is agentless and can also perform granular AD recovery to restore specific objects or containers if necessary.
Customer ratings:
- Capterra – 4.8/5 stars based on 305 customer reviews
- TrustRadius – 9.2/10 stars based on 142 customer reviews
- G2 – 4.7/5 stars based on 203 customer reviews
Advantages:
- NAKIVO’s customer support received a lot of praise over the years and the overwhelming majority of user reviews cite fast response time and general usefulness of the customer support team
- Most enterprise-level backup solutions tend to have a wealth of different features in them, which can be a real problem for for the potential user if there is no proper user interface in place that can make it easier to interact with the entire feature set – and NAKIVO’s interface is often considered one of the most user-friendly on the entire market
- Initial configuration for an enterprise-level backup solution is bound to be difficult to a certain degree, but solutions like NAKIVO try to make it easier by providing better guidance for all configuration steps and taking advantage of a user-friendly interface
Shortcomings:
- The pricing of different solutions on this particular market tends to differ quite a lot from one another, but it is safe to say that NAKIVO’s offerings are all well above the market average price
- Error logs are usually the best way to look for insights after a crash or an error of sorts, but it may be difficult to do exactly that with NAKIVO, as its reporting and logging capabilities are rather basic and non-descriptive
- If a potential customer of NAKIVO wants it to work with Linux-based physical servers, then the customer in question should expect quite a few limitations in functionality compared with the Windows version
- There are certain limitations with scalability in an enterprise environment.
Pricing:
- NAKIVO’s pricing is offered in two significantly different forms – the subscription-based model and the:
- Subscription-based licenses:
- “Pro Essentials” – from $1.95 per month per workload, covers most common backup types such as physical, virtual, cloud and NAS, while also offering instant granular recovery, virtual and cloud replication, storage immutability, and more
- “Enterprise Essentials” – from $2.60 per month per workload, adds native backup to tape, deduplication appliance integration, backup to cloud, as well as 2FA, AD integration, calendar, data protection based on policies, etc.
- “Enterprise Plus” does not have public pricing available, it adds HTTP API integration, RBAC, Oracle backup, backup from snapshots, and other features
- There is also a subscription available for Microsoft 365 coverage that costs $0.80 per month per user with an annual billing and can create backups of MS Teams, SharePoint Online, Exchange Online, OneDrive for Business, and more
- Another subscription from NAKIVO is its VMware monitoring capability that comes in three different forms:
- “Pro Essentials” for $0.90 per month per workload with CPU, RAM, disk usage monitoring and a built-in live chat
- “Enterprise Essentials” for $1.15 per month per workload that adds AD integration, 2FA capability, multi-tenant deployment, and more
- “Enterprise Plus” with no public pricing that adds RBAC and HTTP API integrations
- Perpetual licenses:
- Virtual environments:
- “Pro Essentials” for $229 per socket, covers Hyper-V, VMware, Nutanix AHV, and features such as instant granular recovery, immutable storage, cross-platform recovery, etc.
- “Enterprise Essentials” for $329 per socket, adds native backup to tape, backup to cloud, deduplication, 2FA, AD integration, and more
- “Enterprise Plus” with no public pricing that adds RBAC and HTTP API integrations, as well as backup from storage snapshots
- Servers:
- “Pro Essentials” for $58 per server, covers Windows and Linux, and features such as immutable storage, instant P2V, instant granular recovery, etc.
- “Enterprise Essentials” for $329 per server, adds native backup to tape, backup to cloud, deduplication, 2FA, AD integration, and more
- “Enterprise Plus” with no public pricing that adds RBAC and HTTP API integrations
- Workstations:
- “Pro Essentials” for $19 per workstation, covers Windows and Linux, and features such as immutable storage, instant P2V, instant granular recovery, etc.
- “Enterprise Essentials” for $25 per workstation, adds native backup to tape, backup to cloud, deduplication, 2FA, AD integration, and more
- “Enterprise Plus” with no public pricing that adds RBAC and HTTP API integrations
- NAS:
- “Pro Essentials” for $149 per one Terabyte of data, can backup NFS shares, SMB shares, folders on shares, and offer file level recovery
- “Enterprise Essentials” for $199 per one Terabyte of data, adds AD integration, 2FA support, calendar, multi-tenant deployment, etc.
- “Enterprise Plus” with no public pricing that adds RBAC and HTTP API integrations
- Oracle DB:
- “Enterprise Plus” is the only option available for Oracle database backups via RMAN, it can offer advanced scheduling, centralized management, and more
- VMware monitoring:
- “Pro Essentials” for $100 per socket with CPU, RAM, disk usage monitoring and a built-in live chat
- “Enterprise Essentials” for $150 per socket that adds AD integration, 2FA capability, multi-tenant deployment, and more
- “Enterprise Plus” with no public pricing that adds RBAC and HTTP API integrations
- Virtual environments:
- As you can see here, Active Directory support is included in both the subscription-based model and the perpetual license model of NAKIVO starting from the “Enterprise Essentials” level and above.
My personal opinion on NAKIVO:
AD backup as a feature is rarely the only reason for a large or medium-sized company to start looking for a backup solution in the first place. This feature is usually just one of many, many different functions that a business would like to see in a backup solution or platform. In this context, NAKIVO is one of the best options on the market, with a wealth of different features to choose from, a variety of supported storage types, and so on.
Quest Recovery Manager
Unlike most of the solutions on this list, Quest Recovery Manager’s only purpose is to create and manage Active Directory backups. Recovery Manager describes itself as an “insurance plan for your AD environment” – not only it can offer AD backup capabilities, but there is also an option to constantly monitor for changes in the AD environment at the granular level, as well as instant recovery, granular backup comparison, and more.
Customer ratings:
- G2 – 4.6/5 stars based on 11 customer reviews
Advantages:
- High backup availability and the general convenience of having an AD backup at hand
- High degree of automation allows AD backups to be far more efficient after the initial setup is complete
- Incremental backup capabilities are greatly boosting the overall user experience, improving speed and reducing storage space usage
Shortcomings:
- The solution itself can be rather difficult to get into, and there is definitely a steep learning curve for new users
- The number of different instructions and recommended documentation is extremely low
- Customer support team is knowledgeable, but understaffed, which may sometimes lead to longer wait times
Pricing:
- There is no public information about Quest Recovery Manager’s pricing available on the official website, it seems that the customer would have to contact the company directly and request a quote in order to receive this kind of information
My personal opinion on Quest Recovery Manager:
Quest Recovery Manager is in some respects practically a direct opposite of the previously mentioned NAKIVO. It is created with a single purpose in mind – to protect Active Directory data by either backing it up or restoring it when necessary. Quest’s solution also offers a somewhat rare feature for AD data specifically – a form of incremental backup that constantly monitors AD directory for changes and creates backups of these changes. The overall speed of data recovery is also impressive here, but this particular solution from Quest is only suitable for working with AD data, and nothing else.
MSP360 (formerly Cloudberry Lab)
MSP360 may not be the most familiar name on the market, but its predecessor Cloudberry Lab has been around for quite a while – and MSP360 successfully builds upon that reputation. It is a cross-platform backup and recovery system that can be integrated with plenty of different cloud storage providers, while also offering plenty of backup-related capabilities – file-level backups, image-based backups, DR in cloud, data compression, data encryption, and more.
MSP360’s Active Directory backup and recovery capabilities are relatively basic, with the only option for backup being the image-based backup feature. Since this feature generates the backup of an entire system, it manages to copy the AD database, its transaction logs, as well as the boot volume and the system volume. MSP360’s granular recovery feature also makes it possible to recover specifically the domain controller or specifically the AD database.
Customer ratings:
- Capterra – 4.7/5 stars based on 204 customer reviews
- TrustRadius – 8.1/10 stars based on 45 customer reviews
- G2 – 4.5/5 stars based on 403 customer reviews
Advantages:
- Most of its basic features, such as data backup or data recovery, are easy to work with and user-friendly
- MSP360 is another example of a backup solution that has a reasonably simple initial setup and configuration procedure
- MSP360 acts great as a single centralized management panel for all kinds of data sources, from standard hard drives and servers to VMs, applications, databases, etc.
Shortcomings:
- While there is no public pricing information available on MSP360, many user reviews noted that a lot of features are not included in the base package and have to be purchased separately
- MSP360 is an enterprise-level solution, first and foremost, and while it does technically have support for smaller businesses – most of these businesses would not be able to afford MSP360’s services in the structure they are now
- There is little middle ground when it comes to the reputation of MSP360’s customer support team, with some people singing its praises and others doing the exact opposite, creating an obvious conclusion in the form of an inconsistent customer experience across the board
Pricing:
- MSP360’s pricing information is not publicly available on their official website and the only way to obtain such information is by contacting the company directly for a quote.
- Their special “quote calculator” page allows potential customers to specify what device types they want to be backed up in the future. This particular page allows for three different solution types to be mentioned.
- The first one is MSP360 Managed Backup – a cross-platform backup and recovery solution, this part allows a potential customer to specify how many devices and data sources of specific types they need covered by the solution, including:
- Windows Desktop
- Windows Server
- MS Exchange
- MS SQL Server
- Mac OS Desktop
- Linux Desktop
- Hyper V Server or Server Socket
- VMware Server or Server Socket
- Microsoft SharePoint
- Microsoft Teams
- Microsoft 365
- Google Shared Drives
- Google Workspace
- The second one is MSP360 RMM – a trustworthy endpoint management solution with options such as RMM (priced per administrator), and deep instinct (priced per endpoint)
- The last option is MSP360 Connect – a well-protected remote access solution, it allows for the number of potential remote access devices on either Windows or Mac platform to be specified
- Additionally, a potential customer has the option to mention the need for premium support, onboarding, custom SSL, and advanced rebranding
- After the correct number of options for each data source have been selected, a potential client has to provide additional information about the company in question so that they can be contacted later with a personalized quote.
- It is worth noting that there is no clear separation between pricing tiers of MSP360, which is why AD backup and restore operations can be utilized by any customer that has image-based backup as a feature included in their package
My personal opinion on MSP360:
Businesses get rebranded, purchased or merged on a regular basis and the backup market is no exception. MSP360 is a complex solution with a variety of features, some of which were built upon its predecessor in the form of Cloudberry backup solutions. While some of the features have been improved quite a lot since MSP360s rebranding happened, MSP360 still has its own flaws, such as its very basic AD backup capabilities. The only way to create an AD backup is to perform a complete image-based backup that would include AD data, as well as everything else stored within the same storage unit. Granted, MSP360 does support granular restoration, offering the ability to restore just the AD data if necessary, but the overall approach to AD backups from MSP360 is still rather basic and not particularly flexible.
EaseUS Todo Backup Enterprise
EaseUS is a fairly old company that originates from China and was founded back in 2004. It is a versatile software provider that covers partition management, data recovery, backup operations, video editing, audio recording, and so on. EaseUS Todo Backup specifically is a capable backup and recovery solution that works with desktops, smartphones, and other device types – performing backups, encrypting data, cloning disks, and many other capabilities.
EaseUS Todo Backup also supports Active Directory backups (only in the Enterprise version of the software), providing any user with the ability to perform a hard drive backup or a partition backup. The user would have to find and choose the specific folder or disk to back up manually at first, but it is also possible to automate some parts of the backup process afterwards. The recovery process is also relatively simple, giving the ability to restore the backup to the original location or to choose a different one instead.
Customer ratings:
- Capterra – 4.5/5 stars based on 93 customer reviews
- TrustRadius – 7.8/10 stars based on 12 customer reviews
- G2 – 4.0/5 stars based on 23 customer reviews
Advantages:
- Easy-to-use interface and convenient access to most backup operations
- Granular restoration for all backups boosts versatility of the solution
- EaseUS Todo Backup is relatively cheap, all things considered
Shortcomings:
- An inconvenient approach to attracting more paid users from the free version by displaying frequent pop-ups with upgrade suggestions
- No incremental backup capabilities
- Initial installation and setup may take a while, and the installation executable is rather large
Pricing:
- EaseUS Todo Backup has quite a lot of different approaches to pricing, and their Enterprise version specifically can be purchased in three different ways.
- The first option is to use per-server or per-workstation price calculation, including:
- Workstation backup – $49 for 1 year per workstation
- Server backup – $199 for 1 year per server
- Advanced Server backup – $299 per year per server
- The second option is to use a technician license, including:
- $999 for a single year of free updates, free technician service, and a single license for several devices
- $1,399 for two years of free updates, free technician service, and a single license for multiple devices
- $2,499 for a lifetime’s worth of free updates, free technician service, and a single license for multiple devices
- The last, but not least option is to purchase EaseUS Todo Backup Enterprise as a part of the EaseUS Backup Center – a centralized data management solution purpose-built for managing multiple machines from one place. This subscription may include:
- 1 PC for $59 for 1 year, $79 for 2 years, and $99 for a lifetime’s worth of support and updates
- 1 Server for $199 for 1 year, $299 for 2 years, and $499 for a lifetime’s worth of updates and customer support
- 1 Server w/SQL support, $359 for 1 year, $499 for 2 years, $699 for a lifetime’s worth of updates and support from the company
- All editions of EaseUS Todo Backup Enterprise allow for AD backups to be performed exactly as mentioned above
My personal opinion on EaseUS Todo Backup Enterprise:
EaseUS may be the only solution on this list that actually supports the majority of potential audience types, from enterprises to individual users. The company itself offers a massive number of different solutions to choose from, covering personal home backups, massive enterprise-level backups, and everything in-between. The Backup Enterprise version specifically is the one aimed at businesses and companies, and it can also perform rather basic AD backup tasks – be it a complete system backup or a partial backup that only creates a copy of select partitions. The recovery process is also relatively basic – it is simple, but also lacking pretty much any additional feature that most competitors would have. Very limited scalability.
Acronis Cyber Protect
Acronis is a well-known backup software provider that puts a lot of emphasis on data security as a whole (while also providing backup-related features). It offers an effective and secure backup solution for many different use cases, protecting customer data from all kinds of potential threats, be it malware, software failures, natural disasters, hardware issues, and so on. It can also offer detailed reporting and monitoring, regular backup authenticity check, and some of the most secure data encryption in the field.
Acronis Cyber Protect allows for the AD directory to be backed up from either a physical machine’s storage or from an ESXi virtual machine, the process is similar in both cases (create a backup of the entire machine, with the application backup – Microsoft Active Directory and Volume Shadow Copy Service (VSS) features enabled). Unfortunately, the only way to recover AD backups created with Acronis Cyber Protect is to recover an entire machine that was backed up (from a bootable media or using a web interface).
Customer ratings:
- Capterra – 4.5/5 stars based on 204 customer reviews
- TrustRadius – 7.8/10 stars based on 133 customer reviews
- G2 – 4.3/5 stars based on 668 customer reviews
Advantages:
- One of the best malware protection systems on the market, with AI-based detection capabilities and comprehensive monitoring software
- Acronis Cyber Protect is a versatile backup system that supports integrations with many different workload types, be it workstations, servers, VMs, applications, and more
- Collecting necessary data with Acronis is simple and easy, and can be done with minimal effort whenever necessary
Shortcomings:
- A lot of customers consider the UI of Acronis Cyber Protect to be rather outdated and not particularly straightforward in its logic
- The backup agent of Acronis has quite the appetite – its hardware requirements are surprisingly high, even by this market’s standards
- The same could be said for how Acronis approaches pricing, there may be several different pricing models and solution types, but the average pricing of Acronis is often deemed well above market average, making it unattainable for some SMBs. Conversely, Acronis may not be a good technical fit for large enterprises.
Pricing:
- There are three versions of Acronis Cyber Protect that differ quite a lot in their pricing points – Standard, Advanced, and Backup Advanced (Acronis Cyber Protect – Backup Advanced is an extension of a legacy software called Acronis Cyber Backup, the standard package of this software’s capabilities is now included in Acronis Cyber Protect Standard by default)
- Acronis Cyber Protect Standard and Advanced have their own share of differences, with the Advanced version building upon the Standard version by adding SAN storage snapshots, Acronis ASign, Acronis Notary, tape backup support, Xenserver support, Oracle VM Server support, and more.
- As such, it is fairly normal for the Advanced version to cost more than the Standard one, including:
- From $85/$129 (Standard/Advanced respectively) per one workstation, be it physical or virtual, macOS or Windows
- From $595/$925 (Standard/Advanced respectively) for one server, be it physical or virtual, Linux or Windows
- From $705/$1,175 (Standard/Advanced respectively) per one virtual host, be it Hyper-V or VMware (no limitations on the number of virtual machines per host)
- From $285 for one instance of Microsoft Windows Server Essentials (physical/virtual), includes application backup, only available in Acronis Cyber Protect Standard
- The capabilities of Acronis Cyber Protect – Backup Advanced have a completely different approach to pricing depending on the nature of the backup target:
- From $109 per one workstation, be it physical or virtual, macOS or Windows
- From $779 for one server, be it physical or virtual, Linux or Windows
- From $1,019 per one virtual host, be it Hyper-V or VMware (no limitations on the number of virtual machines per host)
- From $139 for either Microsoft 365 data (across SharePoint Online, Teams, OneDrive for Business or Exchange Online) or Google Workspace data (across Contacts, Calendar, Drive, or Gmail)
- Acronis Cyber Protect – Backup Advanced can offer file-level backups, image-based backups, incremental/differential backups, ransomware protection, vulnerability assessment, group management, AD integration, reports, and more.
- AD backup as a feature is available to most legacy Acronis Cyber Backup 12.5 installments (both subscription-based and perpetual), as well as for the universal Acronis Cyber Protect 15 license, with the biggest limitation being the fact that no workstation-based licenses have access to application-aware backup feature (which is necessary for AD backup)
My personal opinion on Acronis:
Acronis is a well-known backup software provider that puts a lot of emphasis on data security – with data encryption, malware protection, regular authenticity checks, and plenty of other features to work with. Its flagship solution Cyber Protect can also perform AD backups, although they are not what I would call “feature-rich”. While it is true that Acronis can perform AD backups for both physical and virtual domain controllers, both the backup and the recovery processes are just about creating image-based backups of the entire storage unit, which is usually longer and more resource-intensive than just copying the AD directory specifically.
Vembu BDR Suite
Vembu BDR Suite is a proverbial powerhouse of backup-related features, it is a sophisticated backup and recovery solution that boasts an impressively long list of supported storage formats. It can cover physical deployments, virtual machines, endpoints, applications, cloud storage, and even databases. There is also the cloud version of the software (BDR Cloud) that does not have to be deployed in order to work, but also has a limited feature set in comparison with the original.
Vembu’s AD backup capabilities are rather impressive, it offers an image-level agentless and app-aware AD backup for both physical and virtual deployments. The addition of VSS API allows Vembu’s AD backups to remain consistent even if the physical or virtual server in question is currently active. Vembu also provides a choice between granular recovery (individual containers/objects) and complete recovery for AD backups, both of which are performed with an impressive speed.
Customer ratings:
- Capterra – 4.5/5 stars based on 17 customer reviews
- TrustRadius – 8.4/10 stars based on 88 customer reviews
- G2 – 4.2/5 stars based on 130 customer reviews
Advantages:
- The interface of the solution is rather user-friendly and often regarded as easy to work with
- A lot of positive Vembu reviews refer to the customer support experience as extremely positive, stating that all of their issues were resolved extremely fast
- A native Linux version of the software with most of the original’s features is another massive advantage, as well as Vembu’s ability to work with so many different systems in the first place
Shortcomings:
- Vembu BDR Suite is a sophisticated solution that may take some time getting used to all of its features and unique qualities
- Some IT technologies and database types are not supported
- Since there is no feature parity between Linux and Windows versions of the software, the customer support may provide slightly incorrect information at times based on their knowledge of Windows version of the software
- The overall price of the solution is significantly higher than market average, after the last year’s sudden price increase for all pricing plans
Pricing:
- Vembu BDR Suite’s pricing varies quite a lot depending on the target data source, and can be purchased using either a subscription-based model or a perpetual license.
- Subscription-based pricing model includes:
- VM backup – from $18 per year per VM, with support for both Hyper-V and VMware deployments
- Server backup – from $60 per year per server, both Linux and Windows servers are supported
- Application/DB backup – from $60 per year per application/database, can work with SQL, MySQL, and Exchange
- SaaS backup – $12 per year per user, works for Google Workspace and Microsoft 365
- Cloud VM backup – $30 per year per AWS instance
- Endpoint backup – from $15 per year per endpoint, supports Windows and Mac devices
- Alternatively, pricing model based on perpetual licensing includes:
- VMware or Hyper-V backup – from $90 per VM or $432 per CPU socket
- Server backup – from $150 per server, Windows Server version supports file, folder, and image-level backups, while Linux Server version only supports file and folder backups
- Cloud VM backup – $75 per single AWS EC2 instance
- SaaS backup – $30 per user, applies to Google Workspace and Microsoft 365
- Endpoint backup – from $37.5 per endpoint, both Windows and Mac devices can backup files and folders, but only Windows version also supports the image version
- Application/DB backup – $150 per application/database, can work with SQL, MySQL, and MS Exchange
- Vembu’s pricing model can be rather confusing, offering both perpetual licenses and subscriptions, as well as several different subscription “levels” to choose from. However, AD-related functionality and specific features, such as “Instant granular recovery for Microsoft AD” are included in all Vembu versions, even the “Free” version (although this version does have its own limitations)
- A lot more details about Vembu BDR Suite’s pricing can be obtained at the official pricing page.
My personal opinion on Vembu:
Unlike plenty of other well-known names on the market, Vembu puts most of its focus and efforts in a single solution (BDR Suite) that can perform a massive number of different tasks – capable of working with regular storage, virtual storage, endpoints, applications, cloud storage, databases, and more. The only other product that Vembu has is the BDR Cloud solution, which is a simplified version of the full-scale BDR Suite software that operates as a cloud backup service with no deployment requirements. Vembu’s AD backup capabilities are also quite impressive, offering application-aware backups with VSS support that can be performed for both physical and virtual deployments. Both the granular backup/recovery and the complete storage unit backup/recovery options are available and underlined by Vembu’s impressive performance, leading to potentially short backup and recovery times. However, high end enterprise uses may be disappointed with interface limitations and lack of flexibility.
Arcserve Backup
Arcserve Backup may be referred to as Tape Backup in some cases, but it is far more than that. Arcserve Backup uses tape as the primary storage medium in its comprehensive data management solution suitable for multiplatform environments. It can perform backup and restore operations with all machines within the system, no matter how small-scale or large-scale they have to be. Arcserve Backup also serves as a great centralized viewing angle over everything the company has in general, including all storage types, all backups, and more.
Arcserve Backup has several approaches to AD backups. Thanks to its certain level of granularity with backup operations, Arcserve can either create full disk backups, creating a copy of everything including the Active Directory, or it can create a separate backup that only includes the aforementioned Active Directory. The restoration process, on the other hand, is somewhat different from usual, since a user would have to restore the backed up AD to a location different from the original and then restore it back as the main Active Directory location using a dedicated utility.
Customer ratings:
- TrustRadius – 5.4/10 stars based on 49 customer reviews
Key features:
- Capable of meeting even some of the most egregious application-specific requirements, including backup to tape, disk-to-disk-to-tape, backup to disk, and even disk-to-disk-to-cloud
- Can offer plenty of features to work with, including multiplexing, hardware snapshots, multistreaming, virtual tape libraries, and more
- Plenty of smart restore capabilities boost reliability and improve general resilience against disasters
- A centralized access to everything data-related within the company, a great way to improve data management across the board
Pricing:
- Arcserve does not usually reveal any kind of pricing information about its solutions publicly. As such, the only way to receive such information for a company is for that company to request a personalized quote.
My personal opinion on Arcserve:
Arcserve is not a particularly popular or well-known software provider, but it does have its own share of customers – and a variety of different solutions that it can offer. One such solution is Arcserve Backup (or Arcserve Tape Backup), a solution with a rather confusing name, since it is not just about creating tape backups – it is a comprehensive backup solution with plenty of basic enterprise-level backup features. It can perform both image-based backups (with AD included), or just create a backup of an AD data, but restoring these backups is a rather problematic process – a user would have to restore the backup to a different location than the original, and then copy the new data to replace the old data using a specific tool. In addition, some integration issues exist after a recent merger.
Veeam Backup & Replication
Veeam is often considered one of the most popular software providers on this market, with Veeam Backup & Replication being a well-known backup and recovery platform with a lot of interesting features. Not only can it work with virtual machines of any types, it can also protect workstations, servers, applications, and even provide secure cloud storage. Its feature range covers instant file-level recovery, built-in deduplication, and plenty of other capabilities.
Veeam has enough capabilities to offer AD backup and recovery for both virtual and physical environments, but the process for creating these backups differs quite a lot. First of all, creating an AD backup for a virtual environment can be done with Veeam Backup & Replication software, but creating backups of physical environments is different – it is called Veeam Endpoint Backup, and it is highly recommended to use full backup in order to achieve the highest level of data protection while also creating a backup of an AD directory.
Customer ratings:
- Capterra – 4.8/5 stars based on 69 customer reviews
- TrustRadius – 8.8/10 stars based on 1,237 customer reviews
- G2 – 4.6/5 stars based on 387 customer reviews
Advantages:
- Not only the customer support is helpful and efficient, but the community forums are also a great help for many issues or questions
- Most of the basic backup and recovery processes are relatively easy to work with even with little to no prior experience with backup software
- Managing backup and recovery processes is simple and easy with Veeam’s interface thanks to centralization capabilities and other features
Shortcomings:
- The pricing model as a whole got a serious overhaul as of recently and the solution is rather expensive now
- A few specific features of Veeam are somewhat outdated at this point and require a major overhaul
- Troubleshooting errors and other mishaps can be somewhat challenging
- Veeam’s user interface feels outdated to many users, especially when utilized in the context of modern operating systems such as Windows 11
Pricing:
- There’s little to no official information about Veeam’s pricing that is available on the official website. The only way to receive the exact price for everything that your specific company needs is to request a personalized quote.
- What Veeam does have is a pricing calculator page that lets users specify the number of different environments they want covered with Veeam’s solution, as well as the planned subscription period.
- This page can also be used to reveal basic information about Veeam’s pricing, such as:
- Veeam’s subscription can be purchased for at least one year in advance, and up to 5 years, with “multi-year contracts offering additional discounts”
- The workload selection screen offers one field for each of the following workload type: Virtual VM, Cloud VM, Servers, Workstations, M365 Users, NAS/File Shares (TB)
- The “Contact Us” button would not be available if only “NAS/File Shares” part is above zero
- Veeam sells licenses in increment of 5 at once, meaning that at least 5 licenses of one of the aforementioned categories have to be selected
- Protecting five workloads (either Virtual VM, Cloud VM, Server, or Workstation type) for a year costs $642
- “Microsoft 365” category is an exception, it requires at least 10 users to be selected at once, and the starting price for 10 users is $306
- Since there are no different tiers or levels of subscription in Veeam, it would be fair to say that AD backup capabilities are included in all versions of Veeam’s software
My personal opinion on Veeam:
Veeam is well known in the enterprise backup solution market, some might even say that it is the most popular backup solution for this target audience. It may be a solution with a significant focus on virtual machines, but there are also plenty of features for other types of data storage, from workstations to applications or cloud storage. While Veeam does have the ability to back up both virtual and physical AD controller data, the process is slightly different – creating a physical backup is far less convenient, mostly because Veeam claims that the virtual deployment is the future and there is little point in working with physical deployments in the first place. Some data management areas also need improving.
Zmanda
Zmanda is another fairly unusual contender on this list of backup software, offering a highly specialized open-source backup software with plenty of capabilities. Its prime offering is called Amanda Enterprise, a robust data protection solution with a wealth of different integrations and features. It can work with databases, cloud storage, tape storage, disk storage, applications, VMs, file shares, and more. It also supports a good range of different Linux distributions, from Ubuntu and Red Hate to Fedora, CentOS, and even Alma Linux.
Zmanda supports AD domain controller backups and database backups, making it possible for these backups to be restored whenever necessary, be it a software issue, a hardware failure, a natural disaster, etc. Zmanda also supports Authorative Restores for Active Directory, making it far easier to perform disaster recovery at a scale with fewer backup restoration events. An Active Directory backup with Zmanda can also be saved to a variety of different backup storage locations, from cloud to tape.
Key features:
- Zmanda’s AD backups are always consistent with the help of the Volume Shadow Copy Service (VSS)
- Zmanda can offer impressive scalability with no significant impact on performance or price
- Backups can be created and restored in no time, and are always optimized in order to use all of the hardware as efficiently as possible
Pricing:
- Low pricing is one of the biggest selling points of Zmanda, as well as a direct comparison to competition. As such, Zmanda has a fairly simple pricing system that includes:
- $29.99 per physical server per month
- $2.99 per workstation per month
- $5.99 per VM per month
- $20 per 1 TB of cloud storage per month
- Of course, all of these can be mixed and matched in no particular order, and the AD backup feature is included with practically any Zmanda purchase
My personal opinion on Zmanda:
Zmanda is not a particularly popular backup solution, but it is a well-known name in the open source industry since it is based on Amanda – a famous free and open-source enterprise-level backup solution. Zmanda as a company offers an extended version of that software with additional features and a wider range of supported system types. Zmanda’s AD backup capabilities are quite impressive, offering multiple backup storage targets, the ability to restore just AD data in case of a failure, and a choice between granular backup of the AD directory and the image-based backup of the entire storage unit, which is more than most solutions on this list can offer. Beyond Active Directory, Amanda suffers from lack of integration with some of the new virtual and container and database technologies.
Physical and virtual domain controller
There can be two types of domain controllers – virtual and physical, and there is an obvious difference between the two (deployment location). It is easy to notice how not all of the aforementioned solutions support AD backups for both virtual and physical domain controllers.
There can be several reasons for that, including the fact that the physical AD deployment is considered an outdated approach by some. As such, it is highly recommended to know what deployment type your AD is right now, to make sure that the solution you’re about to purchase can work with your system in the first place when it comes to AD backup and restore operations.
Active Directory Backup with Bacula Enterprise
Active Directory runs in a highly redundant architecture by design, and loss of the entire directory normally represents a major site fault. Recovery in this case is often complete rebuilds or bare metal recoveries from backup, and often a separate recovery step for databases and the AD components. Bacula Enterprise’s plugin can provide the DR level backup and recovery tools for these situations, and the Bare Metal Recovery plugin allows recovery of a running system onto which the AD services can be recovered. However, while disaster recovery backups are a great thing to have, they don’t help in the case of mistaken changes or corruptions that cause significant problems to a portion of the directory structure, but shouldn’t require a restore of the entire directory. For example, a careless (or disgruntled) admin could make changes to the permissions of an entire OU causing all manner of problems for the organization.
In this scenario, the solutions may be limited to a very time-consuming and error-prone manual rebuild of the structure, or a restore from backup. This is where the Bacula Enterprise Directory Server plugin can help. The Active Directory backup plugin communicates directly with your Active Directory or LDAP environment using the LDAP network protocol to correctly extract your directory structure and enable backup and recovery at the object level. Objects can even be restored to different locations in the directory tree.
This allows recovery of individual objects as well as the entire directory. Unlike the VSS plugin method, the Directory Server plugin assumes a functioning AD infrastructure has been reinstalled, onto which the backed up AD information will be restored, whereas the VSS plugin is more suited to disaster recovery scenarios. For more information about which plugin will suit your needs, please contact Bacula Systems.
Recovery of Active Directory objects with the Directory Server plugin are easy. Objects look just like files at restore time, and many of the same options work. This image shows an example restore window in bconsole:
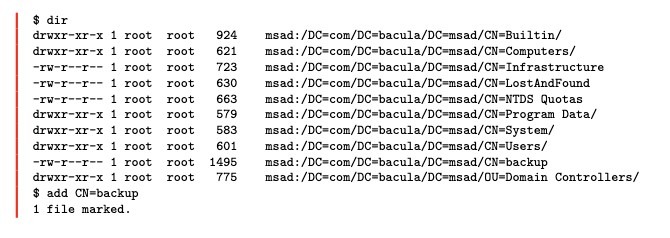
As you can see, we are able to select a single object for recovery and at this point will have access to many restore-time options.
For example, objects can be restored to a different server than they originated from. They can be restored on top of existing objects, and you can choose whether to keep existing objects that are newer than the objects being restore, older, always replace them, or never replace existing objects. You can also have the directory server plugin check for object tombstones, especially useful when restoring objects that have been deleted incorrectly for one reason or another. It’s also possible of course to select the entire directory structure for recovery onto a functioning Active Directory or LDAP server.
Conclusion
The Active Directory is basically at the heart of the business, hence the array of tools and services to prevent any kind of disruption or a memory loss that can at the very least cause downtime for both users and services provided by your business. It’s also important to properly research backup methods and services before applying one of them to your business. Selecting the backup solution that works best for you is the key to preventing most, if not all, of the problems with Active Directory and its’ data.
Active Directory backup is often not the only feature that a company is looking for in a backup solution, and the wealth of choice on this market may sometimes make it quite difficult to pick a single solution. Companies that are looking for a full AD backup support may find NAKIVO or Vembu to be more than suitable for their tastes. Alternatively, users that are looking for a comprehensive backup solution as a whole would be fine with Acronis or Veeam, as well, even though their AD backup capabilities are rather limited.
The ability to recover Active Directory in a disaster is crucial to a good all around risk management strategy for any organization that relies on it heavily. Bacula Enterprise provides very strong tools to both recover from total loss, and also valuable tools to backup Active Directory and recover portions of your infrastructure when things go wrong. It also presents especially high security levels – critical for AD users, and allows for a high level of flexibility and customization where needed. My recommendation – especially for medium to large organizations – is that they explore Bacula’s potential to meet their specialist and high security requirements of AD backup and recovery.



 What is Active Directory?
What is Active Directory?

Hello. Thank you for the up-to-date and useful technical information. In my line of work, I have a lot to do with databases, and backup will be very useful. I will give a task to implement backup system based on Bacula Community to the developers
Hello Albert, sure – you can also look at Bacula Enterprise when your infrastructure grows.