The largest western government and military institutions rely on Bacula, mainly due to the especially high levels of security that it offers.
Move your organization urgently to Bacula’s security levels.
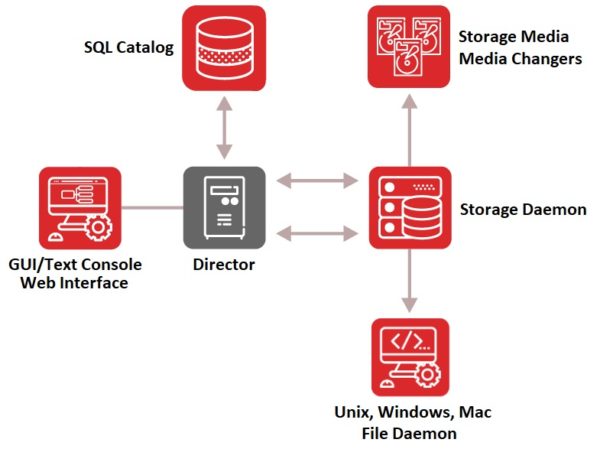
Bacula’s modular architecture does not need, nor allow two way communication between its individual elements. This removes in one stroke the fundamental security vulnerabilities that most of its competitors suffer from. Bacula’s exceptional security qualities are multiplied exponentially by the simple fact that although Bacula can protect practically any data from any operating system, its core engine runs on Linux. As a result, it is significantly more secure than its peers. Finally Bacula’s extreme flexibility to adapt and fit into a user environment without compromise inherently aids that organization’s security, and cannot be underestimated. Contact Bacula now to find out why it is the world leader in Backup and Recovery security levels.