We are thrilled to unveil Bacula Enterprise 18.0.9, the newest standard release.
For comprehensive details, please see the release notes: https://docs.baculasystems.com/BEReleaseNotes/RN18.0/index.html#release-18-0-9-26-august-2025
To access the latest Bacula Enterprise version, please log into the customer portal (https://tickets.baculasystems.com) and select ‘New version 18.0.9!’ located at the top-right corner.
Why Is Ransomware a Critical Threat in Modern Cybersecurity?
Ransomware attacks have been causing major disruptions on numerous organizations for more than a decade now, leading to the loss of critical and sensitive data, among other unfortunate consequences, such as huge amounts of money being paid to criminal organizations. Nearly all major industries are regularly affected by ransomware in some way or another. Ransomware attacks reached 5,263 incidents in 2024 – the highest recorded number since the tracking began back in 2021, and the number in question seems to keep growing on a yearly basis.
While preventive measures remain a key part of ransomware defense, maintaining regular data backups serves as the most effective means of data recovery following an attack. Data protection is paramount: because many forms of ransomware actually target the backed-up data too, necessitating measures to safeguard backups from ransomware is an absolute must. Recent research also shows that attackers attempted to compromise the backups of 94% of organizations hit by ransomware, making backup protection more critical than ever.
Ransomware is a type of malware that infiltrates a victim’s computer or server(s), encrypts their data, and renders it inaccessible. The perpetrators then demand a ransom payment – typically in the form of cryptocurrency – in exchange for the decryption key. Ransomware attacks tend to have devastating consequences, causing significant financial losses, disrupting productivity and even causing bankruptcy. The 2024 Change Healthcare attack (major U.S. healthcare provider) alone resulted in $3.09 billion in damages and compromised the protected health information of over 100 million individuals.
Upon successful encryption of the targeted files, the attackers usually demand a ransom. Ransom payments are often requested in bitcoins or other cryptocurrencies, making them difficult for law enforcement to trace. If the victim fails to comply with the ransom demands, the attackers may resort to further threats, such as publishing the encrypted files online or permanently deleting them.
Who Are the Primary Targets of Ransomware Attacks?
While the statement about practically any device being a potential target for ransomware, there are some categories of information and user groups that ransomware creators tend to target the most:
- Government bodies – primary targets for most ransomware variations due to the sheer amount of sensitive data they hold; it is also a common assumption that the government would rather pay the ransom than let the sensitive data of political significance be released to the public or sold to third parties.
- Healthcare organizations – a notable target for ransomware due to the large number of healthcare infrastructures relying on outdated software and hardware, drastically reducing the amount of effort necessary to break all of its protective measures; healthcare data is also extremely important due to its direct connection with the livelihood of hundreds or thousands of patients, which makes it even more valuable.
- Mobile devices – a common target due to the nature of modern smartphones and the amount of data a single smartphone tends to hold (be it personal videos and photos, financial information, etc.).
- Academic institutions – one of the biggest targets for ransomware, due to the combination of working with large volumes of sensitive data and having smaller IT groups, budget constraints, and other factors that contribute to the overall lower effectiveness of their security systems.
- Human resources departments – may not have a lot of valuable information by themselves but are compensated by having access to both the financial and personal records of other employees; also a common target due to the nature of work itself (opening hundreds of emails per day makes it a lot more likely for an average HR employee to open an email with malware in it).
The number of ransomware attacks seems to be growing at an alarming pace. Financial services organizations saw 65% targeted by ransomware in 2024, with attackers attempting to compromise backups in 90% of these attacks. New ransomware types and variations are also being developed regularly. There is now an entirely new business model called RaaS, or Ransomware-as-a-Service, offering constant access to the newest malicious software examples for a monthly fee, greatly simplifying the overall ransomware attack process.
The latest information from Statista confirms the statements above in terms of the biggest targets for ransomware as a whole – government organizations, healthcare, finance, manufacturing, and so on. Financial organizations also seem to be steadily growing as one of the biggest ransomware targets so far.
There are ways to protect your company against various ransomware attacks, and the first, critical one is to make sure you have ransomware-proof backups.
What Are the Different Types of Ransomware?
Let’s first look at the different types of threats. Encryption-related ransomware (cryptoware) is one of the more widespread types of ransomware in the current day and age. Notable but less widespread examples of ransomware types include:
- Lock screens (interruption with the ransom demand, but with no encryption),
- Mobile device ransomware (cell-phone infection),
- MBR encryption ransomware (infects a part of Microsoft’s file system that is used to boot the computer, preventing the user from accessing the OS in the first place),
- Extortionware/leakware (targets sensitive and compromising data, then demands ransom in exchange for not publishing the targeted data), and so on.
The frequency of ransomware attacks is set to increase dramatically in 2022 and beyond, and with increasing sophistication. Recent data shows that the average ransom payment reached $2.73 million in 2024, a dramatic increase from $400,000 in 2023. This steep escalation reflects both the growing sophistication of attacks and attackers’ improved understanding of victim organizations’ financial capabilities.
While preventive measures are the preferred way to deal with ransomware, they are typically not 100% effective. For attacks that are able to penetrate organizations, backup is their last bastion of defence. Data backup and recovery are proven to be an effective and critical protection element against the threat of ransomware. However, being able to effectively recover data means maintaining a strict data backup schedule and taking various measures to prevent your backup from also being captured and encrypted by ransomware.
For an enterprise to sufficiently protect backups from ransomware, advance preparation and thought is required. Data protection technology, backup best practices and staff training are critical for mitigating the business-threatening disruption that ransomware attacks inflict on an organization’s backup servers.
Double-extortion and data exfiltration
Double-extortion represents the most significant evolution in ransomware tactics over the past five years, fundamentally changing how organizations must approach data protection. Unlike traditional encryption-only attacks where backups provide complete recovery, double-extortion creates liability that persists even after successful restoration.
Attackers now routinely exfiltrate sensitive data during reconnaissance phases – often weeks before deploying encryption payloads. This stolen data becomes permanent leverage. Organizations with perfect backups still face threats of public data dumps, regulatory penalties, competitive intelligence loss, and reputational damage.
Recent high-profile attacks demonstrate this threat: attackers published stolen patient records, customer databases, and proprietary research even after victims refused to pay, causing regulatory fines exceeding tens of millions of dollars. The threat model has fundamentally shifted – ransomware is no longer just an availability attack solved by backups, but a confidentiality breach requiring comprehensive data protection.
Target priorities include:
- customer personally identifiable information (PII)
- financial records
- intellectual property
- employee data
- healthcare records
- any information subject to regulatory protection
Attackers assess data value before selecting victims, specifically targeting organizations holding sensitive information with publication consequences.
Defense requires layering backup strategies with data exfiltration prevention. Data loss prevention (DLP) systems monitor and block unusual data transfers. Network segmentation limits lateral movement between data repositories. Encryption at rest renders stolen files unusable without corresponding keys. Zero-trust architectures verify all access attempts regardless of source.
Backups remain essential for operational recovery but address only half the double-extortion threat. Comprehensive ransomware defense acknowledges that modern attacks create dual risks requiring dual protections – backup resilience for encryption and access controls for exfiltration.
What Are Common Myths About Ransomware and Backups?
If you are researching how to protect backups from ransomware, you might come across wrong or out of date advice. The reality is that ransomware backup protection is a little more complex, so let’s look into some of the most popular myths surrounding the topic.
Ransomware Backup Myth 1: Ransomware doesn’t infect backups. You might think your files are safe. However, not all ransomware activates as you are infected. Some wait before they get started. This means your backups may contain a copy of the ransomware in them.
Ransomware Backup Myth 2: Encrypted backups are protected from ransomware. It doesn’t really matter if your backups are encrypted. As soon as you run a backup recovery, the potential infection becomes executable again and activates.
Ransomware Backup Myth 3: Only Windows is affected. Many people think it is possible to run their backups on a different operating system to eliminate the threat. Unfortunately, if the infected files are hosted on the cloud, the ransomware would cross over.
Ransomware Backup Myth 4: Paying the ransom money is easier and cheaper than investing in data recovery systems. There are two strong arguments against this. Number one – companies that pay the ransom are perceived as vulnerable and unwilling to fight against ransomware attacks. Number two – paying the ransom money in full is not even close to being a guaranteed way to acquire decryption keys.
Ransomware Backup Myth 5: Ransomware attacks are mostly done for the sake of revenge against large enterprises that mistreat regular people. There is a connection that could be made between companies with questionable customer policies and revenge attacks, but the vast majority of attacks are simply looking for anyone to take advantage of.
Ransomware Backup Myth 6: Ransomware does not attack smaller companies and only targets large corporations. While bigger companies might be bigger targets due to a potentially bigger ransom that could be acquired from them, smaller companies are getting attacked by ransomware just as often as bigger ones – and even private users get a significant number of ransomware attacks on a regular basis. A report from Sophos shows that this particular myth is just not true, since both large-scale and small companies have a roughly the same percentage of them being affected by ransomware in a year’s time (72% for enterprises with $5 billion revenue and 58% for businesses with less than $10 million in revenue).
Of course, there are still many ways in which you protect backups from ransomware. Below are some important strategies you should consider for your business.
What Are the Best Methods of Protecting Backups from Ransomware?
Here are some specific technical considerations for your enterprise IT environment, to protect your backup server against future ransomware attacks:
Use Unique, Distinct Credentials
Backup systems require dedicated authentication that exists nowhere else in your infrastructure. Ransomware attacks frequently begin by compromising standard administrative credentials, then using those same credentials to locate and destroy backup repositories. When backup storage shares authentication with production systems, a single credential breach exposes everything.
Access control requirements:
- Enable multi-factor authentication for any human access to backup infrastructure – hardware tokens or authenticator applications provide stronger protection than SMS-based codes
- Implement role-based access control separating backup operators (who execute jobs and monitor completion) from backup administrators (who configure policies and storage)
- Grant minimum required permissions for each function – file read access for backup agents, write access to specific storage locations, nothing more
- Avoid root or Administrator privileges for backup operations, which give ransomware unnecessary system access
Create service accounts exclusively for backup operations with no other system access. These accounts should never log into workstations, email systems, or other applications. Bacula’s architecture enforces this separation by default, running its daemons under dedicated service accounts that operate independently from production workloads.
Monitor authentication logs for backup system access, particularly failed login attempts, access from unusual locations, or credential use outside normal backup windows. Audit privileged actions like retention policy changes or backup deletions – legitimate changes happen infrequently, making unauthorized activity obvious.
Offline storage
Offline storage is one of the best defenses against the propagation of ransomware encryption to the backup storage. There are a number of storage possibilities that are worth mentioning:
| Media Type |
What’s Important |
| Cloud target backups |
These use a different authentication mechanism. Is only partially connected to the backup system. Using cloud target backups is a good way to protect backups from ransomware because your data is kept safe in the cloud. In the case of an attack, you will restore your system from it, although that may prove expensive. You should also keep in mind that syncing with local data storage uploads the infection to your cloud backup too. |
| Primary storage Snapshots |
Snapshots have a different authentication framework and is used for recovery. Snapshot copies are read-only backups, so new ransomware attacks can’t infect them. If you identify a threat, you simply restore it from one taken before the strike took place. |
| Replicated VMs |
Best when controlled by a different authentication framework, such as using different domains for say, vSphere and Hyper-V hosts, and Powered off. You just need to make sure you are keeping careful track of your retention schedule. If a ransomware attack happens and you don’t notice it before your backups are encrypted, you might not have any backups to restore from. |
| Hard drives/SSD |
Detached, unmounted, or offline unless they are being read from, or written to. Some solid-state drives have been cracked open with malware, but this goes beyond the reach of some traditional backup ransomware. |
| Tape |
You can’t get more offline than with tapes which have been unloaded from a tape library. These are also convenient for off-site storage. Since the data is usually kept off-site, tape backups are normally safe from ransomware attacks and natural disasters. Tapes should always be encrypted. |
| Appliances |
Appliances, being black boxes, need to be properly secured against unauthorized access to protect against ransomware attacks. Stricter network security than with regular file servers is advisable, as appliances may have more unexpected vulnerabilities than regular operating systems. |
Backup Copy Jobs
A Backup Copy Job copies existing backup data to another disk system so it is restored later or be sent to an offsite location.
Running a Backup Copy Job is an excellent way to create restore points with retention rules that are different from the regular backup job (and is located on another storage). The backup copy job is a valuable mechanism that helps you protect backups from ransomware because there are different restore points in use with the Backup Copy Job.
For example, if you add an extra storage device to your infrastructure (for instance a Linux server) you would be able to define a repository for it and create a Backup Copy Job to work as your ransomware backup.
Avoid too many file system types
Although involving different protocols is a good way to prevent ransomware propagation, be aware that this is certainly no guarantee against ransomware backup attacks. Different types of ransomware tend to evolve and get more effective on a regular basis, and new types appear quite frequently.
Therefore, it is advisable to use an enterprise-grade approach to security: backup storage should be inaccessible as far as possible, and there should be only one service account on known machines that needs to access them. File system locations used to store backup data should be accessible only by the relevant service accounts to protect all information from ransomware attacks.
Use the 3-2-1-1 rule
Following the 3-2-1 rule means having three distinct copies of your data, on two different media, one of which is off-site. The power of this approach for ransomware backup is that it addresses practically any failure scenario and will not require any specific technologies to be used. In the era of ransomware, Bacula recommends adding a second “1” to the rule; one where one of the media is offline. There are a number of options where you make an offline or semi-offline copy of your data. In practice, whenever you backup to non file system targets, you’re already close to achieving this rule. So, tapes and cloud object storage targets are helpful to you. Putting tapes in a vault after they are written is a long-standing best practice.
Cloud storage targets act as semi-offline storage from a backup perspective. The data is not on-site, and access to it requires custom protocols and secondary authentication. Some cloud providers allow objects to be set in an immutable state, which would satisfy the requirement to prevent them from being damaged by an attacker. As with any cloud implementation, a certain amount of reliability and security risk is accepted by trusting the cloud provider with critical data, but as a secondary backup source the cloud is very compelling.
Verify backup integrity (the 3-2-1-1-0 rule)
The modern 3-2-1-1-0 rule extends traditional backup practices with a critical fifth component: zero errors. This principle emphasizes that backups are only valuable if their successful restoration is guaranteed when needed. The “0” represents verified, error-free backups that have been tested and proven restorable.
Many organizations discover too late that their backups are corrupted, incomplete, or impossible to restore. Ransomware sometimes lies dormant in backup copies for weeks or months before activation, making regular verification essential. Without systematic testing, you may have multiple copies of unusable data rather than functional backups.
Implementing the zero-errors principle requires several practices:
- Automated integrity checks should run after each backup job, verifying checksums and file integrity. These checks catch corruption immediately rather than during a crisis recovery situation.
- Regular restoration testing means periodically restoring data from all backup sources to confirm the process works end-to-end. Test restores should cover different scenarios: individual files, entire systems, and full disaster recovery situations.
- Bandwidth and performance verification ensures your infrastructure will be able to handle full-capacity restores within your recovery time objectives. A backup that takes three weeks to restore may be technically intact but operationally useless.
- Documentation of recovery procedures should be maintained and updated with each test, ensuring staff would still be able to successfully execute recoveries under pressure.
Schedule comprehensive recovery drills quarterly at minimum, testing backups from different time periods and storage locations. Measure and document your actual recovery time objectives (RTO) and recovery point objectives (RPO) during these drills, comparing them against your business requirements. This practice transforms theoretical backup protection into proven, reliable data recovery capability.
Avoid storage snapshots
Storage snapshots are useful to recover deleted files to a point in time, but aren’t backup in the true sense. Storage snapshots tend to lack advanced retention management, reporting, and all the data is still stored on the same system and therefore may be vulnerable to any attack that affects the primary data. A snapshot is no more than a point in time copy of your data. As such, the backup is still vulnerable to ransomware attacks if these were programmed to lie dormant until a certain moment.
Bare metal recovery
Bare metal recovery is accomplished in many different ways. Many enterprises simply deploy a standard image, provision software, and then restore data and/or user preferences. In many cases, all data is already stored remotely and the system itself is largely unimportant. However, in others this is not a practical approach and the ability to completely restore a machine to a point in time is a critical function of the disaster recovery implementation that allows you to protect backups from ransomware.
The ability to restore a ransomware-encrypted computer to a recent point in time, including any user data stored locally, may be a necessary part of a layered defense. The same approach is applied to virtualized systems, although there are usually preferable options available at the hypervisor.
Backup plan testing
Testing backup and recovery procedures transforms theoretical protection into proven capability. Organizations that discover backup failures during actual ransomware incidents face catastrophic data loss and extended downtime. Regular testing identifies problems before emergencies occur.
Establish a structured testing schedule based on data criticality. Test mission-critical systems monthly, important systems quarterly, and standard systems semi-annually. Each test validates different recovery scenarios to ensure comprehensive coverage.
Recovery scenarios to test regularly:
- File-level restoration – Recover individual files and folders from various dates to verify granular recovery capabilities
- System-level restoration – Restore complete servers, databases, or virtual machines to confirm full system recovery
- Bare metal recovery – Rebuild systems from scratch on new hardware to validate disaster recovery procedures
- Cross-platform recovery – Test restoration to different hardware or virtualized environments
- Partial recovery – Restore specific application components or database tables to verify selective recovery options
Document Recovery Time Objective (RTO) and Recovery Point Objective (RPO) for each system during testing. RTO measures how quickly you restore operations – the time between failure and full recovery. RPO measures potential data loss – the time between the last backup and the failure event. Compare actual results against business requirements and adjust backup frequencies or infrastructure accordingly.
Verify bandwidth capacity handles full-scale restores within your RTO targets. A backup system that requires three weeks to restore terabytes of data fails operationally despite technical integrity. Test restoration over production networks during business hours to identify realistic performance constraints.
Maintain detailed documentation of each test including procedures followed, time required, problems encountered, and corrective actions taken. Update runbooks based on test findings to ensure staff execute recoveries efficiently during actual incidents. Rotate testing responsibilities among team members to prevent single points of knowledge failure.
Monitoring, alerting and anomaly detection
Continuous monitoring detects ransomware attacks in progress before they destroy backup infrastructure. Attackers typically spend hours or days reconnaissance mapping backup systems, attempting credential access, and testing deletion capabilities before launching full-scale attacks. Monitoring is needed to catch these reconnaissance activities early.
Critical events requiring immediate alerts:
- Failed authentication attempts to backup systems, especially multiple failures from single sources
- Backup deletion requests or retention policy modifications outside change windows
- Unusual backup sizes – dramatic increases suggest data exfiltration, significant decreases indicate corruption or tampering
- Backup job failures across multiple systems simultaneously, signaling coordinated attacks
- Access to backup storage from unauthorized IP addresses or geographic locations
- Encryption key access outside scheduled backup operations
Configure anomaly detection baselines by measuring normal backup patterns over 30-day periods. Establish typical backup sizes, completion times, and access patterns for each system. Integrate backup system logs with Security Information and Event Management (SIEM) platforms for unified visibility. Automate response to critical alerts where possible. Review monitoring data weekly even without alerts.
Immutable storage
Modern ransomware actively seeks and destroys backups before encrypting primary data. Immutable storage counters this threat by creating backup copies that cannot be modified, deleted, or encrypted once written – even by administrators with full system access.
WORM (Write-Once-Read-Many) technology represents the most robust implementation of immutability. When data is stored in WORM format, it becomes permanently locked for a specified retention period. Ransomware that compromises administrator credentials cannot override these protections, making WORM storage immune to credential-based attacks.
Cloud providers offer object-level immutability through services like Amazon S3 Object Lock, Azure Immutable Blob Storage, and Google Cloud Storage Retention Policies. These services lock objects at the API level, preventing deletion or modification requests from any user or application. Configuration requires enabling immutability at the bucket or container level before writing backup data.
Hardware-based WORM solutions include specialized tape libraries and appliances with firmware-enforced write protection. These devices reject modification commands at the hardware level, providing protection independent of software vulnerabilities.
Implementation steps for immutable backups:
- Configure backup software to write to immutable targets immediately after backup completion
- Set retention periods that exceed your longest potential ransomware dormancy period – typically 90 to 180 days based on current threat patterns
- Separate authentication systems for immutable storage from production environments using dedicated service accounts with write-only permissions
- Layer immutable storage with standard backup infrastructure rather than replacing it – immutable copies serve as the final recovery option
- Monitor for unauthorized access attempts and failed deletion requests, which signal active attacks
- Verify that immutability settings remain enforced after system updates
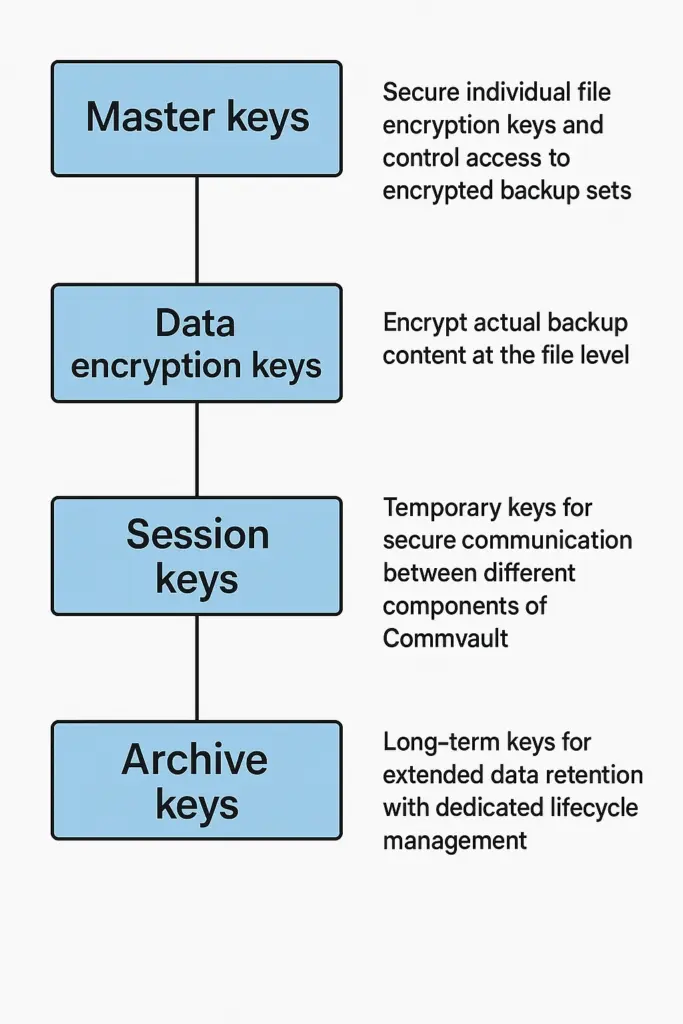
Backup encryption
Encryption protects backup data from unauthorized access and prevents attackers from exploiting stolen backups in double-extortion schemes. Modern ransomware groups increasingly exfiltrate data before encryption, threatening to publish sensitive information unless victims pay additional ransoms. Encrypted backups render stolen data unusable to attackers.
Implement encryption at two critical points:
- data at rest (stored backups)
- data in transit (during backup and restore operations)
AES-256 encryption provides industry-standard protection for stored backup data, offering effectively unbreakable security with current technology. TLS 1.2 or higher secures data moving between backup clients and storage targets, preventing interception during transmission.
Key management practices:
- Store encryption keys separately from backup data – keys stored alongside encrypted backups provide no protection if attackers compromise the storage system
- Use dedicated key management systems (KMS) or hardware security modules (HSMs) that provide tamper-resistant key storage and access logging
- Implement role-based access controls limiting key access to authorized backup administrators only
- Rotate encryption keys annually or after any suspected security incident
- Maintain secure offline copies of encryption keys in physically separate locations – losing keys means permanent data loss regardless of backup integrity
- Document key recovery procedures and test them regularly to ensure keys remain accessible during disasters
- Enable multi-factor authentication for all key management system access
Separate key management credentials from backup system credentials. Attackers who compromise backup administrator accounts should not automatically gain encryption key access. This separation creates an additional barrier requiring attackers to breach multiple authentication systems.
For organizations subject to regulatory requirements, encryption addresses compliance mandates including GDPR, HIPAA, and PCI-DSS. These frameworks require encryption of sensitive data at rest and in transit, making backup encryption legally mandatory rather than optional for regulated industries.
Monitor encryption key access logs for unusual activity. Unexpected key retrieval attempts signal potential attacks attempting to decrypt backup data for exfiltration or sabotage.
Backup policies
Reviewing and updating your anti-ransomware backup policies on a regular basis is a notably effective method of minimizing the effect of a ransomware attack or straight-up preventing it. For the backup policy to be effective in the first place – it has to be up-to-date and flexible, including solutions for all of the modern ransomware attack methods.
One of the best defenses against ransomware is a restoration of information from clean backups, since paying a ransom is not a 100% guarantee of your data being decrypted in the first place – signifying the importance of backups once again. Topics that have to be covered when performing a thorough audit of your entire internal data structure include:
- Is the 3-2-1 rule in place?
- Are there any critical systems that are not covered by regular backup operations?
- Are those backups properly isolated so that they are not affected by ransomware?
- Was there ever a practice run of a system being restored from a backup to test how it works?
Disaster recovery planning
A Disaster Recovery Plan (DRP) outlines how your organization responds to threats including ransomware, hardware failures, natural disasters, and human errors. Effective DRPs establish clear procedures before incidents occur, eliminating confusion during high-stress response situations.
Recovery objectives framework:
Recovery Point Objective (RPO) defines acceptable data loss measured in time – how much data you would be able to afford to lose. Recovery Time Objective (RTO) defines acceptable downtime how quickly you must restore operations. Set these targets based on business impact:
- Mission-critical systems (financial transactions, patient records): RPO of 15 minutes to 1 hour, RTO of 1-4 hours
- Important business systems (email, CRM, project management): RPO of 4-8 hours, RTO of 8-24 hours
- Standard systems (file servers, archives): RPO of 24 hours, RTO of 48-72 hours
Backup frequency and infrastructure must support these targets. Systems with 15-minute RPO require continuous replication or frequent snapshots, not daily backups.
Ransomware incident response procedures:
- Isolate affected systems immediately – Disconnect compromised devices from networks to prevent ransomware spread, but leave systems powered on to preserve evidence
- Activate incident response team – Assign roles: incident commander, technical lead, communications coordinator, legal liaison
- Assess scope – Identify all compromised systems, determine ransomware variant, check if backups are affected
- Preserve evidence – Capture memory dumps, logs, and system states before remediation for potential law enforcement involvement
- Verify backup integrity – Test restoration from multiple backup generations to confirm clean recovery points exist
- Execute recovery – Restore from the most recent clean backup, rebuild compromised systems, implement additional security controls before reconnecting to production
Document ransomware payment decisions in advance. Establish criteria for when payment might be considered (life safety systems, no viable backups) versus firm refusal policies. Never negotiate without legal counsel and law enforcement coordination.
Security-centric education for employees
Backups are conducted on both system-wide levels and on individual employee systems, especially when it comes to various emails and other specific info. Teaching your employees about the importance of their participation in the backup process is a great way to close even more gaps in your defense against ransomware.
At the same time, while regular employees help with the backup process, they should not have access to backups themselves whatsoever. The more people have access to backed-up data – the higher the chances are for human error or some other way for your system and your backups to be compromised.
Infrastructure Hardening and Endpoint Protection
Ransomware exploits vulnerabilities in systems to gain initial access and spread laterally through networks. Comprehensive infrastructure hardening closes these entry points and limits attacker movement even when perimeter defenses fail.
Patch management forms the foundation of infrastructure security. Establish automated patch deployment for operating systems, applications, and firmware within 72 hours of release for critical vulnerabilities. Prioritize patches addressing known ransomware exploits and remote code execution flaws. Maintain an inventory of all systems to ensure nothing falls through patching gaps.
Endpoint detection and response (EDR) solutions provide real-time monitoring and threat detection on workstations and servers. EDR tools identify ransomware behavior patterns – such as rapid file encryption, unusual process execution, or attempts to delete shadow copies – and automatically isolate infected endpoints before ransomware spreads. Deploy EDR across all endpoints including backup servers and administrative workstations.
Attack surface reduction eliminates unnecessary access points. Each removed service or closed port represents one less vulnerability for attackers to exploit. As such, disable unused services, close unnecessary network ports, remove legacy protocols, and uninstall software that poses security risks. Also implement application whitelisting to prevent unauthorized executables from running.
Vulnerability scanning identifies security gaps before attackers do. Schedule weekly automated scans of all systems, prioritizing remediation based on exploit likelihood and potential impact. Pay particular attention to backup infrastructure, storage systems, and authentication servers – the high-value targets in ransomware campaigns.
Security awareness training addresses the human element. Train employees to recognize phishing attempts, suspicious attachments, and social engineering tactics quarterly. Simulated phishing exercises identify users requiring additional training. Email and phishing attacks accounted for 52.3% of ransomware incidents in 2024, making employee vigilance critical.
Regular infrastructure hardening audits verify that security configurations remain enforced. Systems drift from secure baselines over time through legitimate changes and misconfigurations – periodic audits catch these deviations before attackers exploit them.
Air gapping
Air-gapped backups provide physical isolation that makes them unreachable through network-based attacks. This approach physically disconnects backup storage from all networks, cloud infrastructure, and connectivity during non-backup periods, creating an absolute barrier against remote ransomware infiltration.
Ransomware spreads through network connections, scanning for accessible storage and backup repositories. Air-gapped storage eliminates this attack vector entirely – if the storage device has no network connection, ransomware would not be able to reach it regardless of credential compromise or zero-day exploits.
Implementing air-gapped backups:
- Use removable storage devices such as external hard drives, NAS appliances, or tape media
- Connect devices to backup systems only during scheduled backup windows, then physically disconnect immediately after completion
- Establish a rotation schedule with multiple storage devices – while one device captures the current backup, previous devices remain completely offline in secure physical locations
- Store disconnected devices in separate physical locations from primary infrastructure to protect against both ransomware and physical disasters
- Configure backups as full copies rather than incremental chains (chain-free backups) that depend on previous generations – this allows recovery from any single device without requiring access to other backup versions
- Automate disconnection using programmatically controlled tape libraries or storage arrays where possible to reduce human error
- Document reconnection procedures thoroughly for high-stress incident response situations
Air-gapped backups suit organizations with defined backup windows and recovery time objectives measured in hours rather than minutes. Real-time applications requiring instant failover need supplementary protection through replicated systems or immutable cloud storage.
Configure backups as full copies rather than incremental chains that depend on previous backups. Chain-free backups allow recovery from any single air-gapped device without requiring access to other backup generations. If ransomware compromises your incremental backup chain, chain-free archives remain independently recoverable.
Amazon S3 Object Lock
Object Lock is a feature of Amazon cloud storage that allows for enhanced protection of information stored within S3 buckets. The feature, as its name suggests, prevents any unauthorized action with a specific object or set of objects for a specific time period, making data practically immutable for a set time frame.
One of the biggest use cases for Object Lock is compliance with various frameworks and compliance regulations, but it is also a useful feature for general data protection efforts. It is also relatively simple to set up – all that is needed is for the end user to choose a Retention Period, effectively turning the data into WORM format for the time being.
There are two main retention modes that S3 Object Lock offers – Compliance mode and Governance mode. The Compliance mode is the least strict of the two, offering the ability to modify the retention mode while the data is “locked”. The Governance mode, on the other hand, prevents most users from tampering with data in any way whatsoever – the only users that are permitted to do anything with the data during the retention time frame are the ones that have special bypass permissions.
It is also possible to use Object Lock to turn on a “Legal Hold” on specific data, it works outside of retention periods and retention mods and prevents the data in question from being tampered with for legal reasons such as litigation.
Zero Trust Security
An ongoing shift from traditional security to data-centric security has introduced many new technologies that offer incredible security benefits, even if there is a price to pay in terms of user experience. For example, a zero-trust security approach is a relatively common tactic for modern security systems, serving as a great protective barrier from ransomware and other potential threats.
The overall zero-trust security approach adopts the main idea of data-centric security, attempting to verify and check all users and devices accessing specific information, no matter what they are and where they are located. This kind of approach focuses on four main “pillars”:
- The principle of least privilege provides each user with as few privileges in the system as possible, trying to mitigate the problem of over privileged access that most industries had for years.
- Extensive segmentation is mostly used to limit the scope of a potential security breach, eliminating the possibility of a single attacker acquiring access to the entire system at once.
- Constant verification is a core principle for zero-trust security, without any kind of “trusted users” list that is used to bypass the security system altogether.
- Ongoing monitoring is also a necessity to make sure that all users are legitimate and real, in case some form of a modern attack program or a bad actor succeeds in bypassing the first layer of security.
Network segmentation for backup infrastructure
Isolating backup systems from production networks prevents ransomware from moving laterally between compromised workstations and backup repositories. When backup infrastructure shares network space with endpoints and servers, attackers use the same pathways to reach both targets.
Deploy backup systems on dedicated network segments using separate VLANs or physical subnets. Configure firewall rules allowing only necessary backup traffic between production and backup networks – typically limited to backup agents initiating connections to backup servers on specific ports. Block all other traffic, particularly production-to-backup administrative protocols like RDP or SSH.
Use separate Active Directory domains or forests for backup infrastructure authentication. Production domain compromise frequently gives attackers enterprise-wide access including backup systems when both share authentication infrastructure. Separate domains require attackers to breach multiple authentication systems independently.
Implement jump hosts or bastion servers as the sole entry point for backup system administration. Administrators connect to the jump host first, then access backup infrastructure from there. This architecture creates a monitored chokepoint for all administrative access and prevents direct connections from potentially compromised workstations.
Network isolation checklist:
- Dedicated VLANs or subnets for backup servers and storage
- Firewall rules restricting backup traffic to necessary ports and directions only
- Separate authentication domains for backup infrastructure
- Jump host requirement for all backup system administration
- Network access control (NAC) preventing unauthorized devices from reaching backup segments
- Regular firewall rule audits removing unnecessary access permissions
How Would Backup System Tools Provide Additional Ransomware Protection?
Going for an augmented approach to the same problem of ransomware-infected backup, it is possible – and advisable – to use backup systems’ tools as an additional means of protecting against attack. Here are five ransomware backup best practises – to further protect a business against ransomware:
- Make sure that backups themselves are clean of ransomware and/or malware. Checking that your backup is not infected should be one of your highest priorities, since the entire usefulness backup as a ransomware protection measure is negated if your backups are compromised by ransomware. Perform regular system patching to close off vulnerabilities in the software, invest in malware detection tools and update them regularly, and try to take your media files offline as fast as possible after changing them. In some cases, you might consider a WORM approach (Write-One-Read-Many) to protect your backups from ransomware – a specific type of media that is only provided for certain tape and optical disk types, as well as a few cloud storage providers.
- Do not rely on cloud backups as the only backup storage type. While cloud storage has a number of advantages, it is not completely impervious to ransomware. While harder for an attacker to corrupt data physically, it is still possible for ransomware attackers to gain access to your data either using a shared infrastructure of the cloud storage as a whole, or by connecting said cloud storage to an infected customer’s device.
- Review and test your existing recovery and backup plans. Your backup and recovery plan should be tested on a regular basis to ensure you’re protected against threats. Finding out that your recovery plan is not working as intended only after a ransomware attack is clearly undesirable. The best ransomware backup strategy is the one that will never have to deal with malicious data breaches. Work through several different scenarios, time-check some of your restoration-related results such as time-to-recovery, and establish which parts of the system are prioritized by default. Remember, many businesses measure the cost of services being down in dollars-per-minute and not any other metric.
- Clarify or update retention policies and develop backup schedules. A regular review of your ransomware backup strategies is strongly recommended. It may be that your data is not backed up often enough, or that your backup retention period is too small, making your system vulnerable to more advanced types of ransomware that target backup copies via time delays and other means of infection.
- Thoroughly audit all of your data storage locations. To protect backups from ransomware, these should be audited to be sure that no data is lost and everything is backed up properly – possibly including end-user systems, cloud storages, applications and other system software.
How Does Ransomware Target and Compromise Your Backups?
While it is true that backup and recovery systems are capable of protecting organizations against ransomware in most cases, these systems are not the only ones that keep progressing and evolving over the years – because ransomware also gets more and more unusual and sophisticated as the time passes.
One of the more recent problems of this whole approach with backups is that now a lot of ransomware variations have learned to target and attack not only the company’s data in the first place, but also the backups of that same company – and this is a significant problem for the entire industry. Many ransomware writers have modified their malware to track down and eliminate backups. From this perspective, while backups still protect your data against ransomware – you will also have to protect backups from ransomware, too.
It is possible to figure out some of the main angles that are typically used to tamper with your backups as a whole. We will highlight the main ones and explain how you use them to protect backups from ransomware:
Ransomware damage potential increase with longer recovery cycles
While not as obvious as other possibilities, the problem of long recovery cycles is still a rather big one in the industry, and it’s mostly caused by outdated backup products that only perform slow full backups. In these cases, recovery cycles after ransomware attack take days, or even weeks – and it’s a severe disruption for the majority of companies, as system downtime and production halt costs quickly overshadow initial ransomware damage estimates.
Two possible solutions here to help protect your backups from ransomware would be: a) to try and get a solution that provides you a copy of your entire system as quickly as possible, so you don’t have to spend days or even weeks in recovery mode, and b) to try and get a solution that offers mass restore as a feature, getting multiple VMs, databases and servers up and running again very quickly.
Your insurance policy may also become your liability
As we have mentioned before, more and more ransomware variations appear that target both your original data and your backups, or sometimes even try to infect and/or destroy your backed up data before moving to its source. So you need to make it as hard as possible for ransomware to eliminate all of your backup copies – a multi-layered defense, of sorts.
Cybercriminals are using very sophisticated attacks that target data, going straight for your backups as that’s your main insurance policy to keep your business running. You should have a single copy of the data in such a state that it is never mounted by any external system (often referred to as an immutable backup copy), and implement various comprehensive security features, like the aforementioned WORM, as well as modern data isolation, data encryption, tamper detection and monitoring for data behavior abnormality.
There are two measures here that we will go over in a bit more detail:
- Immutable backup copy. Immutable backup copy is one of the bigger measures against ransomware attacks – it’s a copy of your backup that cannot be altered in any way once you’ve created it. It exists solely to be your main source of data if you have been targeted by ransomware and need your information back as it was before. Immutable backups cannot be deleted, changed, overwritten, or modified in any other way – only copied to other sources. Some vendors pitch immutability as foolproof – but in terms of ransomware backup, there is no such thing. But you should not fear immutable backup ransomware attacks. Just ensure you have a comprehensive strategy that includes attack detection and prevention, and implement strong credential management.
- Backup encryption. It is somewhat ironic that encryption is also used as one of the measures to counter ransomware attacks – since a lot of ransomware uses encryption to demand ransom for your data. Encryption doesn’t make your backups ransomware-proof, and it won’t prevent exploits. However, in its core, backup encryption is supposed to act as one more measure against ransomware, encrypting your data within backups so that ransomware cannot read or modify it in the first place.
Visibility issues of your data become an advantage for ransomware
By its nature, ransomware is at its most dangerous when it gets into a poorly managed infrastructure – “dark data”, of sorts. In there, it does a lot of damage, a ransomware attack encrypts your data and/or sells it on the dark web. This is a significant problem that requires the most cutting-edge technologies to detect and combat effectively.
While early detection of ransomware is possible with only a modern data management solution and a good backup system, detecting such threats in real-time requires a combination of machine learning and artificial intelligence – so that you receive alerts about suspicious ransomware activity in real-time, making attack discovery that much faster.
Data fragmentation is a serious vulnerability
Clearly, a lot of organizations deal with large amounts of data on a regular basis. However, the size is not as much of a problem as fragmentation – it’s not uncommon for one company’s data to be located in multiple different locations and using a number of different storage types. Fragmentation also creates large caches of secondary data (not always essential to business operations) that affect your storage capabilities and make you more vulnerable.
Each of these locations and backup types are adding another potential venue for ransomware to exploit your data – making the entire company’s system even harder to protect in the first place. In this case it is a good recommendation to have a data discovery solution working within your system which brings many different benefits – one of which is better visibility for the entirety of your data, making it far easier to spot threats, unusual activity and potential vulnerabilities.
User credentials are used multiple times for ransomware attacks
User credentials have always been one of the biggest problems in this field, providing ransomware attackers with clear access to valuable data within your company – and not all companies are capable of detecting the theft in the first place. If your user credentials become compromised, ransomware attackers leverage the different open ports and gain access to your devices and applications. The entire situation with user credentials became worse when, because of Covid, businesses were forced to largely switch to remote work around in 2019 – and this problem is still as present as ever.
These vulnerabilities even affect your backups and leave them more exposed to ransomware. Typically the only way to combat this kind of gap in security is to invest into strict user access controls – including features such as multi-factor authentication, role-based access controls, constant monitoring, and so on.
Always test and re-test your backups
Many companies only realize their backups have failed or are too difficult to recover only after they have fallen victim to a ransomware attack. If you want to ensure your data is protected, you should always do some kind of regular exercise and document the exact steps for creating and restoring your backups.
Because some types of ransomware also remain dormant before encrypting your information, it’s worth testing all your backup copies regularly – as you might not know when precisely the infection took place. Remember that ransomware will only continue to find more complex ways to hide and make your backup recovery efforts more costly.
Conclusion
For maximum protection of your backup against ransomware and similar threats, Bacula Systems’ strong advice is that your organization fully complies with the data backup and recovery best practices listed above. The methods and tools outlined in this blog post are used by Bacula’s customers on a regular basis to successfully protect their backups from ransomware. For companies without advanced-level data backup solutions, Bacula urges these organizations to conduct a full review of their backup strategy and evaluate a modern backup and recovery solution. Bacula is generally acknowledged in the industry to have exceptionally high levels of security in its backup software. Contact Bacula now for more information.
Key Takeaways
- Modern ransomware attacks target backup systems in most cases, making backup protection as critical as protecting production data
- Implement the 3-2-1-1-0 rule with three copies of data on two media types, one off-site, one immutable or offline, and zero errors through regular verification and recovery testing
- Immutable storage using WORM technology and air-gapped backups create multiple defense layers that prevent attackers from deleting or encrypting backup copies even with compromised administrator credentials
- Separate backup infrastructure from production networks using dedicated VLANs, distinct authentication domains, and strict access controls with multi-factor authentication to prevent lateral ransomware movement
- Double-extortion tactics mean backups alone cannot protect against data theft and publication threats—organizations need comprehensive strategies including encryption, data loss prevention, and network segmentation
- Regular recovery testing with documented RTO and RPO metrics transforms theoretical backup protection into proven capability, while continuous monitoring detects reconnaissance activities before attackers destroy backup infrastructure
Download Bacula’s white paper on ransomware protection
What is High Performance Computing Security and Why Does It Matter?
High Performance Computing (HPC) is a critical infrastructure backbone for scientific discovery, artificial intelligence advancement, and national economic competitiveness. As these systems process increasingly sensitive research data and support mission-critical computational workloads, traditional enterprise security approaches fall short of addressing the unique challenges inherent in HPC environments. Knowing how to work with these fundamental differences is essential for implementing effective security measures that protect valuable computational resources without compromising overall productivity.
High Performance Computing refers to the practice of using supercomputers and parallel processing techniques to solve highly complex computational problems that demand enormous processing power. These systems typically feature thousands of interconnected processors, specialized accelerators like GPUs, and high-speed networking infrastructure capable of performing quadrillions of calculations per second. HPC systems support critical applications across a multitude of domains:
- Scientific research and modeling – Climate simulation, drug discovery, nuclear physics, and materials science
- Artificial intelligence and machine learning – Training large language models, computer vision, and deep learning research
- Engineering and design – Computational fluid dynamics, structural analysis, and product optimization
- Financial modeling – Risk analysis, algorithmic trading, and economic forecasting
- National security applications – Cryptographic research, defense modeling, and intelligence analysis
The security implications of HPC systems extend far beyond typical IT infrastructure concerns. A successful attack on an HPC facility could result in intellectual property theft worth billions of dollars – compromising sensitive research data, disrupting critical scientific programs, or even being classified as national security breaches.
Why HPC Security Standards and Architecture Matter in Modern Facilities
HPC security differs fundamentally from enterprise IT through architectural complexity and performance-first design. Unlike conventional business infrastructure, HPC systems prioritize raw computational performance while managing hundreds of thousands of components, creating expanded attack surfaces difficult to monitor comprehensively. Traditional security tools cannot handle the volume and velocity of HPC operations, while performance-sensitive workloads make standard security controls like real-time malware scanning potentially destructive to petabyte-scale operations.
Before NIST SP 800-223 and SP 800-234, organizations lacked comprehensive, standardized guidance tailored to HPC environments. Now, these complementary standards address this knowledge gap using a foundational four-zone reference architecture that acknowledges distinct security requirements across access points, management systems, compute resources, and data storage. It even documents HPC-specific attack scenarios such as credential harvesting and supply chain attacks.
Real-world facilities exemplify these challenges. Oak Ridge National Laboratory systems contain hundreds of thousands of compute cores and exabyte-scale storage while balancing multi-mission requirements supporting unclassified research, sensitive projects, and classified applications. They accommodate international collaboration and dynamic software environments that traditional enterprise security approaches cannot effectively address.
The multi-tenancy model creates additional complexity as HPC users require direct system access, custom software compilation, and arbitrary code execution capabilities. This demands security boundaries balancing research flexibility with protection requirements across specialized ecosystems including scientific libraries, research codes, and package managers with hundreds of dependencies.
How Do We Understand HPC Security Architecture and Threats?
HPC security requires a fundamental shift in perspective from traditional enterprise security models. The unique architectural complexity and threat landscape of high-performance computing environments demand specialized frameworks that acknowledge the existing tensions between computational performance and security controls.
NIST SP 800-223 provides the architectural foundation by establishing a four-zone reference model that recognizes the distinct security requirements across different HPC system components. This zoned approach acknowledges that blanket security policies are not effective enough when it comes to addressing the varying threat landscapes and operational requirements found in access points, management systems, compute resources, and data storage infrastructure.
The complementary relationship between NIST SP 800-223 and SP 800-234 creates a comprehensive security framework specifically tailored for HPC environments. Here, SP 800-223 defines the architectural structure and identifies key threat scenarios, while SP 800-234 provides detailed implementation guidance through security control overlays that adapt existing frameworks to HPC-specific operational context.
A dual-standard approach like this addresses critical gaps in HPC security guidance by providing both conceptual architecture and practical implementation details. With it, organizations move beyond adapting inadequate enterprise security frameworks to implementing purpose-built security measures that protect computational resources without compromising research productivity or scientific discovery missions.
What Does NIST SP 800-223 Establish for HPC Security Architecture?
NIST SP 800-223 provides the foundational architectural framework that transforms HPC security from ad-hoc implementations to structured, zone-based protection strategies. This standard introduces a systematic approach to securing complex HPC environments while maintaining the performance characteristics essential for scientific computing and research operations.
How Does the Four-Zone Reference Architecture Work?
The four-zone architecture recognizes that different HPC components require distinct security approaches based on their operational roles, threat exposure, and performance requirements. This zoned model replaces one-size-fits-all security policies with targeted protections that acknowledge the unique characteristics of each functional area.
| Zone |
Primary Components |
Security Focus |
Key Challenges |
| Access Zone |
Login nodes, data transfer nodes, web portals |
Authentication, session management, external threat protection |
Direct internet exposure, high-volume data transfers |
| Management Zone |
System administration, job schedulers, configuration management |
Privileged access controls, configuration integrity |
Elevated privilege protection, system-wide impact potential |
| Computing Zone |
Compute nodes, accelerators, high-speed networks |
Resource isolation, performance preservation |
Microsecond-level performance requirements, multi-tenancy |
| Data Storage Zone |
Parallel file systems, burst buffers, petabyte storage |
Data integrity, high-throughput protection |
Massive data volumes, thousands of concurrent I/O operations |
The Access Zone serves as the external interface that must balance accessibility for legitimate users with protection against external threats. Security controls here focus on initial access validation while supporting the interactive sessions and massive data transfers essential for research productivity.
Management Zone components require elevated privilege protection since compromise here could affect the entire HPC infrastructure. Security measures emphasize administrative access controls and monitoring of privileged operations that control system behavior and resource allocation across all zones.
The High-Performance Computing Zone faces the challenge of maintaining computational performance while protecting shared resources across multiple concurrent workloads. Controls must minimize overhead while preventing cross-contamination between different research projects that share the same physical infrastructure.
Data Storage Zone security implementations aim to protect against data corruption and unauthorized access while maintaining performance in systems handling petabyte-scale storage with thousands of concurrent operations from distributed compute nodes.
What Are the Real-World Attack Scenarios Against HPC Systems?
NIST SP 800-223 documents four primary attack patterns that specifically target HPC infrastructure characteristics and operational requirements. These scenarios reflect actual threat intelligence and incident analysis from HPC facilities worldwide.
Credential Harvesting
Credential Harvesting attacks exploit the extended session durations and shared access patterns common in HPC environments. Attackers target long-running computational jobs and shared project accounts to establish persistent access that remain undetected for months. The attack succeeds by compromising external credentials through phishing or data breaches, then leveraging legitimate HPC access patterns to avoid detection while maintaining ongoing system access.
Remote Exploitation
Remote Exploitation scenarios focus on vulnerable external services that provide legitimate HPC functionality but create attack vectors into internal systems. Web portals, file transfer services, and remote visualization tools become pivot points when not properly secured or isolated. Attackers exploit these services to bypass perimeter defenses and gain initial foothold within the HPC environment before moving laterally to more sensitive systems.
Supply Chain Attacks
Supply Chain Attacks target the complex software ecosystem that supports HPC operations. Malicious code enters through CI/CD (Continuous Integration / Continuous Deployment) pipelines, compromised software repositories, or tainted dependencies in package management systems like Spack. These attacks are particularly dangerous because they affect multiple facilities simultaneously and may remain dormant until triggered by specific computational conditions or data inputs.
Confused Deputy Attacks
Confused Deputy Attacks manipulate privileged programs into misusing their authority on behalf of unauthorized parties. In HPC environments, these attacks often target job schedulers, workflow engines, or administrative tools that operate with elevated privileges across multiple zones. The attack succeeds by providing malicious input that causes legitimate programs to perform unauthorized actions while appearing to operate normally.
What Makes HPC Threat Landscape Unique?
The HPC threat environment differs significantly from enterprise IT due to performance-driven design decisions and research-focused operational requirements that create new attack surfaces and defensive challenges.
Trade-offs between performance and security create fundamental vulnerabilities that do not exist in traditional IT environments. Common performance-driven compromises include:
- Disabled security features – Address Space Layout Randomization, stack canaries, and memory protection removed for computational efficiency
- Unencrypted high-speed interconnects – Latency-sensitive networks that sacrifice encryption for microsecond performance gains
- Throughput-prioritized file systems – Shared storage systems that minimize access control overhead to maximize I/O performance
- Relaxed authentication requirements – Long-running jobs and batch processing negatively affect multi-factor authentication enforcement
These architectural decisions create exploitable conditions that attackers leverage to compromise systems that would otherwise be protected in traditional enterprise environments.
Supply chain complexity in HPC environments far exceeds typical enterprise software management challenges. Modern HPC facilities manage 300+ workflow systems with complex dependency graphs spanning scientific libraries, middleware, system software, and custom research codes. This inherent complexity creates multiple entry points for malicious code injection and makes comprehensive security validation extremely difficult to implement and maintain.
Multi-tenancy across research projects complicates traditional security boundary enforcement. Unlike enterprise systems with well-defined user roles and data classification, HPC systems must support dynamic project memberships, temporary collaborations, and varying data sensitivity levels within shared infrastructure. Such a structure creates scenarios where traditional access controls and data isolation mechanisms prove inadequate for research computing requirements.
The emergence of “scientific phishing“ is another important topic – a novel attack vector where malicious actors provide tainted input data, computational models, or analysis workflows that appear legitimate but contain hidden exploits. These attacks target the collaborative nature of scientific research and the tendency for researchers to share data, code, and computational resources across institutional boundaries without going through comprehensive security validation.
What Does NIST SP 800-234’s Security Control Overlay Provide?
NIST SP 800-234 translates the architectural framework of SP 800-223 into actionable security controls specifically tailored for HPC operational realities. This standard provides the practical implementation guidance that transforms theoretical security architecture into deployable protection measures while maintaining the performance characteristics essential for scientific computing.
How Does the Moderate Baseline Plus Overlay Framework Work?
The SP 800-234 overlay builds upon the NIST SP 800-53 Moderate baseline by applying HPC-specific tailoring to create a comprehensive security control framework. This approach recognizes that HPC environments require both established security practices and specialized adaptations that address unique computational requirements.
The framework encompasses 288 total security controls, consisting of the 287 controls from the SP 800-53 Moderate baseline plus the addition of AC-10 (Concurrent Session Control) specifically for HPC multi-user environments. This baseline provides proven security measures while acknowledging that standard enterprise implementations are frequently not enough for HPC operational demands.
Sixty critical controls receive HPC-specific tailoring and supplemental guidance that addresses the unique challenges of high-performance computing environments. These modifications range from performance-conscious implementation approaches to entirely new requirements that don’t exist in traditional IT environments. The tailoring process considers factors such as:
- Performance impact minimization – Controls adapted to reduce computational overhead
- Scale-appropriate implementations – Security measures designed for systems with hundreds of thousands of components
- Multi-tenancy considerations – Enhanced controls for shared research computing environments
- Zone-specific applications – Differentiated requirements across Access, Management, Computing, and Data Storage zones
Zone-specific guidance provides implementers with detailed direction for applying controls differently across the four-zone architecture. Access zones require different authentication approaches than Computing zones, while Management zones need enhanced privilege monitoring that would be impractical for high-throughput Data Storage zones.
The supplemental guidance is an expansion of standard control descriptions using additional HPC context, implementation examples, and performance considerations. This guidance bridges the gap between generic security requirements and the specific operational realities of scientific computing environments.
What Are the Critical Control Categories for HPC?
The overlay identifies key control families that require the most significant adaptation for HPC environments, reflecting the unique operational characteristics and threat landscapes of high-performance computing systems.
Role-Based Access Control
Role-Based Access Control (AC-2, AC-3) receives extensive HPC-specific guidance due to the complex access patterns inherent in research computing. Unlike enterprise environments with relatively static user roles, HPC systems must support dynamic project memberships, temporary research collaborations, and varying access requirements based on computational resource needs. Account management must accommodate researchers who may need different privilege levels across multiple concurrent projects while maintaining clear accountability and audit trails.
HPC-Specific Logging
HPC-Specific Logging (AU-2, AU-4, AU-5) addresses the massive volume and velocity challenges of security monitoring in high-performance environments. Zone-specific logging priorities help organizations focus monitoring efforts on the most critical security events while managing petabytes of potential log data. Volume management strategies include intelligent filtering, real-time analysis, and tiered storage approaches that maintain security visibility without overwhelming storage and analysis systems.
Session Management
Session Management (AC-2(5), AC-10, AC-12) controls are tailored for the unique timing requirements of computational workloads. Long-running computational jobs may execute for days or weeks, requiring session timeout mechanisms that distinguish between interactive debugging sessions and legitimate batch processing. Interactive debugging sessions need different timeout policies than automated workflow execution, while inactivity detection must account for valid computational patterns that might appear inactive to traditional monitoring systems.
Authentication Architecture
Authentication Architecture (IA-1, IA-2, IA-11) guidance addresses when multi-factor authentication should be required versus delegated within established system trust boundaries. External access points require strong authentication, but internal zone-to-zone communication may use certificate-based or token-based authentication to maintain performance while ensuring accountability. The guidance helps organizations balance security requirements with the need for automated, high-speed inter-system communication.
What Zone-Specific Security Implementations Are Recommended?
The overlay provides detailed implementation guidance for each zone in the four-zone architecture, recognizing that security controls must be adapted to the specific operational characteristics and threat profiles of different HPC system components.
Access Zone implementations focus on securing external connections while supporting the high-volume data transfers and interactive sessions essential for research productivity. Security measures include enhanced session monitoring for login nodes, secure file transfer protocols that maintain performance characteristics, and web portal protections that balance usability with security. User session management must accommodate both interactive work and automated data transfer operations without creating barriers to legitimate research activities.
Management Zone protections require additional safeguards for privileged administrative functions that affect system-wide operations. Enhanced monitoring covers administrative access patterns, configuration change tracking, and job scheduler policy modifications. Privileged operation logging provides detailed audit trails for actions that could compromise system integrity or affect multiple research projects simultaneously.
Computing Zone security implementations address the challenge of protecting shared computational resources while maintaining the microsecond-level performance requirements of HPC workloads. Shared GPU resource protection includes memory isolation mechanisms, emergency power management procedures for graceful system shutdown, and compute node sanitization processes that ensure clean state between different computational jobs. Security controls must minimize performance impact while preventing cross-contamination between concurrent research workloads.
Data Storage Zone recommendations focus on integrity protection approaches that work effectively with petabyte-scale parallel file systems. Implementation guidance covers distributed integrity checking, backup strategies for massive datasets, and access control mechanisms that maintain high-throughput performance. The challenge involves protecting against both malicious attacks and system failures that could compromise research data representing years of computational investment.
How Do Organizations Implement HPC Security in Practice?
Moving from standards documentation to operational reality requires organizations to navigate complex implementation challenges while maintaining research productivity. Successful HPC security deployments balance theoretical frameworks with practical constraints, organizational culture, and the fundamental reality that security measures must enhance rather than hinder scientific discovery.
What Is the “Sheriffs and Deputies” Security Model?
The most effective HPC security implementations adopt what practitioners call the “Sheriffs and Deputies” model – a shared responsibility framework that recognizes both facility-managed enforcement capabilities and the essential role of user-managed security practices in protecting computational resources.
Facility-managed controls are the “sheriffs” of HPC security, providing centralized enforcement mechanisms that users cannot circumvent or disable. These controls include network-level firewall rules, centralized authentication systems, and job scheduler policies, and more. The facility also maintains system-level monitoring that tracks resource usage, detects anomalous behavior patterns, and provides audit trails for compliance requirements.
Authorization frameworks represent another critical facility-managed component, where Resource Utilization Committees (RUCs) and project approval processes ensure that computational access aligns with approved research objectives. These mechanisms prevent unauthorized resource usage while maintaining clear accountability for all computational activities within the facility.
User-managed responsibilities function as “deputies” in this security model, handling aspects that cannot be effectively automated or centrally controlled. Researchers bear responsibility for input data sanitization, ensuring that datasets and computational models don’t contain malicious content that could compromise system integrity. Code correctness and security become user responsibilities, particularly for custom research applications that facility administrators cannot comprehensively validate.
Project access management often involves user coordination, especially in collaborative research environments where multiple institutions share computational resources. Users must understand and comply with data classification requirements, export control restrictions, and intellectual property protections that may vary across different research projects running on the same infrastructure.
This shared responsibility model acknowledges that effective HPC security requires active participation from both facility operators and research users. Neither party is capable of ensuring comprehensive protection on their own – facilities lack the domain expertise to validate all research codes and datasets, while users lack the system-level access needed to implement infrastructure-level protections.
What Are the Practical Security “Rules of Thumb”?
Experienced HPC security practitioners rely on fundamental principles that translate complex standards into day-to-day operational guidance. These rules of thumb help organizations make consistent security decisions while adapting to the dynamic nature of research computing environments.
The identity principle requires that every computational activity traces back to an identifiable, authorized person. While this may seem straightforward – it becomes a lot more complex in environments with shared accounts, automated workflows, and long-running batch jobs. Successful implementations maintain clear audit trails that connect computational resource usage to specific individuals, even when multiple researchers collaborate on shared projects or when automated systems execute computational workflows on behalf of users.
Authorization scope must align with project boundaries and approved research objectives rather than traditional role-based models. Resource Utilization Committee approval drives access decisions, ensuring that computational privileges match the scope of approved research activities. This approach prevents the issue of scope creep, with researchers gaining access to resources far beyond their legitimate project requirements while supporting the collaborative nature of scientific research.
Authentication requirements follow a risk-based approach that distinguishes between different types of system access and computational activities. Two-factor authentication becomes mandatory for external access points and administrative functions, but may be delegated to certificate-based or token-based mechanisms for internal system-to-system communication that requires high-speed, automated operation.
Credential sharing represents a persistent challenge in research environments where collaboration often involves shared computational resources. The practical rule emphasizes individual accountability – even in collaborative projects, access credentials should remain tied to specific individuals who are held responsible for computational activities performed under their identity.
What Performance-Conscious Security Approaches Work?
Real-world HPC security implementations succeed by acknowledging that performance degradation undermines both security and research objectives. Organizations develop security strategies that protect computational resources without creating barriers to legitimate scientific work.
Vulnerability scanning requires careful orchestration to avoid impacting petabyte-scale file systems that serve thousands of concurrent computational jobs. Successful approaches include off-peak scanning schedules, distributed scanning architectures that spread assessment loads across multiple systems, and intelligent scanning that focuses on critical system components rather than attempting comprehensive coverage during peak operational periods.
Malware protection in HPC environments abandons traditional real-time scanning approaches that prove incompatible with high-throughput computational workloads. Instead, effective implementations use behavioral analysis that monitors for anomalous computational patterns, network traffic analysis that detects unauthorized communication patterns, and periodic offline scanning of critical system components during scheduled maintenance windows.
Security control differentiation by node type allows organizations to apply appropriate protection levels without creating universal performance penalties. Login nodes and management systems receive comprehensive security monitoring since they handle sensitive authentication and administrative functions, while compute nodes focus on isolation and resource protection mechanisms that maintain computational performance.
Data protection strategies balance comprehensive backup requirements with the reality that petabyte-scale datasets cannot be backed up using traditional enterprise approaches. Organizations implement tiered protection strategies that provide complete protection for critical configuration data and user home directories while using alternative approaches like distributed replication and integrity checking for large research datasets that would be impractical to back up comprehensively.
Network segmentation provides security benefits while maintaining the high-speed communication essential for parallel computational workloads. Effective implementations use zone-based isolation that aligns with the SP 800-223 architecture while ensuring that legitimate computational communication patterns are not disrupted by security controls designed for traditional enterprise network environments.
Risk-Based Security Checklist for HPC Environments
This prioritized security checklist helps organizations implement NIST SP 800-223 and SP 800-234 controls based on risk levels, ensuring critical vulnerabilities receive immediate attention while building comprehensive protection over time.
Critical/High-Risk Items (Immediate Action Required)
Access Control and Authentication:
- Verify multi-factor authentication is enforced on all external access points (login nodes, web portals, data transfer nodes)
- Audit privileged accounts across all zones – ensure no shared administrative credentials exist
- Review and document all service accounts with cross-zone access permissions
- Validate that default passwords have been changed on all HPC infrastructure components
External Interface Protection:
- Confirm firewall rules properly segment the four security zones per SP 800-223 architecture
- Scan externally-facing services for known vulnerabilities and apply critical security patches
- Verify secure protocols (SSH, HTTPS, SFTP) are used for all external communications
- Review and restrict unnecessary network services and open ports
Data Classification and Protection:
- Identify and classify all sensitive research data according to organizational and regulatory requirements
- Verify export control compliance for international researcher access and data sharing
- Confirm backup procedures exist for critical configuration data and user home directories
- Validate encryption is implemented for data at rest in storage zones and data in transit
- Implement a HPC-specific, NIST-aligned data protection solution such as Bacula Enterprise
Medium Risk Items (Address Within 3-6 Months)
Software and Supply Chain Security:
- Implement automated software inventory tracking using SBOM tools (Spack, containers, or package managers)
- Establish vulnerability scanning schedules that minimize impact on computational workloads
- Document and assess security practices of critical HPC software vendors and dependencies
- Create incident response procedures specific to HPC environments and multi-zone architecture
Monitoring and Logging:
- Configure zone-specific logging priorities per SP 800-234 guidance (AU-2, AU-4, AU-5 controls)
- Implement automated monitoring for unusual computational resource usage patterns
- Establish log retention policies that balance storage costs with compliance requirements
- Deploy security information and event management (SIEM) tools capable of HPC-scale data processing
Operational Security:
- Develop and test disaster recovery procedures for each security zone
- Create security awareness training specific to HPC environments and research collaboration
- Establish procedures for secure software deployment and configuration management
- Implement regular security assessments that account for HPC performance requirements
Lower Risk Items (Ongoing Maintenance Activities)
Documentation and Compliance:
- Maintain current network diagrams and system architecture documentation
- Review and update security policies annually to reflect changing research requirements
- Document security roles and responsibilities using the “Sheriffs and Deputies” model
- Conduct annual reviews of user access rights and project-based permissions
Continuous Improvement:
- Participate in HPC security community forums and threat intelligence sharing
- Evaluate emerging security technologies for HPC applicability and performance impact
- Conduct periodic tabletop exercises for security incident response
- Assess cloud and hybrid HPC security requirements as infrastructure evolves
Performance Monitoring:
- Monitor security control performance impact on computational workloads
- Review and optimize security tool configurations to minimize research productivity impact
- Evaluate new security approaches that maintain HPC performance characteristics
- Track security metrics and key performance indicators specific to research computing environments
What Are the Necessary Software Security and Supply Chain Considerations for HPC?
HPC environments depend on extraordinarily complex software ecosystems that create unique security challenges far beyond traditional enterprise IT environments. Managing hundreds of scientific libraries, workflow systems, and custom research codes while maintaining security requires specialized approaches that balance open-source collaboration benefits with comprehensive risk management.
How Do You Secure Complex HPC Software Stacks?
HPC software management presents unprecedented complexity through package managers like Spack that handle intricate dependency relationships across hundreds of scientific computing libraries, compilers, and runtime environments. This complexity creates security challenges that traditional enterprise software management approaches cannot effectively address.
Package managers in HPC environments manage exponentially more complex dependency graphs than typical enterprise software. A single scientific application might depend on dozens of mathematical libraries, each with their own dependencies on compilers, communication libraries, and system-level components. Spack, the leading HPC package manager, commonly manages 300-500 distinct software packages with dependency relationships that change based on compiler choices, optimization flags, and target hardware architectures.
The security implications include supply chain vulnerabilities where malicious code enters through any point in the dependency graph. Unlike enterprise environments with controlled software catalogs, HPC systems regularly incorporate bleeding-edge research codes, experimental libraries, and custom-built scientific applications that may lack comprehensive security validation.
Open-source software benefits drive HPC adoption but complicate security risk management. Research communities rely on collaborative development models where code quality and security practices vary significantly across projects. Key considerations include:
- Vulnerability disclosure timelines – Research projects may lack formal security response processes
- Maintenance continuity – Academic projects often lose funding or developer support
- Code quality variation – Research codes prioritize scientific accuracy over security practices
- Integration complexity – Combining multiple research codes increases attack surface area
Defensive programming practices become essential for mitigating software vulnerabilities in research codes. Organizations implement code review processes for critical scientific applications, automated testing frameworks that validate both scientific correctness and security properties, and sandboxing approaches that isolate experimental codes from production computational resources.
What Are the CI/CD and Workflow Security Challenges?
The proliferation of automated workflow systems in HPC environments creates substantial security challenges as organizations manage 300+ distinct workflow management tools, each with different security models, credential requirements, and integration approaches.
Scientific workflow systems range from simple batch job submissions to complex multi-facility orchestration platforms that coordinate computational resources across multiple institutions. Common examples include Pegasus, Kepler, Taverna, and NextFlow, each designed for different scientific domains and computational patterns. This diversity creates security challenges as each system requires different authentication mechanisms, has varying levels of security maturity, and integrates differently with HPC infrastructure.
Credential management for automated workflows represents a persistent security challenge. Scientific workflows often require access to multiple computational facilities, external databases, and cloud resources, necessitating long-lived credentials that execute unattended operations across institutional boundaries. Traditional enterprise credential management approaches prove inadequate for research computing requirements.
Common credential security risks include:
- Environment variable exposure – Sensitive credentials stored in shell environments accessible to other processes
- Command line argument leakage – Authentication tokens visible in process lists and system logs
- Configuration file storage – Plaintext credentials in workflow configuration files shared across research teams
- Cross-facility authentication – Credentials that provide access to multiple institutions and cloud providers
External orchestration creates additional security challenges as workflow systems coordinate resources across multiple organizations, cloud providers, and international research facilities. These systems must balance research collaboration requirements with security controls, export restrictions, and varying institutional security policies.
Automated multi-facility workflows require sophisticated credential delegation mechanisms that maintain security while enabling seamless resource access across organizational boundaries. This includes handling different authentication systems, managing temporary credential delegation, and ensuring audit trails across multiple administrative domains.
How Do You Implement Software Bills of Materials (SBOM) for HPC?
Software inventory management in HPC environments requires approaches that handle the dynamic, research-focused nature of scientific computing while providing the visibility needed for effective vulnerability management and compliance reporting.
Dynamic research environments complicate traditional SBOM approaches as scientific computing installations change frequently based on evolving research requirements. Researchers regularly install new software packages, modify existing installations with custom patches, and create entirely new computational environments for specific research projects. This creates constantly evolving software inventories that resist static documentation approaches.
Automated inventory tracking becomes essential for maintaining accurate software bills of materials in environments where manual tracking proves impractical. Successful implementations include container-based approaches that capture complete software environments, package manager integration that automatically tracks installed components, and runtime analysis tools that discover actual software dependencies during computational execution.
Vulnerability tracking across constantly evolving software stacks requires automated approaches that grant the following capabilities:
- Monitor upstream sources – Track security advisories for hundreds of scientific software projects
- Assess impact scope – Determine which installations and research projects are affected by specific vulnerabilities
- Prioritize remediation – Focus security updates on software components that pose the greatest risk
- Coordinate updates – Manage software updates across multiple research projects without disrupting ongoing computational work
Automated testing and validation frameworks provide security benefits while supporting research productivity by ensuring that software updates don’t introduce regressions in scientific accuracy or computational performance. These frameworks include continuous integration pipelines that validate both security properties and scientific correctness, automated regression testing that detects changes in computational results, and performance benchmarking that ensures security updates don’t degrade computational efficiency.
Container and environment management strategies help organizations implement effective SBOM practices by providing immutable software environments that are completely documented, version-controlled, and security-validated. Containerization approaches such as Singularity and Docker enable organizations to create reproducible computational environments while maintaining clear software inventories for security analysis.
How Do Different Sectors Apply HPC Security Standards and Compliance Requirements?
HPC security implementation varies dramatically across sectors, with each facing distinct regulatory requirements, operational constraints, and threat landscapes that shape how NIST standards translate into practical security measures.
What Are Government and Defense Requirements?
Government HPC facilities operate under stringent regulatory frameworks that extend far beyond the NIST SP 800-223 and SP 800-234 baseline requirements. Department of Energy national laboratories must comply with comprehensive policy frameworks including FIPS 199 for information categorization, NIST SP 800-53 for detailed security controls, and NIST SP 800-63 for digital identity guidelines that govern authentication and access management across all computational resources.
These facilities face absolute prohibitions on certain types of information processing. Classified data, Unclassified Controlled Nuclear Information (UCNI), Naval Nuclear Propulsion Information (NNPI), and any weapons development data are strictly forbidden on unclassified HPC systems. Violations result in severe legal consequences and facility security clearance revocation.
Export control regulations create additional operational complexity, particularly affecting international collaboration and equipment management. International researchers may face access restrictions, while hardware components and security tokens often cannot travel across national boundaries. These restrictions significantly impact scientific collaboration and require careful coordination with compliance offices to ensure legitimate research activities don’t inadvertently violate regulations.
What Challenges Do Academic and Research Institutions Face?
Academic institutions navigate a fundamentally different landscape where open science principles often conflict with necessary security restrictions. Research universities need to balance transparency and collaboration requirements with protection of sensitive research data, intellectual property, and student information.
Managing security across multiple research projects with different sensitivity levels creates operational complexity that commercial enterprises rarely face. A single HPC facility might simultaneously support unclassified basic research, industry-sponsored proprietary projects, and government-funded research with export control restrictions. Each project requires different access controls, data protection measures, and compliance reporting.
International collaboration represents both an opportunity and a challenge for academic institutions. While global scientific collaboration drives innovation and discovery, it also creates security considerations around foreign researcher access, data sharing across national boundaries, and compliance with varying international regulations. Universities must maintain research openness while addressing legitimate security concerns about foreign influence and technology transfer.
What Are Commercial HPC Security Considerations?
Commercial HPC environments face unique challenges around cloud integration and hybrid deployments. Many organizations now combine on-premises HPC resources with cloud-based computational capabilities, creating security architectures that span multiple administrative domains and security models. This hybrid approach requires careful attention to data sovereignty, credential management across environments, and consistent security policy enforcement.
Vendor management in commercial HPC environments involves specialized hardware and software providers who may have limited security maturity compared to traditional enterprise vendors. Organizations must evaluate security practices across the entire supply chain, from custom silicon manufacturers to specialized scientific software developers.
Multi-tenant commercial environments create additional security challenges as cloud HPC providers must isolate multiple customer workloads while maintaining the performance characteristics that justify HPC investments. This requires sophisticated resource isolation, network segmentation, and monitoring capabilities that go beyond traditional cloud security approaches.
How Do These Standards Integrate with Other Security Frameworks?
The integration challenges become apparent when organizations must align FISMA and FedRAMP requirements with HPC-specific implementations. Federal agencies using cloud HPC resources must ensure that cloud providers meet FedRAMP authorization requirements while implementing the HPC-specific controls outlined in SP 800-234. This often requires custom security control implementations that satisfy both frameworks simultaneously.
NIST SP 800-171 plays a critical role when HPC systems process Controlled Unclassified Information (CUI) in research environments. Academic institutions and commercial research organizations must implement the 110 security requirements of SP 800-171 while maintaining the performance and collaboration characteristics essential for research productivity.
The NIST Cybersecurity Framework provides a complementary approach that many organizations use alongside the HPC-specific standards. The Framework’s focus on Identify, Protect, Detect, Respond, and Recover functions helps organizations develop comprehensive security programs that incorporate HPC-specific controls within broader cybersecurity strategies.
ISO 27001/27002 alignment in research environments requires careful attention to the unique operational characteristics of scientific computing. Research organizations implementing ISO standards must adapt traditional information security management approaches to accommodate the collaborative, international, and performance-sensitive nature of scientific computing while maintaining the systematic approach that ISO frameworks require.
Why Are HPC Data Protection and Backup Critical?
HPC data protection extends far beyond traditional enterprise backup strategies, requiring specialized approaches that address the unique challenges of petabyte-scale research datasets and the computational infrastructure supporting critical scientific discovery. Effective data protection in HPC environments must balance comprehensive protection requirements with performance considerations that make or break research productivity.
What Makes HPC Backup Fundamentally Different from Enterprise Backup?
The scale differential between HPC and enterprise environments creates fundamentally different backup challenges that render traditional enterprise solutions inadequate for high-performance computing requirements. While enterprise systems typically manage terabytes of data, HPC facilities routinely handle petabyte and exabyte-scale datasets that would overwhelm conventional backup infrastructure.
Petabyte and exabyte-scale data volumes change backup strategies from routine operations to major engineering challenges. A single research dataset might exceed the total storage capacity of entire enterprise backup systems, while the time required to back up such datasets could span weeks or months using traditional approaches. This scale creates scenarios where full system backup becomes mathematically impossible given available backup windows and storage resources.
Performance implications of backup operations represent another critical distinction from enterprise environments. HPC systems support concurrent computational workloads that generate massive I/O loads against shared storage systems. Traditional backup approaches that scan file systems or create snapshot copies tend to severely impact active computational jobs, potentially invalidating research results or wasting weeks of computational time.
Traditional enterprise backup solutions fail in HPC environments because they assume relatively stable data patterns and manageable data volumes. Enterprise backup tools typically expect structured databases, office documents, and application data with predictable growth patterns. HPC research data often consists of massive scientific datasets, complex file hierarchies with millions of small files, and computational output that may be generated faster than it would take to back it up using conventional methods.
NIST SP 800-234 addresses these challenges through HPC-specific backup controls including CP-6 (Alternate Storage Site), CP-7 (Alternate Processing Site), and CP-9 (Information System Backup) with tailored implementation guidance. These controls acknowledge that HPC backup strategies must prioritize critical system components and irreplaceable research data rather than attempting comprehensive backup coverage that proves impractical at HPC scale.
What Are the Unique HPC Data Protection Requirements?
HPC data protection requires strategic prioritization that focuses available backup resources on the most critical and irreplaceable data components while accepting that comprehensive backup of all research data may be impractical or impossible given scale and performance constraints.
Configuration data and critical project data receive the highest protection priority since these components are essential for system operation and often irreplaceable. System configurations, user home directories containing research code and analysis scripts, and project metadata must be protected comprehensively since recreating this information would be extremely difficult or impossible.
Parallel file systems, burst buffers, and campaign storage each require different backup strategies based on their role in the computational workflow. Parallel file systems like Lustre, GPFS (General Parallel File System), and IBM Spectrum Scale support active computational workloads and require backup approaches that minimize performance impact. Burst buffers provide temporary high-speed storage that may not require traditional backup but needs rapid recovery capabilities. Campaign storage holds intermediate research results that may warrant selective backup based on research value and reproducibility considerations.
Zone-based backup strategies align with the NIST SP 800-223 four-zone architecture, recognizing that different zones have varying backup requirements and performance constraints. Access zone data might receive frequent backup due to its external exposure, while Computing zone data may focus on rapid recovery rather than comprehensive backup coverage.
The trade-offs between full system backup and selective protection reflect the practical reality that HPC facilities must make strategic decisions about data protection based on research value, reproducibility potential, and replacement cost. Organizations develop data classification frameworks that guide backup decisions and ensure that protection resources focus on the most critical research assets.
How Does Bacula Enterprise Address HPC-Scale Data Protection?
Bacula Enterprise represents one of the few commercial backup solutions specifically designed to handle the scale and performance requirements of HPC environments, providing capabilities that address the unique challenges of petabyte-scale scientific computing infrastructure.
The architecture of Bacula Enterprise handles HPC performance requirements through distributed backup operations that scale across multiple systems and storage resources simultaneously. This distributed approach enables backup operations that don’t bottleneck on single points of failure while maintaining the throughput necessary for HPC-scale data protection without impacting active computational workloads.
Integration with parallel file systems like Lustre, GPFS, and IBM Spectrum Scale requires specialized approaches that understand the distributed nature of these storage systems. Bacula Enterprise provides native integration capabilities that work with the metadata and data distribution patterns of parallel file systems, enabling efficient backup operations that leverage the inherent parallelism of HPC storage infrastructure.
Zone-based security model support aligns with NIST SP 800-223 requirements by providing backup operations that respect the security boundaries and access controls defined in the four-zone architecture. This includes backup processes that maintain appropriate security isolation between zones while enabling efficient data protection operations across the entire HPC infrastructure.
Key capabilities that make Bacula Enterprise suitable for HPC environments include:
- Scalable architecture – Distributed operations that scale with HPC infrastructure growth
- Performance optimization – Backup operations designed to minimize impact on computational workloads
- Parallel file system integration – Native support for HPC storage systems and their unique characteristics
- Flexible retention policies – Data lifecycle management appropriate for research data with varying retention requirements
- Security integration – Backup operations that maintain HPC security zone integrity and access controls
What Future Challenges Will Impact HPC Security?
The HPC security landscape continues evolving rapidly as emerging technologies and evolving threats create new challenges that current standards and practices must adapt to address. Organizations implementing HPC security today must consider not only present requirements but also prepare for technological advances that will reshape both computational capabilities and threat landscapes.
How Will Emerging Technologies Affect Architecture?
Exascale computing capabilities represent the next major leap in HPC performance, bringing computational power that exceeds current systems by orders of magnitude. These systems will feature novel accelerator architectures, revolutionary networking technologies, and storage systems operating at unprecedented scales. The security implications include exponentially larger attack surfaces, new types of hardware vulnerabilities, and performance requirements that may render current security approaches inadequate.
Quantum computing technologies will create dual impacts on HPC security – both as computational resources requiring protection and as threats to existing cryptographic systems. Near-term quantum systems would require specialized security controls for protecting quantum states and preventing decoherence attacks, while longer-term quantum capabilities will necessitate migration to post-quantum cryptographic algorithms across all HPC infrastructure.
Emerging networking technologies and storage solutions including photonic interconnects, persistent memory systems, and neuromorphic computing architectures will require security updates to current zone-based models. These technologies may blur traditional boundaries between compute, storage, and networking components, potentially requiring new security zone definitions that reflect novel architectural patterns.
What Evolving Threats Should Organizations Prepare For?
AI and machine learning-powered attacks represent an emerging threat category specifically targeting HPC computational resources. Adversaries may develop attacks that leverage artificial intelligence to identify vulnerabilities in scientific codes, optimize resource consumption to avoid detection, or target specific research areas for intellectual property theft. These attacks could prove particularly dangerous because they may adapt to defensive measures in real-time.
Supply chain security evolution becomes increasingly critical as HPC systems incorporate specialized components from global suppliers. Future threats may target custom silicon designs, firmware embedded in accelerators, or specialized software libraries developed for emerging computational paradigms. The challenge involves developing verification capabilities for components that are becoming increasingly complex and specialized.
Edge computing integration will extend HPC capabilities to distributed sensing networks, autonomous systems, and real-time computational requirements that current centralized models cannot support. This integration will challenge the traditional four-zone architecture by introducing distributed computational elements that require security controls while operating in potentially hostile environments with limited administrative oversight.
The convergence of these trends suggests that future HPC security will require more dynamic, adaptive approaches that respond to rapidly changing technological capabilities and threat landscapes while maintaining the performance characteristics essential for scientific discovery and innovation.
Conclusion: What Does Effective HPC Security Look Like?
Effective HPC security emerges from organizations that successfully balance research productivity with comprehensive protection by implementing zone-based architectures, performance-conscious security controls, and shared responsibility models that engage both facility operators and research users. The most successful implementations treat security not as a barrier to scientific discovery but as an enabler that protects valuable computational resources and research investments while maintaining the collaborative, high-performance characteristics essential for advancing scientific knowledge.
Critical success factors for implementing NIST SP 800-223 and SP 800-234 include organizational commitment to the shared responsibility model, investment in security tools and processes designed for HPC scale and performance requirements, and ongoing adaptation to evolving threats and technological capabilities. Organizations must recognize that HPC security requires specialized expertise, dedicated resources, and long-term strategic planning that extends beyond traditional enterprise IT security approaches.
The security landscape continues evolving with advancing HPC capabilities, emerging threats, and new technologies that will reshape both computational architectures and protection requirements. Successful organizations maintain flexibility in their security implementations while adhering to proven architectural principles, ensuring their HPC infrastructure supports both current research missions and future scientific breakthroughs while maintaining appropriate protection against evolving cyber threats.
Key Takeaways
- HPC security requires specialized approaches that differ fundamentally from enterprise IT security due to unique performance requirements and research-focused operational models
- NIST SP 800-223 and SP 800-234 provide comprehensive guidance through zone-based architecture and tailored security controls that balance protection with computational performance
- Successful implementation depends on shared responsibility models where facility operators manage infrastructure protections while research users handle application-level security practices
- Software supply chain security presents ongoing challenges through complex dependencies, diverse workflow systems, and collaborative development that requires continuous vulnerability management
- Data protection strategies must be tailored for HPC scale using selective backup approaches and specialized tools designed for petabyte-scale datasets without performance impact
- Future HPC security will require adaptive approaches that respond to emerging technologies like exascale computing while addressing evolving threats including AI-powered attacks
We’re proud to announce that Bacula Enterprise has been recognized as a Champion in the 2025 Emotional Footprint Report for Data Replication, published by Info-Tech Research Group’s SoftwareReviews.

This award is based entirely on real user feedback, which makes it especially meaningful. It reflects not just the performance of our technology, but also the trust, satisfaction, and positive experiences of the organizations that rely on Bacula Enterprise every day.
What Makes Bacula Enterprise Stand Out
Bacula Enterprise is an enterprise-grade backup and recovery solution designed for higher security, performance, and lower cost. Our customers span a wide range of industries, all with complex and demanding IT environments. Some highlights from the 2025 report:
- 91% of users are likely to recommend Bacula Enterprise
- 100% of customers plan to renew
- 87% are satisfied with cost relative to value
- +95 Net Emotional Footprint score, showing overwhelmingly positive customer sentiment
When broken down into key categories, Bacula Enterprise achieved excellent scores:
- 97% for Product Experience
- 94% for Strategy & Innovation
- 92% for Negotiation & Contract
- 94% for Conflict Resolution
- 94% for Service Experience
These results confirm what our customers often tell us: Bacula Enterprise is not only reliable and feature-rich, but also backed by responsive and trustworthy support.
What Users Are Saying
Here’s what a few recent reviewers shared:
- “It can take backup in any operating system like Windows, Linux and more. It is very secure, saves my data well, and provides flexible backup options.” – Mithilesh T. (IT Manager)
- “This tool is really helpful to get automated backup of VMware and databases. It makes work fast and there are no worries of data loss. The support team is always ready to help.” – Raghav S. (IT Manager)
- “Reliable, secure, and cost-effective backup solution. Reliable performance and easy backup management.” – Ganga Sagar Y. (Consultant)
These voices underline the strengths highlighted in the Emotional Footprint Report: reliability, efficiency, trustworthiness, and continual improvement.
Most industry awards focus on technical specifications or analyst evaluations. The Emotional Footprint Report is different, it measures how customers feel about the product and the company. It looks at dimensions like trust, integrity, transparency, innovation, and support responsiveness.
For Bacula Enterprise to achieve one of the highest Net Emotional Footprint scores in the industry (+95) means that customers consistently view us as:
- Reliable – delivering dependable results across diverse environments.
- Performance-enhancing – making IT operations faster and more effective.
- Supportive – providing efficient and responsive service when it matters most.
- Innovative – continually improving features to meet evolving enterprise needs.
This recognition validates our philosophy: great software is more than code—it’s about building strong relationships and empowering customers with confidence in their data protection.
A Thank You to Our Customers
We are proud to receive this recognition, but it is truly thanks to the feedback and trust of our customers. Their experiences and insights guide our roadmap and inspire us to continually improve. To read more, you can explore Bacula Enterprise’s full profile and reviews here on SoftwareReviews.
The conversation around backups has changed dramatically in recent years. Five years ago, backups were discussed as a separate IT function. Today? It’s a prime attack target, and if you’re not treating it as part of your core security strategy – you’re asking for trouble.
The numbers don’t lie. When Verizon released their latest breach report, backup infrastructure showed up as a compromise vector in 23% of incidents. That’s not just collateral damage – that’s attackers specifically going after your recovery capabilities.
Zero-trust has become the go-to framework for a reason. The old castle-and-moat approach failed because attackers are already inside your network. They’ve been there for months, sometimes years, just waiting for the right moment to strike. When that moment comes, they’re not just encrypting your production data – they’re coming for your backups too.
What Zero-Trust Really Means in Practice
Forget the buzzword definitions for a moment. Zero-trust boils down to this: you don’t trust anyone or anything by default. Every request gets verified, every time, without exceptions.
I learned this lesson the hard way during an incident response three years ago. A financial services client thought they were protected because their backup administrator had been with the company for eight years. Turns out his credentials had been compromised for six months. The attackers used his access to systematically corrupt backup files while planning their ransomware deployment.
That incident taught me that zero-trust isn’t paranoid – it’s realistic. Here’s how it works:
You verify every request using multiple signals – not just usernames and passwords, but device certificates, location data, behavioral patterns. If something looks off, you block access first and ask questions later.
Least privilege means your database admin can’t access HR backups, and your HR team can’t restore financial data. Everyone gets exactly what they need to do their job, nothing more.
The assume-breach mindset changes everything. Instead of asking “how do we keep attackers out,” you ask “what happens when they get in?” That shift in thinking makes you design better defenses.
Why Backups Became the New Crown Jewels
Here’s what changed: ransomware groups got smarter. Early ransomware was akin to digital vandalism – encrypt everything and demand payment. Modern ransomware is strategic. These groups spend weeks mapping your environment, identifying critical systems, and locating backup infrastructure.
A study from last year showed that 96% of ransomware victims also had their backups targeted. This kind of statistic is absolutely disastrous for business continuity. Your disaster recovery plan assumes you’ll have clean backups to restore from. But what happens when that assumption is wrong?
Remote work made this problem worse. Now you’ve got employees accessing backup systems from home networks, coffee shops, hotel wifi. Traditional security models assumed everyone was behind your corporate firewall. Those days are gone.
Building Authentication That Actually Works
Multi-factor authentication should be table stakes for backup access, but implementation matters. I’ve seen organizations deploy MFA that’s so cumbersome their admins find workarounds. That defeats the purpose.
Smart card authentication works well for backup administrators because it’s both secure and convenient. Biometric factors are getting better too, especially for mobile access scenarios.
Role-based access control gets interesting with backups because you need separation of duties. The person who can create backups shouldn’t be the same person who can delete them. The person who manages retention policies shouldn’t have restore privileges. It sounds complex, but it’s actually simpler to manage than you’d think.
Logging is crucial, but make sure your logs are useful. Timestamp, user identity, source IP, action performed, and result. Feed that data into your SIEM so you can spot patterns. Unusual restore requests at 3 AM might be legitimate, but they deserve investigation.
Encryption Strategy That Goes Beyond Compliance Checkboxes
Most organizations encrypt backups because regulations require it, but they don’t think strategically about key management. I’ve responded to incidents where companies had perfect backups that were completely useless because they lost their encryption keys during the attack.
Client-side encryption protects data before it leaves your environment. This matters more than you might think – if attackers compromise your backup infrastructure but can’t decrypt the data, you’ve bought yourself time and options.
End-to-end encryption means your backup vendor can’t read your data, which is important for compliance but also for limiting your attack surface. If their systems get breached, your encrypted data is still protected.
Key rotation should be automatic and regular. I recommend quarterly rotation for backup encryption keys, with emergency rotation procedures if you suspect compromise. Enterprise key management systems handle this automatically, but test your rotation procedures before you need them in an emergency.
Immutability and Geographic Distribution
Immutable backups were a nice-to-have feature five years ago. Today they’re borderline mandatory. Write-once storage, whether it’s tape, immutable cloud storage, or specialized backup appliances, creates recovery options that attackers literally cannot eliminate.
The trick is to try and balance immutability with operational requirements. You need some backups that can be modified for operational recovery, and others that are completely immutable for disaster scenarios. Most organizations implement a 3-2-1-1 strategy: three copies of critical data, two different media types, one offsite, and one immutable.
Geographic distribution helps with both disaster recovery and security. Attackers might compromise your primary datacenter and your local DR site, but having immutable copies in a different region or with a different cloud provider gives you options.
Companies like Bacula Enterprise have built their entire platform around this approach. Military-grade encryption, mandatory MFA, immutable storage options, and comprehensive logging create a backup environment that’s inherently zero-trust.
Monitoring and Incident Detection
Your SIEM should be watching backup activity just like it watches everything else. Unusual patterns often indicate problems before they become disasters.
Mass deletion attempts are obvious red flags, but watch for subtler indicators too. Changes to retention policies, new user accounts with backup privileges, restore requests for unusual data sets. These might be legitimate business activities, or they might be reconnaissance for a larger attack.
Recovery testing serves double duty – it validates your backups and tests your monitoring systems. If you can’t detect unusual restore activity during a planned test, you won’t catch it during an actual incident.
Automated integrity checking catches corruption before you need the data. Hash verification, consistency checks, and periodic restore tests should run automatically. When these checks fail, investigate immediately.
The Business Benefits Are Real
Organizations that implement zero-trust backup see measurable improvements in multiple areas. Ransomware resilience improves because attackers can’t eliminate all recovery options. Even complex, organized attacker groups tend to struggle when faced with properly segmented and immutable backups.
Compliance becomes significantly more manageable when not just access controls, but also encryption and audit trails are all built into your backup processes. Auditors love detailed logs and clear role separations.
Insider threat protection improves because no single person has unrestricted access to backup operations. Malicious insiders and compromised accounts find it a lot more difficult to cover their tracks than ever before.
Confidence in business recovery capabilities also improves the overall business continuity planning. Tested, monitored, protected backups enable faster recovery and better uptime.
Real-World Implementation Challenges
Key management is usually the biggest stumbling block. Organizations either make it too complex (causing operational problems) or too simple (creating security gaps). Enterprise key management systems solve this, but they require upfront investment and training.
User resistance to stricter authentication is common but manageable. Focus on user experience – modern MFA solutions are much more convenient than older implementations. Smart cards, mobile authenticators, and biometric options are all feasible for reducing friction while also contributing to security improvement.
Remote access requires careful planning. Virtual Private Network solutions (such as Surfshark VPN) offer secure tunnels to access backups, but the exact specifications have to be evaluated on a case-by-case basis with your specific requirements in mind. All operational teams need not just performance, but also reliability and ease of use in such services…
Performance impact from additional security layers should be minimal with proper implementation. Security measures must not create operational bottlenecks, especially in critical recovery scenarios.
Preparation for the Future
The overall threat landscape is in a state of constant evolution, forcing backup security measures to keep up with all the changes. Regular policy reviews, for example, would help ensure that your current measures are capable of handling up-to-date risks, as things change quickly and measures that were effective just a year or two ago might not be as effective today.
Technology changes bring new risks, but also create plenty of new opportunities. Cloud backup services are a good example, providing immutability with geographic distribution while also creating a number of new access vectors that need to be covered. Alternatively, the rise of Artificial Intelligence and Machine Learning improves threat detection, while also being used in newer tools on the attackers’ side.
The trend for remote workforce is also not going away any time soon. As such, backup strategies have to assume that any critical recovery operation might happen from a home office, a mobile device, or an untrusted network – forcing users to plan accordingly.
Making It Happen
Backup security isn’t just an IT problem anymore – it’s a business continuity issue that deserves executive attention and investment. Zero-trust principles offer a great, working framework to protect all the necessary critical assets.
Begin by implementing strong authentication and role-based access controls. Add comprehensive encryption to the mix – with defined encryption key management. Implement immutability and geographic distribution. Do not forget about monitoring and testing everything regularly, either.
Perfect security is not the end goal for any of these measures, as it is practically impossible. The goal is to make your backup environment resilient enough to support business continuity efforts – even if primary systems are somehow compromised.
Frequently Asked Questions
What’s the difference between zero-trust backup and regular backup security?
Regular backup security tends to rely on network perimeter controls with trust-based access. Zero-trust backup efforts continuously verify every single request, assuming that systems are already compromised at any point in time.
The practical difference between the two is most noticeable in comprehensive monitoring, strict access controls, and immutable storage options that are impossible to bypass – even by administrators.
Is it practical to have both encryption and immutability?
Absolutely, and it is actually recommended to use both immutability and encryption when possible. Encryption secures against unauthorized access, while immutability prevents deletion or modification. These measures address different attack vectors, complementing each other in different ways – which is why most enterprise backup solutions support them both simultaneously.
How do we balance security with recovery speed during emergencies?
Testing becomes a critical measure when there is a need to find a balance between recovery speed and protection measures. Your recovery procedures need to be properly documented and regularly practiced to ensure that security controls don’t slow down necessary recovery operations. Automated verification, pre-staged encryption keys, and role-based access can even speed up recovery efforts in their own way – eliminating confusion about who can do what.
Can we implement zero-trust backup with existing cloud services?
Most major cloud providers support zero-trust backup principles using features like immutable storage options, encryption controls, and comprehensive access management. The point is to ensure that your security controls are extended consistently across all backup locations – doesn’t matter if they’re on-premises or in the cloud.
What happens if we lose access to our key management system?
This particular scenario is exactly why enterprise key management systems have options like redundancy, escrow, and disaster recovery. With that being said, poor key management has the potential to make encrypted backups inaccessible on a permanent basis. As such, this topic deserves serious investment and planning, with documented recovery procedures that are tested regularly.
What is Proxmox?
Proxmox Virtual Environment (VE) is a comprehensive open-source virtualization management platform that combines multiple virtualization technologies under a single, unified interface. Built on Debian Linux, Proxmox offers organizations a cost-effective alternative to proprietary virtualization solutions while maintaining enterprise-grade functionality. The platform’s strength lies in its ability to manage both virtual machines and containers seamlessly, making it particularly attractive for businesses that seek flexible infrastructure solutions without the complexity of larger cloud platforms.
What Makes Proxmox VE a Complete Virtualization Solution?
Proxmox VE operates as an integrated virtualization platform that eliminates the need for separate hypervisor installations and management tools. Unlike traditional virtualization setups that require multiple software components, Proxmox delivers everything through a single ISO installation that includes the hypervisor, management interface, and clustering capabilities.
The platform operates on a web-based management model, allowing administrators to control entire virtualization environments through any modern browser. This approach significantly reduces the learning curve compared to command-line-heavy alternatives while still providing advanced users with full shell access when needed.
What sets Proxmox apart is its dual virtualization approach:
- Full virtualization via KVM – Runs unmodified operating systems with hardware-level isolation
- Container virtualization through LXC – Delivers lightweight, OS-level virtualization for Linux workloads
- Unified management interface – Controls both virtualization types through a single dashboard
This flexibility allows organizations to optimize resource usage by choosing the most appropriate virtualization method for each workload, rather than being locked into a single approach.
What are the Essential Components of Proxmox Architecture?
Proxmox VE’s architecture consists of several interconnected components that work together to deliver comprehensive virtualization management.
Proxmox VE Manager forms the central control system, providing the web interface and API endpoints that administrators use for daily operations. This component handles user authentication, resource allocation, and coordination between different nodes in a cluster environment.
Backup and restore functionality operates through the Proxmox Backup Server, which runs as a separate appliance or integrated service. This component handles incremental backups, deduplication, and cross-node backup distribution for disaster recovery scenarios.
The clustering engine enables multiple Proxmox nodes to operate as a unified system, sharing resources and providing automatic failover capabilities. This component uses a proven corosync/pacemaker foundation to ensure reliable cluster communication and split-brain prevention.
For enterprise-level backup and recovery, organizations are recommended to use dedicated backup solutions such as Bacula Enterprise, which can natively integrate with all the technologies covered in this blog.
Which Virtualization Technologies Power Proxmox?
Proxmox leverages two primary virtualization technologies, each optimized for different use cases and performance requirements: KVM and LXC.
KVM (Kernel-based Virtual Machine) provides full hardware virtualization capabilities, allowing Proxmox to run unmodified operating systems with near-native performance. KVM integration includes support for advanced features like live migration, memory ballooning, and hardware pass-through for specialized workloads requiring direct hardware access.
LXC (Linux Containers) delivers operating system-level virtualization with significantly lower overhead than traditional VMs. Container support includes advanced networking options, resource limiting, and the ability to run multiple isolated Linux environments on a single kernel.
The platform’s supporting technologies include:
- QEMU integration – Handles device emulation and VM management layer
- ZFS and LVM storage systems – Provides snapshots, compression, and RAID capabilities
- Hardware pass-through support – Enables direct hardware access for specialized workloads
- Cross-platform compatibility – Supports Windows, Linux, and BSD guest operating systems
These technologies integrate seamlessly to deliver enterprise-grade performance while maintaining the simplicity that makes Proxmox accessible to smaller organizations.
What are the Key Features of Proxmox?
Proxmox’s feature set distinguishes it from both simple hypervisors and complex cloud platforms by aiming for a balance between enterprise functionality and operational simplicity. The platform combines advanced clustering capabilities, flexible storage options, and comprehensive backup solutions into a cohesive management experience. These features work together to provide organizations with production-ready virtualization infrastructure capable of scaling from small deployments to multi-node clusters, all while maintaining the cost advantages of open-source software.
How Does Proxmox Handle Cluster Management and Monitoring?
Proxmox delivers centralized cluster management through its web-based interface, providing real-time visibility into resource utilization and cluster health across multiple nodes. The dashboard combines monitoring, alerting, and management functions into a single interface.
Key management capabilities include:
- Node auto-discovery and resource pooling across cluster members
- Role-based access control with granular permission management
- REST API integration for external tools and automation
- Real-time monitoring of CPU, memory, network, and storage metrics
What High Availability and Migration Options Are Available?
Proxmox provides enterprise-grade high availability (HA) through automated failover and live migration capabilities. VMs automatically restart on healthy nodes during failures, while live migration enables zero-downtime maintenance and load balancing.
Core HA features:
- Automatic failover with VM restart on available cluster nodes
- Live migration for both compute and storage resources
- Maintenance mode for planned migrations and updates
- Fencing mechanisms to prevent data corruption
How Does Proxmox Support Both Containers and Virtual Machines?
Proxmox uniquely manages both LXC containers and KVM virtual machines through a unified interface. This dual approach optimizes resource allocation by matching workload requirements to the appropriate virtualization technology.
Container support includes privileged and unprivileged modes, while VM capabilities extend to hardware pass-through and cloud-init integration for automated deployments.
What Storage and Network Features Does Proxmox Offer?
Proxmox supports diverse storage backends including local storage, Ceph distributed storage, ZFS, and traditional SAN/NAS systems. Software-defined networking capabilities include VLAN support, bonding, and integration with external SDN (software-defined networking) solutions.
Key infrastructure features:
- Multiple storage types – Local, NFS, iSCSI, Ceph, and ZFS support
- Network bonding and VLAN configuration for redundancy and isolation
- Built-in firewall with host and guest-level security controls
How Comprehensive Are Proxmox’s Backup and Snapshot Capabilities?
The Proxmox Backup Server provides enterprise-grade data protection with incremental backups, deduplication, and encryption. Instant snapshots enable point-in-time recovery for both VMs and containers without impacting production workloads.
Backup capabilities support full system restoration, individual file recovery, and cross-node distribution for disaster recovery scenarios.
What is OpenStack?
OpenStack is a comprehensive open-source cloud computing platform designed to build and manage large-scale public and private cloud infrastructures. Originally developed by NASA and Rackspace, OpenStack has evolved into an industry standard for organizations that need enterprise-grade cloud capabilities combined with the flexibility of open-source software. Unlike simpler virtualization platforms, OpenStack provides a complete Infrastructure-as-a-Service (IaaS) solution capable of scaling from small private clouds to massive public cloud deployments to serve millions of users.
How Does OpenStack’s Modular Architecture Work?
OpenStack operates through a service-oriented architecture where individual components handle specific cloud functions while communicating through well-defined APIs. This modular design allows organizations to deploy only the services they need, adjusting complexity based on requirements rather than implementing unnecessary overhead.
Each OpenStack service runs as an independent daemon capable of being distributed across multiple physical servers for high availability and scalability. Services communicate using message queues and REST APIs, ensuring loose coupling to enable individual component updates without system-wide disruptions.
The architecture’s flexibility extends to deployment models:
- All-in-one installations for development and small-scale testing environments
- Multi-node deployments with services distributed across dedicated hardware
- Containerized deployments using Kubernetes or Docker for enhanced portability
- Hybrid configurations mixing bare-metal and virtualized service components
This microservices approach enables OpenStack to handle demanding enterprise workloads while maintaining the operational flexibility needed for diverse deployment scenarios.
What Are OpenStack’s Essential Core Services?
OpenStack’s functionality centers around several core services that provide fundamental cloud infrastructure capabilities. These services work together to deliver compute, storage, networking, and identity management functions comparable to major public cloud providers. As of the 2025.1 Epoxy release, OpenStack includes over 30 official services, each handling specific aspects of cloud operations:
Core Infrastructure Services form the foundation:
- Nova (Compute) – Virtual machine lifecycle management and hypervisor integration
- Neutron (Networking) – Software-defined networking with plugin architecture
- Cinder (Block Storage) – Persistent volume management and storage backend integration
- Swift (Object Storage) – Distributed object storage system comparable to Amazon S3
- Keystone (Identity) – Authentication, authorization, and service catalog management
- Glance (Image Service) – Virtual machine image repository and distribution
Advanced Cloud Services extend functionality:
- Heat (Orchestration) – Infrastructure automation using templates
- Horizon (Dashboard) – Web-based management interface
- Ironic (Bare Metal) – Physical server provisioning and lifecycle management
- Magnum (Container Infrastructure) – Kubernetes and Docker Swarm cluster management
- Zun (Containers) – Direct container management without orchestration
- Octavia (Load Balancing) – Network load balancing as a service
- Designate (DNS) – DNS management and integration
- Barbican (Key Management) – Cryptographic key and certificate storage
- Manila (Shared File Systems) – NFS and CIFS shared storage management
Operational and Monitoring Services support production deployments:
- Ceilometer (Telemetry) – Resource usage data collection
- Aodh (Alarming) – Monitoring alerts based on telemetry data
- Vitrage (Root Cause Analysis) – Infrastructure problem diagnosis
- Watcher (Infrastructure Optimization) – Resource optimization recommendations
- Masakari (Instance HA) – Automatic VM recovery during host failures
This comprehensive service catalog enables OpenStack to match public cloud provider capabilities while maintaining complete organizational control over infrastructure and data.
What are the Key Features of OpenStack?
OpenStack’s feature set reflects its design for large-scale enterprise cloud deployments where multi-tenancy, advanced networking, and API-driven automation are critical requirements. Unlike platforms focused on simplicity, OpenStack prioritizes comprehensive functionality that supports complex organizational structures and demanding workloads. These capabilities enable businesses to create private clouds that rival public cloud providers in terms of features and scalability, while also maintaining complete control over their own infrastructure and data.
How Does OpenStack Handle Scalability and Multi-Tenant Support?
OpenStack excels at horizontal scaling through its distributed architecture, supporting deployments that range from small private clouds to massive installations working for millions of users. The platform’s service-oriented design enables individual components to scale independently based on demand patterns.
Multi-tenancy capabilities provide complete isolation between different organizational units or customers. Each tenant receives dedicated virtual resources including networks, storage volumes, and compute quotas while sharing the underlying physical infrastructure.
Key scalability features:
- Horizontal service scaling – Individual services scale across multiple nodes
- Resource quotas and limits – Granular control over tenant resource consumption
- Availability zones – Geographic distribution and fault isolation
- Cells architecture – Nova cells enable massive compute scaling
The platform supports thousands of compute nodes and is capable of managing hundreds of thousands of virtual machines through its distributed control plane architecture.
What Advanced Networking Capabilities Does OpenStack Provide?
OpenStack Neutron delivers software-defined networking capabilities that surpass traditional virtualization platforms. The plugin architecture supports integration with enterprise networking hardware and advanced SDN controllers.
Network virtualization includes support for VLANs, VXLANs, GRE tunnels, and Geneve encapsulation. Multi-tenant network isolation ensures complete traffic separation between different organizational units or customers.
Advanced networking features of the platform include:
- Load balancing as a service through Octavia integration
- VPN and firewall services with policy-based security controls
- BGP and MPLS support for carrier-grade networking requirements
- SR-IOV and DPDK (Single Root Input/Output Virtualization and Data Plane Development Kit) integration for high-performance networking
Quality of Service (QoS) policies enable bandwidth guarantees and traffic prioritization across virtual networks, supporting demanding applications with specific performance requirements.
How Flexible Are OpenStack’s Storage Backend Options?
OpenStack provides comprehensive storage abstraction supporting virtually any enterprise storage system through its pluggable backend architecture. Organizations use it to leverage existing storage investments while gaining cloud-native storage capabilities.
Block storage through Cinder supports over 80 different storage backends including traditional SAN arrays, software-defined storage systems, and hyper-converged infrastructure. Object storage via Swift provides scalable, distributed storage comparable to Amazon S3.
Storage capabilities include:
- Multi-backend configurations – Different storage tiers within single deployments
- Volume encryption and snapshot management across backend types
- Quality of Service controls for storage performance guarantees
- Backup and replication services for disaster recovery scenarios
Manila shared file systems service adds NFS and CIFS capabilities, enabling legacy application support and cross-instance data sharing.
What APIs and Orchestration Tools Does OpenStack Offer?
OpenStack’s RESTful APIs provide programmatic access to all platform capabilities, enabling infrastructure as code practices and third-party tool integration. Each service exposes consistent API patterns following OpenStack’s design principles.
Heat orchestration service uses templates to automate infrastructure deployment and management. The service supports both native Heat Orchestration Templates (HOT) and AWS CloudFormation template formats for cross-platform compatibility.
API and automation features of OpenStack include:
- Comprehensive REST APIs for all services with consistent authentication
- Infrastructure templates for repeatable deployment patterns
- Workflow automation through Mistral for complex operational procedures
- Policy-based governance ensuring compliance across automated processes
The platform’s SDK and CLI tools support multiple programming languages, enabling seamless integration with existing development and operations workflows.
Proxmox vs OpenStack: Backup & High Availability
Data protection and service continuity are critical operational requirements where both platforms take fundamentally different approaches. Proxmox emphasizes simplicity and integrated backup solutions that work out-of-the-box, while OpenStack provides enterprise-grade flexibility through distributed services and pluggable architectures. Knowing these differences helps organizations choose the platform that better aligns with their operational complexity tolerance and reliability requirements.
How Does Proxmox Handle Backup Operations?
Proxmox provides integrated backup capabilities using the Proxmox Backup Server, delivering enterprise-grade data protection without requiring external backup software. The system performs incremental backups with built-in deduplication and compression, minimizing storage overhead and backup windows.
Snapshot-based backups leverage underlying storage system capabilities, enabling consistent backups of running virtual machines without performance impact. The backup system supports cross-node replication, ensuring data protection survives complete node failures.
Proxmox backup features include:
- Automated backup scheduling with retention policies and cleanup
- Incremental backups with client-side deduplication and encryption
- Instant recovery capabilities for rapid restoration scenarios
- Cross-platform compatibility supporting migration between different Proxmox clusters
The unified management interface handles backup configuration, monitoring, and restoration through the same web dashboard used for VM management, reducing operational complexity.
What Backup Approaches Does OpenStack Support?
OpenStack treats backup as a distributed challenge requiring coordination between multiple services. The platform supports various backup strategies through different service combinations, enabling organizations to choose approaches that match their scale and complexity requirements.
Volume backups integrate with enterprise backup systems and cloud storage providers through Cinder, while Swift object storage serves as a backup target for both local and remote data protection scenarios. Each OpenStack service typically requires its own backup strategy, creating operational complexity but also providing granular control over data protection policies.
Third-party integration with enterprise backup platforms like Veeam and Commvault is common in production deployments. Organizations often leverage existing backup infrastructure rather than building OpenStack-native solutions. Cross-region replication capabilities enable geographically distributed disaster recovery, although this does require careful network and storage planning.
The Freezer backup service (community project) provides additional backup orchestration capabilities, even if many organizations prefer integrating with existing enterprise backup infrastructure. API-driven automation enables custom backup workflows and policies, allowing organizations to build backup processes that integrate with their existing operational frameworks.
How Do High Availability Approaches Differ Between Platforms?
Proxmox HA focuses on simplicity with automatic VM restart capabilities when cluster nodes fail. The system uses proven clustering technology (corosync/pacemaker) to provide reliable failover for mission-critical workloads without complex configuration.
OpenStack HA requires architecting multiple service components for redundancy. Each OpenStack service must be configured for high availability individually, involving load balancers, database clustering, and message queue redundancy.
The highlights of comparison between their approaches to high availability include:
- Proxmox approach – Integrated HA with minimal configuration complexity
- OpenStack approach – Distributed HA requiring extensive architectural planning
- Recovery speed – Proxmox typically faster due to simpler architecture
- Customization options – OpenStack offers more granular HA control
Complexity trade-offs become apparent in HA implementations: Proxmox delivers reliable HA with minimal effort, while OpenStack provides extensive customization options that require significant expertise to implement correctly.
How Do Proxmox and OpenStack Manage Virtual Machines and Containers?
Virtual machine and container management represents a fundamental operational difference between these platforms, reflecting their distinct design philosophies and target use cases. Proxmox delivers unified management for both VMs and containers through a single interface, emphasizing operational simplicity and rapid deployment. OpenStack takes a more service-oriented approach where different components handle various aspects of workload management, providing granular control at the cost of increased complexity.
How Do VM Lifecycle Operations Compare?
Proxmox VM management centers around simplicity and direct control. Administrators create, configure, and manage virtual machines through an intuitive web interface that handles all aspects of the VM lifecycle. Template creation and cloning operations are straightforward, enabling rapid deployment of standardized configurations.
The platform provides integrated tools for VM monitoring, performance tuning, and resource allocation adjustments. Live migration between cluster nodes requires minimal configuration, making maintenance operations seamless for administrators.
OpenStack VM lifecycle involves coordination between multiple services. Nova handles compute scheduling and hypervisor management, while Glance manages VM images and templates. Neutron configures networking, and Cinder attaches storage volumes, creating a more complex but highly customizable deployment process.
Image management differs significantly between platforms. Proxmox uses simple template systems that administrators create from existing VMs, while OpenStack maintains a centralized image repository with versioning, metadata management, and multi-format support. This complexity provides advantages for large-scale deployments but adds operational overhead for smaller environments.
What Container Support Options Are Available?
Proxmox container integration focuses on LXC (Linux Containers) management alongside KVM virtual machines. The unified interface allows administrators to choose between full virtualization and container-based deployment based on workload requirements, optimizing resource utilization without separate management tools.
Container templates in Proxmox provide pre-configured environments for common applications and operating systems. Resource allocation for containers uses the same familiar interface as VM management, reducing the learning curve for teams transitioning from traditional virtualization.
OpenStack container approaches involve multiple strategies depending on organizational requirements. The Magnum service creates and manages Kubernetes clusters, while Zun provides direct container management capabilities. Heat orchestration templates help automate complex container deployments across multiple nodes.
Integration with container orchestration platforms like Kubernetes represents a strength of OpenStack’s architecture. With it, organizations would be able to deploy container infrastructure as code while leveraging OpenStack’s networking and storage services for underlying infrastructure management.
How Does Resource Allocation Differ Between Platforms?
Proxmox resource management operates through direct allocation models where administrators assign specific CPU cores, memory amounts, and storage volumes to individual workloads. The system provides real-time monitoring and adjustment capabilities without requiring complex quota systems or policy frameworks.
Overcommitment ratios and resource balancing happen automatically, though administrators retain full control over allocation policies. The clustering system ensures resources are utilized efficiently across available nodes while maintaining performance predictability.
OpenStack resource allocation employs sophisticated scheduling algorithms that consider multiple factors including availability zones, host aggregates, and custom scheduler filters. Quota systems provide multi-tenant resource controls, enabling organizations to allocate infrastructure resources based on business requirements rather than technical constraints.
Placement service optimization in recent OpenStack releases has improved resource scheduling efficiency, though this adds another layer of complexity that administrators must understand and configure properly for optimal performance.
Storage Management: Proxmox vs OpenStack
Storage architecture decisions fundamentally impact performance, scalability, and operational complexity in virtualized environments. Proxmox emphasizes proven storage technologies with straightforward configuration, while OpenStack provides extensive abstraction layers that support virtually any enterprise storage system. These different approaches reflect each platform’s target audience: Proxmox prioritizes reliable storage that administrators would be able to deploy quickly, while OpenStack focuses on flexibility and integration with complex enterprise storage infrastructures.
What Storage Types are Supported by Proxmox and OpenStack?
Proxmox storage integration focuses on widely-adopted technologies that provide reliable performance without extensive configuration overhead. The platform natively supports local storage, ZFS pools, Ceph distributed storage, and traditional network storage protocols including NFS and iSCSI.
ZFS integration stands out as a particular strength, offering advanced features like snapshots, compression, and checksums directly within the Proxmox interface. Ceph integration provides distributed storage capabilities for organizations requiring scalable, redundant storage across multiple nodes.
OpenStack storage support operates through pluggable backend architecture that accommodates over 80 different storage systems. Cinder block storage supports everything from basic LVM configurations to enterprise SAN arrays, software-defined storage platforms, and hyper-converged infrastructure.
The driver ecosystem enables integration with storage vendors including NetApp, Dell EMC, HPE, Pure Storage, and numerous open-source projects. This flexibility allows organizations to leverage existing storage investments while gaining cloud-native capabilities, though it requires expertise in both OpenStack and the chosen storage backend.
How Do Object, Block, and Image Storage Compare Between Proxmox and OpenStack?
Proxmox storage model treats different storage types as backend variations managed through a unified interface. Virtual machine disks use block storage, while backup operations leverage object storage targets. Container storage operates through the same mechanisms as VM storage, simplifying operational procedures.
Image management in Proxmox uses straightforward template systems where administrators create reusable VM templates from existing installations. These templates integrate directly with the storage backend, enabling rapid deployment without complex image distribution mechanisms.
OpenStack storage architecture provides distinct services for each storage type, enabling specialized optimization but requiring coordination between multiple components. Swift object storage delivers scalable, distributed storage comparable to Amazon S3, while Cinder block storage provides persistent volumes for compute instances.
Glance image service maintains centralized repositories with versioning, metadata management, and distribution capabilities across multiple availability zones. This separation enables advanced features like image deduplication and multi-format support, but adds operational complexity compared to simpler template systems.
Manila shared file systems service extends OpenStack’s storage capabilities to include NFS and CIFS protocols, supporting legacy applications that require shared storage access patterns. This comprehensive approach covers virtually any storage requirement but requires understanding multiple service interactions.
What Performance and Resilience Capabilities Exist in OpenStack and Proxmox?
Proxmox performance optimization relies on proven storage technologies and straightforward configuration options. ZFS provides built-in compression and deduplication, while Ceph delivers distributed performance scaling across multiple nodes.
Live migration capabilities work seamlessly with shared storage systems, enabling zero-downtime maintenance without complex storage coordination. Snapshot operations integrate directly with the storage backend, providing consistent backup points without impacting running workloads.
OpenStack performance management operates through quality-of-service policies and backend-specific optimization features. Storage QoS controls enable administrators to guarantee performance levels for specific workloads or tenant groups.
Multi-backend configurations allow organizations to implement tiered storage architectures where high-performance workloads use SSD-based backends while archival data resides on cost-optimized storage systems. This flexibility requires careful planning but enables sophisticated storage strategies that match business requirements to infrastructure costs.
Networking Comparison Between Proxmox and OpenStack
Network architecture choices have a significant impact on deployment complexity, performance, and integration capabilities of virtualized environments. Proxmox delivers straightforward networking that covers common virtualization scenarios without extensive configuration overhead, while OpenStack provides comprehensive software-defined networking capable of supporting entire enterprise network infrastructures. These approaches reflect fundamentally different assumptions about organizational networking requirements and available expertise.
How Does Proxmox Handle Network Configuration?
Proxmox networking operates using familiar Linux networking concepts including bridges, bonds, and VLANs. Administrators configure network interfaces with the web interface and standard networking terminology, making the platform accessible to teams with traditional virtualization experience.
Bridge networking connects virtual machines to physical networks using standard Linux bridge configurations. VLAN support enables network segmentation without requiring external VLAN configuration, though integration with existing VLAN infrastructure requires coordination with network teams.
Network bonding provides link aggregation and redundancy using proven technologies like LACP. The system handles failover automatically while maintaining network connectivity during hardware failures or maintenance operations.
Built-in firewall capabilities operate at both the host and guest levels, providing security controls without requiring separate firewall appliances for basic protection scenarios.
What Advanced Networking Does OpenStack Provide?
OpenStack Neutron delivers enterprise-grade software-defined networking capable of replacing traditional network infrastructure. The plugin architecture supports integration with hardware SDN controllers, traditional networking equipment, and cloud-native networking solutions.
Multi-tenant networking provides complete isolation between different organizational units or customers. Each tenant has the power to create virtual networks, routers, and security groups without impacting other tenants or requiring manual network administration intervention.
Advanced networking capabilities include:
- Load balancing as a service – Automated load balancer provisioning and management
- VPN connectivity – Site-to-site and remote access VPN services
- Distributed virtual routing – East-west traffic optimization within data centers
- Security groups – Stateful firewall rules applied at the hypervisor level
Quality of Service policies enable bandwidth guarantees and traffic prioritization, supporting demanding applications with specific network performance requirements.
How Do External Integration Options Compare?
Proxmox external networking relies on standard protocols and interfaces that integrate with existing network infrastructure. VLAN trunking enables integration with enterprise switching infrastructure, while routing protocols like BGP are configured with Proxmox hosts for advanced scenarios.
Network monitoring integrates with existing SNMP-based tools, enabling organizations to extend current monitoring practices to cover virtualized infrastructure without requiring specialized monitoring platforms.
OpenStack network integration operates through sophisticated plugin architectures that support virtually any networking vendor. ML2 plugin framework enables integration with Cisco ACI, VMware NSX, Juniper Contrail, and numerous open-source SDN solutions.
API-driven automation allows network changes to be orchestrated alongside compute and storage provisioning, enabling true infrastructure-as-code practices for complex networking scenarios. This integration capability supports advanced use cases like automated network policy enforcement and dynamic security group management.
What are the Strengths of Proxmox and OpenStack Comparatively?
Understanding each platform’s core advantages helps organizations align technology choices with business objectives and operational realities. Instead of declaring one platform superior, we aim to recognize specific strengths and enable informed decisions based on actual requirements, team capabilities, and growth trajectories.
With that being said, the choice between these platforms often comes down to prioritizing operational simplicity versus comprehensive functionality. Here are some of the most notable strengths of both solutions in the form of a table for comparison:
| Aspect |
Proxmox |
OpenStack |
| Deployment Speed |
Hours to days |
Weeks to months |
| Learning Curve |
Low – familiar concepts |
High – specialized skills |
| Scalability |
Up to ~100 nodes |
Thousands of nodes |
| Multi-tenancy |
Basic isolation |
Enterprise-grade |
| API Automation |
REST API available |
Comprehensive APIs |
| Operational Overhead |
Low maintenance |
High expertise required |
Where Does Proxmox Excel?
Operational simplicity stands as Proxmox’s greatest asset. Teams deploy production-ready virtualization infrastructure within hours rather than weeks, making it ideal for organizations that need reliable results without extensive planning phases. The learning curve remains manageable for administrators with traditional virtualization experience.
Cost-effectiveness extends beyond the absence of licensing fees. Smaller teams manage larger infrastructures due to the platform’s intuitive design and integrated tooling. This efficiency translates into lower operational costs and faster time-to-value for virtualization projects.
Proxmox shines in scenarios requiring quick deployment and reliable performance. The platform’s mature technology foundation builds using proven components like KVM, LXC, and ZFS, reducing the risk of encountering unexpected issues in production environments.
Cluster management requires minimal specialized knowledge. Adding nodes, configuring high availability, and performing maintenance operations follow straightforward procedures that don’t require deep understanding of distributed systems architecture.
What are OpenStack’s Key Advantages?
Enterprise-scale capabilities position OpenStack as the platform of choice for organizations operating at cloud provider scale. Multi-tenancy support enables complex organizational structures with complete isolation between departments, business units, or external customers.
API consistency across all services creates powerful automation opportunities. Infrastructure-as-code practices become practical when every component is managed programmatically, enabling sophisticated deployment and management workflows that scale with organizational growth.
Vendor neutrality protects against technology lock-in while enabling best-of-breed component selection. Organizations are free to choose optimal solutions for compute, storage, and networking without being constrained by single-vendor ecosystems.
The platform’s service-oriented architecture supports incremental adoption and customization. Teams implement only needed services initially, then expand capabilities as requirements evolve:
- Modular deployment – Start with basic compute and storage, add advanced services later
- Component substitution – Replace individual services without affecting others
- Custom integration – Develop organization-specific services using standard APIs
- Gradual migration – Move workloads incrementally from existing infrastructure
Community-driven development ensures long-term viability and feature evolution aligned with industry needs rather than vendor priorities. This collaborative approach produces solutions that address real-world operational challenges across diverse deployment scenarios.
Cost Structures: Proxmox vs OpenStack
Financial considerations extend far beyond initial software licensing, encompassing operational overhead, staffing requirements, and long-term maintenance costs. Organizations often discover that apparent cost savings disappear when factoring in deployment complexity, training needs, and ongoing management requirements. Smart financial planning examines total cost of ownership rather than focusing solely on upfront expenses.
How Do Licensing and Support Models Compare?
Proxmox operates on a freemium model where the core platform remains completely free for unlimited use. Organizations deploy production environments without licensing fees, paying only for optional enterprise support and additional features like the backup server’s advanced capabilities.
Enterprise subscriptions start at reasonable rates per CPU socket, providing access to tested repositories, security updates, and professional support channels. This model scales predictably with hardware growth, making budget planning straightforward for expanding organizations.
OpenStack’s open-source nature eliminates licensing costs entirely, but professional deployment typically requires commercial distributions or consulting services. Red Hat OpenStack Platform, SUSE OpenStack Cloud, and other enterprise distributions charge substantial licensing fees based on CPU cores or instances.
Support economics favors organizations with strong internal expertise. Companies capable of managing OpenStack deployments internally avoid distribution costs, while those requiring external support face significant ongoing expenses for specialized consulting and managed services.
What Operational Overhead Differences Exist?
Staffing requirements diverge dramatically between platforms. Proxmox deployments are managed by traditional virtualization administrators with minimal additional training, allowing existing teams to expand their responsibilities without hiring specialized personnel.
Time-to-productivity remains low for Proxmox, where administrators become proficient within weeks rather than months. Basic operations like VM provisioning, backup configuration, and cluster management follow intuitive patterns that don’t require extensive documentation or training programs.
OpenStack demands specialized expertise across multiple domains including distributed systems, software-defined networking, and API development. Building internal capability requires significant training investments or hiring experienced OpenStack engineers commanding premium salaries.
Deployment complexity impacts ongoing costs through extended project timelines and consultant requirements. Organizations frequently underestimate the time and expertise needed for production-ready OpenStack deployments, leading to budget overruns and delayed implementations.
Maintenance operations in OpenStack environments require coordinated updates across multiple services, often necessitating dedicated DevOps teams familiar with the platform’s architectural nuances.
What Hidden Costs Should Organizations Consider?
Infrastructure requirements differ substantially between platforms. Proxmox runs efficiently on modest hardware configurations, while OpenStack’s distributed architecture requires additional servers for controller nodes, network nodes, and service redundancy.
Training investments become significant factors in OpenStack deployments. Teams need education on cloud-native concepts, API automation, and troubleshooting distributed systems. These skills take time to develop and may require external training programs or conference attendance.
Integration complexity drives unexpected consulting costs on its own. Organizations with existing enterprise infrastructure often require specialized expertise to integrate OpenStack with legacy systems, backup solutions, and monitoring platforms.
Development overhead emerges when organizations attempt to customize OpenStack deployments beyond standard configurations. Custom automation, specialized drivers, or organization-specific features require ongoing development resources that many organizations underestimate during initial planning phases.
What are the Primary Use Cases Proxmox vs OpenStack?
Real-world deployment scenarios reveal where each platform delivers optimal value. Organizations achieve success when platform capabilities align with actual requirements rather than theoretical needs. Examining specific use cases helps clarify which technology choices support business objectives while remaining within operational capabilities and budget constraints.
When Do Small and Medium-Sized Businesses Benefit Most?
Resource constraints typically favor Proxmox for SMB environments where IT teams handle multiple responsibilities and need reliable solutions that don’t consume excessive time or specialized expertise. Companies with 50-500 employees tend to find that Proxmox’s integrated approach matches their operational reality better than complex distributed systems.
Development environments represent ideal Proxmox use cases. Software teams quickly provision test systems, create development sandboxes, and manage CI/CD (continuous integration/continuous deployment) infrastructure without dedicated cloud platform expertise. The platform’s template system accelerates developer productivity while keeping infrastructure costs predictable.
Branch office virtualization scenarios play to Proxmox’s strengths in environments requiring local compute resources with centralized management. Remote locations benefit from simplified deployment and maintenance procedures that don’t require on-site OpenStack expertise.
Small hosting providers and managed service providers often choose Proxmox for its straightforward multi-tenancy and billing integration capabilities. The platform provides sufficient isolation for customer workloads without the operational complexity that larger cloud platforms introduce.
Which Large-Scale Deployments Favor OpenStack?
Service provider infrastructure demands the multi-tenancy, API automation, and billing integration that OpenStack delivers at scale. Telecommunications companies building NFV (network function virtualization) platforms consistently choose OpenStack for its ability to handle thousands of concurrent tenants with complete resource isolation.
Enterprise private clouds requiring integration with complex existing infrastructure benefit from OpenStack’s extensive plugin ecosystem. Large organizations with heterogeneous storage, networking, and security systems leverage existing investments while gaining cloud-native capabilities.
Research institutions and universities deploy OpenStack for its ability to handle diverse workload types and provide self-service capabilities to multiple departments or research groups. The platform’s quota systems and project isolation support complex organizational structures with varying resource requirements.
Government agencies and regulated industries choose OpenStack when compliance requirements mandate complete control over infrastructure components. The platform’s transparency and auditing capabilities support regulatory compliance while providing cloud-like functionality.
Where Do Hybrid and Edge Scenarios Fit?
Edge computing deployments increasingly favor Proxmox for remote locations requiring minimal operational overhead. Manufacturing facilities, retail locations, and IoT gateways benefit from virtualization capabilities that don’t require constant connectivity to centralized management systems.
Multi-cloud strategies often incorporate both platforms in complementary roles. Organizations use OpenStack for core private cloud infrastructure while deploying Proxmox at edge locations or for specific workloads requiring simplified management.
Hybrid integrations with public cloud providers work differently for each platform:
- Proxmox hybrid – Direct integration with cloud storage and backup services
- OpenStack hybrid – API compatibility with AWS and Azure for workload portability
- Disaster recovery – Proxmox focuses on backup/restore, OpenStack enables infrastructure replication
Container orchestration scenarios see OpenStack providing underlying infrastructure for Kubernetes clusters, while Proxmox often runs container workloads directly through LXC integration. This difference influences architecture decisions for organizations adopting containerized applications.
What are Important Migration Considerations for OpenStack and Proxmox?
Platform transitions involve substantial technical and business risks that extend beyond simple data movement. Organizations must evaluate migration complexity against expected advantages while also planning for potential disruptions to current business operations. Successful migrations require a careful assessment of all existing workloads, team capabilities, and even acceptable downtime windows.
What Does Moving from Proxmox to OpenStack Involve?
Infrastructure expansion becomes necessary when migrating to OpenStack’s distributed architecture. Organizations typically need additional servers for controller nodes, network nodes, and service redundancy, increasing hardware requirements beyond current Proxmox deployments.
Skill development is a major migration challenge. Teams familiar with Proxmox’s integrated approach would have to learn distributed systems concepts, API automation, and service coordination patterns that don’t exist in simpler virtualization platforms.
VM migration procedures vary greatly depending on storage backend compatibility. Shared storage environments enable somewhat straightforward migrations using standard tools, while local storage scenarios require more complex data movement processes and extended downtime windows.
Network reconfiguration often proves more disruptive than anticipated. OpenStack’s software-defined networking requires different approaches to VLAN management, routing, and security policies that may conflict with existing network architectures.
Testing phases would need to include complete application stacks rather than just individual VMs. Yet, application dependencies on specific network configurations or storage behaviors may not become apparent until full workload testing occurs in the new environment.
How Complex Is OpenStack to Proxmox Migration?
Simplification opportunities make this migration direction potentially attractive for organizations struggling with OpenStack’s operational complexity. Proxmox’s integrated approach reduces operational overhead while maintaining core virtualization capabilities.
Service consolidation challenges arise when OpenStack’s distributed services must be mapped to Proxmox’s unified architecture. Organizations using advanced OpenStack features like Heat orchestration or complex Neutron networking may need to redesign workflows for simpler alternatives.
Data extraction from OpenStack environments requires careful planning to preserve VM configurations, network settings, and storage mappings. The migration process often involves recreating infrastructure patterns rather than direct translation between platforms.
Cost analysis becomes crucial during this migration type. Organizations should verify that Proxmox’s capabilities meet their actual requirements rather than assumed needs that drove initial OpenStack adoption.
What Compatibility Issues and Risks Should Teams Anticipate?
Hypervisor compatibility generally remains consistent since both platforms support KVM, enabling VM migrations without guest operating system changes. However, virtual hardware configurations may require adjustment to accommodate different default settings between platforms.
Storage backend changes pose the biggest risk during migrations. Organizations using OpenStack-specific storage features like Cinder volume types or Swift object storage must plan alternative solutions or accept functionality changes.
Automation workflows rarely transfer directly between platforms due to different API structures and management approaches. Organizations have to budget time for rewriting deployment scripts, monitoring configurations, and operational procedures.
Backup and disaster recovery strategies require complete reevaluation during platform migrations. Existing backup solutions may not support the target platform, necessitating changes to data protection procedures and recovery testing:
- Backup tool compatibility – Verify current solutions support the target platform
- Recovery procedures – Test restoration processes in new environments
- Retention policies – Ensure compliance requirements remain met during transition
- Cross-platform recovery – Plan for potential rollback scenarios
Network dependencies on specific OpenStack services – load balancers or floating IP pools – may require architectural changes that impact application connectivity patterns. Application teams should participate in migration planning to identify potential service disruptions.
Final Thoughts
The choice between Proxmox and OpenStack ultimately depends on organizational priorities, not technical superiority.
Proxmox excels in environments where simplicity, rapid deployment, and cost-effectiveness take precedence over comprehensive feature sets. Its integrated approach delivers reliable virtualization with minimal operational overhead, making it ideal for small to medium-sized organizations or specific use cases requiring straightforward management.
OpenStack serves organizations that prioritize flexibility, scalability, and enterprise-grade features over operational simplicity. The platform’s comprehensive service catalog and extensive customization options support complex requirements that justify the associated complexity and resource investments. Success with OpenStack requires substantial expertise and commitment to distributed systems management.
Both platforms are mature, production-ready solutions that serve as foundations for robust virtualization infrastructure. The decision should align with current team capabilities, growth projections, and tolerance for operational complexity instead of attempting to choose the “best” platform in isolation.
Key Takeaways
- Proxmox prioritizes simplicity and cost-effectiveness, making it ideal for SMBs and straightforward virtualization scenarios
- OpenStack delivers enterprise-scale capabilities with comprehensive multi-tenancy and API automation for large organizations
- Total cost of ownership differs significantly – Proxmox minimizes operational overhead while OpenStack requires specialized expertise
- Migration between platforms involves substantial complexity and should be carefully evaluated against actual business benefits
- Storage and networking approaches reflect each platform’s philosophy – integrated simplicity versus distributed flexibility
- Both platforms support production workloads effectively when properly matched to organizational requirements and capabilities
Frequently Asked Questions
Does Proxmox Scale to Thousands of Nodes?
Proxmox does technically scale to hundreds of nodes within a single cluster, but performance and management complexity increase significantly beyond 50-100 nodes. For deployments that require thousands of nodes, OpenStack’s distributed architecture provides better scaling characteristics and operational tools. Organizations needing massive scale should evaluate whether Proxmox’s simplicity benefits justify potential scaling limitations.
Is Proxmox a Full Replacement for OpenStack?
Proxmox serves as a replacement for basic OpenStack deployments focused on compute and storage virtualization. However, OpenStack’s advanced features like multi-tenancy, comprehensive API automation, and enterprise service catalog extend far beyond Proxmox’s capabilities. Organizations need to evaluate their actual requirements rather than assuming feature parity between platforms.
How Do Disaster Recovery Approaches Differ Between OpenStack and Proxmox?
Proxmox emphasizes backup-based disaster recovery through its integrated Proxmox Backup Server with cross-site replication capabilities. OpenStack supports more sophisticated disaster recovery strategies including live site replication, automated failover, and infrastructure-as-code restoration. The final choice depends on recovery time objectives and acceptable complexity for disaster recovery operations.
 The SC25 conference (officially known under the name of International Conference for High Performance Computing, Networking, Storage, and Analysis) is taking place from November 16 to 21, 2025, in St. Louis, Missouri. It is a special event that operates as a global hub for professionals of the supercomputing community, such as researchers, scientists, educators, engineers, programmers, and developers.
The SC25 conference (officially known under the name of International Conference for High Performance Computing, Networking, Storage, and Analysis) is taking place from November 16 to 21, 2025, in St. Louis, Missouri. It is a special event that operates as a global hub for professionals of the supercomputing community, such as researchers, scientists, educators, engineers, programmers, and developers.
Visit Bacula Systems at Booth 839
Join us at Booth 839 during SC25 to discover how Bacula Systems is revolutionizing enterprise backup and data protection solutions for high-performance computing environments. Our team of experts are going to be stationed on-site in order to demonstrate our cutting-edge backup technologies and discuss how we can help optimize your data management strategies.
What to Expect at SC25
The conference promises an entire week of sessions and networking opportunities, along with an exhibition, to foster innovation and collaboration using a leading technical program that showcases best practices across different areas of HPC and AI. It is comprised of several different elements and components, such as:
- Workshops – aiming to spark innovation and professional growth by going beyond the boundaries of traditional presentations
- Exhibits – capability to interact with various industry leaders, as well as research organizations, startups, and universities, all of which showcase different forms of cutting-edge technologies or services
- Students@SC Program – volunteer experiences, cluster competitions, and networking opportunities specifically for student audiences, helping them with advancing their professional development specifically in the HPC field.
- SCinet – granting advanced internet connectivity for attendees, operating as a volunteer-driven effort but also showcasing the latest advancements in network innovation
Why Meet with Bacula Systems?
At Booth 839, you will have the opportunity to:
- Explore our latest enterprise backup and recovery solutions designed for HPC environments
- Discuss your specific data protection challenges with our technical experts
- Learn about scalable backup strategies for large-scale computing infrastructures
- Discover how exactly Bacula Systems can help reduce your total cost of ownership
- See the live demonstrations of our backup software in action
Supporting Quantum Research with Reliable Backup
Quantum Computing is rapidly becoming a priority for universities, labs, and government research centers worldwide. Bacula secures the HPC and IT infrastructures driving these initiatives, ensuring resilience, scalability, efficiency, and predictable costs for the future of computing.
Event Details
Location: America’s Center, downtown St. Louis, Missouri
Dates: November 16-21, 2025
Bacula Systems Booth: 839
Conference Sponsors: ACM and IEEE
The venue, America’s Center, is located close to the middle of downtown St. Louis, which offers easy access for all attendees to visit our booth and engage with the broader supercomputing community.
Schedule a Meeting
Don’t miss this opportunity to connect with Bacula Systems at SC25. You can stop by Booth 839 or contact us in advance to schedule a dedicated meeting with our team. We are looking forward to discussing all the different methods that our data protection solutions can use to support your high-performance computing initiatives.
What is OpenStack and How Does It Work?
OpenStack is one of the most comprehensive open-source cloud computing platforms available, created to help organizations manage private or cloud public infrastructures at scale. Originally developed by NASA and Rackspace in 2010, OpenStack has quickly evolved into a robust ecosystem capable of powering some of the world’s biggest cloud deployments, ranging from telecommunications giants to financial institutions.
Knowledge of OpenStack’s core architecture and business benefits is essential for any IT leader who is considering infrastructure modernization. In this section, we explore how OpenStack operates as a complete Infrastructure-as-a-Service (IaaS) solution, explaining its technical foundation and practical advantages for enterprise environments.
What is OpenStack?
OpenStack is an open-source cloud operating system that can control large pools of computing, storage, and networking resources throughout a datacenter. Unlike most proprietary cloud solutions, OpenStack gives organizations complete control over their cloud infrastructure while avoiding the issue of vendor-lock that plagues many enterprise IT departments.
At its core, OpenStack is a comprehensive orchestration platform capable of transforming commodity hardware into a dynamic, scalable cloud environment. The platform manages virtual machines, containers, and bare metal servers using a unified dashboard and API framework. This allows administrators to provision resources on-demand and also maintain granular control over security policies and resource allocation.
Key characteristics that define OpenStack are:
- Multi-tenancy support allowing different departments and customers to share infrastructure, while remaining completely isolated from each other
- Vendor-neutral architecture capable of working with hardware from different manufacturers
- API-driven management offers automation and integration capabilities with existing enterprise tools
- Modular design allows deployment of only the services needed in each specific situation
The platform supports a wide range of hypervisors, including KVM, Xen, VMware ESXi, and Hyper-V, giving its clients flexibility in underlying virtualization choices. For enterprises that are currently evaluating cloud strategies, OpenStack is a compromise between public cloud services and traditional on-premises infrastructure. Organizations that use OpenStack gain cloud-like agility and scalability but maintain complete control over data location, security policies, and compliance requirements.
How Does OpenStack Architecture Enable Cloud Infrastructure?
OpenStack’s architecture follows a distributed, service-oriented design, separating cloud functions into independent components that connect with each other. A modular approach allows organizations to scale the specific services, based on demand, while maintaining overall system reliability.
The architecture uses a three-tier model, with controller nodes managing API requests and orchestration tasks, compute nodes handling virtual machine execution, and making networking nodes responsible for managing traffic routing. This separation enables horizontal scaling, giving organizations the ability to add capacity using additional nodes instead of performing expensive hardware upgrades.
The RESTful API framework is paramount for OpenStack’s structure, providing programmatic access to every single function of the platform. These APIs offer integration with existing enterprise tools and automation frameworks. Consistency in API design also means that understanding the interface of one service helps developers adapt to the interface of others much more quickly.
OpenStack’s Identity service uses a role-based access control (RBAC) , which allows administrators to define granular permissions for different user groups. The platform’s plugin architecture allows third-party vendors to integrate their solutions directly into OpenStack’s workflow. Notable examples of these direct integrations include storage vendors providing drivers, networking companies integrating CDN solutions, and monitoring tools gaining access to telemetry data.
High availability is at the core of the platform’s design, achieved with the help of automated failover capabilities and overall service redundancy. Critical services run across multiple controller nodes with constant health monitoring capable of automatically routing traffic away from failed components if necessary.
What are OpenStack’s Essential Components and Services?
OpenStack includes a number of services that operate together to provide comprehensive cloud functionality. The core services include:
- Nova – Compute services managing VMs and bare metal
- Neutron – Networking with virtual networks and load balancers
- Cinder – Block storage with encryption and snapshots
- Swift – Object storage for unstructured data and backups
- Keystone – Identity and authentication service
- Glance – Virtual machine image management
- Heat – Orchestration for complex application deployments
- Horizon – Web-based dashboard interface
- Ceilometer – Telemetry and monitoring data collection
The complete visual overview of all OpenStack services and their relationships is available on OpenStack’s official website as the “OpenStack map”.
Of all these components, three that would typically be instrumental for any deployment: Nova, Neutron, and Keystone.
Nova handles all compute operations, managing virtual machine lifecycles and scheduling workloads using available hardware. It supports multiple hypervisors and allocates resources based on performance requirements and availability constraints.
Neutron is the networking backbone, enabling the complex network topologies on which modern applications rely. Its features include network segmentation, floating IP addresses, and integration with various networking vendors using its plugin architecture.
Keystone is the security foundation of the platform, managing user authentication and API endpoint discovery. It is easily integratable with enterprise directory services like Active Directory, enabling support for Single Sign-On (SSO) and consistent user management across the entire infrastructure.
What Key Benefits Does OpenStack Deliver for Enterprises?
OpenStack delivers substantial operational and strategic advantages for businesses that want to modernize their infrastructure while maintaining control over costs, security, and compliance requirements.
Primary enterprise benefits of the platform include:
- Cost Control – Eliminating recurring licensing fees from proprietary platforms
- Vendor Independence – Avoiding vendor lock-in by supporting hardware from different vendors
- Complete Infrastructure Control – Enabling custom security policies, regulatory compliance, and data sovereignty
- Unlimited Scalability – Supporting both horizontal and vertical scaling using additional nodes and hardware upgrades, respectively
- Development Acceleration – Providing self-service infrastructure access via APIs to shorten development cycles
- Hybrid Cloud Flexibility – Extending private environments to OpenStack-compatible public cloud providers for cost optimization and burst capacity
- Transferable Skills Investment – Applying knowledge gained directly to public cloud environments to protect training investments
OpenShift’s vendor-neutral approach is especially valuable during technology refresh cycles or whenever market conditions change vendor relationships. That way, organizations avoid the dependency issues that single-vendor strategies often introduce while maintaining enterprise-grade cloud capabilities.
As for more regulated industries, such as healthcare, finance, and government, OpenStack provides complete control over infrastructure, enabling compliance with legal requirements while still offering a wide range of modern cloud benefits to improve operational efficiency.
What is OpenShift and How Does It Work?
Red Hat OpenShift is the leading enterprise Kubernetes platform, designed to streamline container application development, deployment, and management in hybrid cloud environments. Built on Kubernetes, OpenShift adds enterprise-level security capabilities, as well as the developer productivity tools and operational automation that businesses need for production container workloads.
Understanding how OpenShift extends Kubernetes’ capabilities and simplifies container operations at the same time is important for development teams and IT leaders tasked with evaluating modern application platforms. This section explores the container platform architecture of OpenShift and its wide range of features.
What is OpenShift?
OpenShift is Red Hat’s enterprise-ready container platform, combining Kubernetes’ orchestration and integrated development tools with enhanced security and streamlined operations management. OpenShift provides a complete application platform to handle the entire container lifecycle, from development to production deployment, which is significantly different from plain-vanilla Kubernetes.
At its foundation, OpenShift uses Kubernetes as an orchestration engine, adding layers of functionality to it. The platform integrates container security, CI/CD (Continuous Integration and Continuous Delivery) pipelines, monitoring, logging, and networking into a unified experience that reduces operational complexity.
Core characteristics that define OpenShift include:
- Developer-focused workflows with built-in CI/CD, source-to-image builds, and integrated development environments
- Enterprise security by default, with role-based access control, network policies, and security context constraints
- Multi-cloud portability that supports deployment across on-premises, public cloud, and edge deployments
- Operator-based automation for managing application lifecycles and infrastructure operations
- Comprehensive observation capabilities with integrated monitoring, logging, and alerting capabilities
OpenShift also addresses the complexity gap between Kubernetes and enterprise requirements. While Kubernetes itself offers container orchestration primitives, OpenShift delivers the additional tooling, security, and operational features that all enterprises need, without the need to integrate dozens of separate tools manually.
The platform fully supports multiple deployment models, ranging from self-managed on-premises installations to managed cloud services (Azure Red Hat OpenShift, Red Hat OpenShift Service in AWS) and dedicated hosting options. This flexibility allows organizations to choose the deployment approach that best fits their operational capabilities.
How does the Container Platform Architecture of OpenShift Work?
OpenShift’s architecture builds upon Kubernetes, with additional enterprise features from Red Hat, maintaining full API compatibility and ensuring that existing Kubernetes applications can run without modification.
Key OpenShift-specific components include:
- OpenShift API server, which extends Kubernetes API with additional resource types and security policies
- OAuth server provides enterprise authentication integration with LDAP, Active Directory, and SAML
- Integrated image registry stores container images with automated vulnerability scanning and build triggers
- Security Context Constraints enforces granular security policies beyond basic Kubernetes Pod Security Standards
Worker nodes run OpenShift node agents alongside standard kubelets (the primary node agent in Kubernetes), providing improved security enforcement and integrated telemetry collection. OpenShift’s architecture supports deployment on virtual machines, bare metal, and public cloud infrastructure.
The built-in image registry scans container images automatically, looking for security vulnerabilities and integrating with source-to-image builds. This enables automated application deployments triggered by code commits and eliminates the need for external registry services and manual security scanning processes.
What Makes OpenShift Different from Kubernetes?
OpenShift provides substantial value-added capabilities that distinguish it from standard Kubernetes environments, addressing enterprise development and operational requirements without the need for using an extensive toolchain integration. These capabilities are:
- Security Beyond Kubernetes – Security Context Constraints (SCCs) grant granular control over container privileges, resource access, and volume types: capabilities that standard Pod Security Standards cannot match. Built-in OAuth integration provides connectivity with enterprise identity systems, such as LDAP or SAML for SSO, as well, whereas Kubernetes always requires separate authentication solutions.
- Complete Developer Platform – Unlike the infrastructure focus of Kubernetes, OpenShift offers integrated development workflows with source-to-image builds, built-in CI/CD pipelines, and developer self-service capabilities. To do that, Kubernetes users must employ separate tools, such as Jenkins, GitLab, or Tekton.
- Operational Simplicity – OpenShift’s web console incorporates comprehensive cluster and application management capabilities, unlike Kubernetes’ basic functionality. Built-in monitoring with Prometheus and Grafana (monitoring tools) eliminates the complex setup required for Kubernetes’ observability.
- Enterprise Support Model – Red Hat offers commercial support, certified integrations, and security patches using a single vendor relationship, which contrasts with Kubernetes’ community-driven support model, typically requiring multiple vendor relationships.
What are the Key Features of OpenShift?
OpenShift accelerates application development and simplifies container operations across the application lifestyle with integrated platform capabilities. The noteworthy features of the platform fall into three primary categories: development acceleration features, enterprise operations capabilities, and specialized workload support.
Development Acceleration Features of OpenShift
- Automated image builds from source code with secure and optimized container creation
- Integrated development environment with hot reloading capabilities and remote debugging
- Multi-language support with pre-configured runtimes for Java, Node.js, Python, .NET, Go, and PHP
- GitOps workflows that enable infrastructure-as-code and automated deployment pipelines
Enterprise Operations Capabilities of OpenShift
- Multi-cluster management for hybrid cloud or edge deployment strategies
- Operator ecosystem with automated application lifecycle management for databases, middleware, and custom applications
- Advanced networking includes service mesh integration, traffic management, and network policy enforcement
- Comprehensive security that offers vulnerability scanning, compliance reporting, and automated patch management
Specialized Workload Support of OpenShift
- Serverless computing with Knative (serverless framework) for event-driven, auto-scaling applications
- AI/ML workflows supporting GPU workloads and model training pipelines
- Edge computing capabilities for distributed application deployment
These integrated capabilities eliminate the complexity of assembling and maintaining separate toolchains, while also offering enterprise-grade reliability and support.
OpenStack vs. OpenShift: Key Differences and Use Cases
Although OpenStack and OpenShift are both enterprise-grade open-source platforms, they serve completely different purposes in modern IT infrastructures. OpenStack offers Infrastructure-as-a-Service capabilities for managing virtual machines, storage, and networking. OpenShift, on the other hand, focuses on Platform-as-a-Service (PaaS) for container application development and deployment.
A wide range of factors should be evaluated to know when each platform aligns with organizational needs, including existing infrastructure, development workflows, compliance requirements, and long-term technology strategy. This section explores each strategic decision criteria used to choose between the two platforms and examines scenarios in which the two can be used in tandem to create comprehensive cloud solutions.
When Should You Choose OpenStack for Your Organization?
OpenStack suits organizations that prioritize infrastructure control over application development speed, especially those with significant existing investments or regulatory constraints. Other noteworthy use cases are:
- Large-scale VM environments. Companies running hundreds of virtual machines across departments need OpenStack’s multi-tenant resource management and billing, which traditional virtualization platforms cannot offer with the same level of efficiency.
- Regulated industries. Healthcare, finance, and government organizations that require data residency, audit trails, and compliance frameworks can usually find public cloud services insufficient for their regulatory obligations.
- VMware replacement strategies. Organizations facing increases in licensing costs, seeking alternatives to proprietary virtualization with the aim of reusing existing hardware investment while gaining cloud capabilities.
- Established operations teams. A significant portion of infrastructure experts prefer OpenStack’s flexibility and customization over the restrictions of managed platforms, viewing operational complexity as an acceptable compromise for better architectural control.
When is OpenShift the Better Choice?
OpenShift excels for organizations that prioritize development velocity and application modernization over extensive infrastructure customization capabilities (especially companies with limited container expertise). There are several situations when OpenShift would be the best choice for businesses, such as:
- Digital transformation initiatives. Organizations that build new applications or modernize existing ones, benefitting from OpenShift’s automated deployment workflows and developer productivity tools to help reduce time-to-market pressures.
- Small to medium operations teams. Companies that lack deep Kubernetes knowledge have the option to leverage Red Hat’s enterprise container capabilities, instead of building internal expertise from scratch.
- Application-centric environments. Environments focusing on software delivery instead of infrastructure management, who may find OpenShift’s platform abstraction more valuable than infrastructure flexibility.
- Multi-cloud application deployment. Businesses that run applications across different cloud providers and need consistent operational models.
Can OpenStack and OpenShift Work Together?
OpenStack and OpenShift complement each other effectively when organizations need a combination of infrastructure flexibility and application platform capabilities in integrated environments. These cases can use a layered deployment model, with OpenStack managing underlying compute, storage, and networking resources while OpenShift orchestrates containers and development tools to create comprehensive cloud capabilities.
Other common integration scenarios of OpenStack and OpenShift include:
- Hybrid enterprises that use OpenStack for compliance-sensitive workloads and OpenShift, for modern application development
- Service providers that leverage OpenStack for multi-tenant infrastructure and OpenShift for managed application services
- Large organizations running OpenStack for departmental resource allocation and OpenShift for shared development platforms
- Edge deployments combining OpenStack’s infrastructure provisioning with OpenShift’s distributed application management
Success in hybrid approaches requires precise coordination between infrastructure and platform teams to optimize resource utilization and maintain operational consistency at the same time.
Deployment and Management Considerations of OpenStack and OpenShift
Successful deployment and ongoing management of OpenStack or OpenShift requires careful planning around complexity, resource requirements, and operational expertise. OpenStack demands extensive infrastructure planning and specialized expertise, but OpenShift grants more streamlined deployment with application-focused management. These operational differences are instrumental when it comes to assessing implementation timelines or staffing needs before committing to any platform.
How Do Deployment Complexity and Requirements Compare Between OpenStack and OpenShift?
OpenStack requires 3-6 months for production deployment, due to the extensive architectural decisions that need to be conducted around service selection, network design, and high availability configuration. Every deployment of OpenStack needs custom planning of hardware integration and compatibility with the existing infrastructure.
OpenShift’s deployment timeline varies significantly depending on the approach chosen. Managed services often achieve production readiness in the matter of days, but self-managed installations take at least several weeks to deploy. The platform’s opinionated defaults reduce complexity but also become a limiting factor when it comes to customization, compared to OpenStack’s capabilities.
Critical differences in deployment between the two platforms are summarized below:
- Planning. OpenStack demands detailed service architecture design; OpenShift provides guided installation with reasonable default presets
- Integration. OpenStack requires extensive system integration to operate properly; OpenShift is much more focused on application-layer connections that simplify integration
- Production. OpenStack’s production timeline takes up to a year in total; OpenShift achieves production within a few reasonable months
What Infrastructure and Expertise Does Each Platform Need?
The requirements of both platforms for expertise vary significantly, with OpenStack demanding dedicated infrastructure specialists as the baseline. OpenShift, on the other hand, is often content with the addition of application-focused engineers who can grow into platform operations as time goes on.
As for the infrastructure requirements – OpenStack requires:
- Hardware scale – 10+ servers as production requirements, but it is possible to work with 3-5 strictly for testing purposes
- Network complexity – Multiple VLANs with a potential SDN (Software-Defined Networking) integration
- Storage – Dedicated nodes or SAN/NAS integration are a necessity
- Team skills – Deep Linux administration, experience with networking, virtualization, and knowledge about database management
Alternatively, OpenShift’s infrastructure requirements are:
- Smaller footprint – 3-node clusters are the starting point for most, with simple scalability when necessary
- Standard networking – Basic Kubernetes networking with optional service mesh
- Storage flexibility – Either CSI driver integration or cloud provider storage
- Team skills – Knowledge of Kubernetes/container systems, expertise in CI/CD pipeline management, and application deployment skills
How Do Ongoing Management of OpenStack Differ from OpenShift?
OpenStack operations focus on infrastructure maintenance, including distributed service updates, capacity planning, and hardware lifecycle management. Teams must devote time to troubleshooting component interactions and require custom automation capabilities for more complex tasks. Ongoing management relies substantially on command-line tools with dashboards, primarily for monitoring purposes.
OpenShift operations revolve around application support and cluster health. Platform teams manage automated cluster updates while ensuring consistency in deployment experiences. The web console of the platform offers comprehensive management tools and convenient automation capabilities for routine tasks.
Both platforms also have their own approaches to operations scaling. OpenStack relies on manual capacity planning, hardware procurement, and node integration. OpenShift uses automated node provisioning with dynamic resource allocation capabilities using cloud provider integration.
Continuous attention to infrastructure is a requirement in OpenStack environments. On the other hand, OpenShift’s managed complexity makes it possible to focus more on application support instead of conducting low-level system maintenance manually.
Cost Analysis and Licensing Models of OpenStack and OpenShift
Knowledge of both fundamental cost structures and licensing approaches of both OpenStack and OpenShift are essential for accurate budget planning and long-term financial strategy. Even though both platforms serve enterprise needs, they use different economic models, significantly impacting both initial investments, and ongoing operational expenses and Total Cost of Ownership (TCO) calculations.
OpenStack’s open-source foundation eliminates licensing fees but requires significant investment in both expertise and ongoing support. OpenShift’s subscription model offers predictable costs with comprehensive support from the vendor. In this section, we examine the cost factors, licensing structures, and economic considerations of both solutions, to assist with platform selection and budget allocation decisions.
What Does OpenStack Cost to Deploy and Maintain?
OpenStack follows an open-source cost model: the software is free but organizations must invest significantly in infrastructure, expertise, and ongoing operational support to achieve production-ready deployments.
Initial deployment costs here are all about hardware procurement, professional services, and team training. Organizations often require substantial upfront investments in networking equipment, servers, and storage systems, because OpenStack requires robust infrastructure foundations. Many enterprises use consulting firms during initial deployment, with the cost of such services varying significantly based on organizational requirements and deployment complexity.
Ongoing operational expenses focus more on staffing and support than on software licensing. Dedicated infrastructure specialists that are familiar with OpenStack operations are needed here, often commanding much higher salaries than are typical for application-focused roles. Commercial support options from vendors (Red Hat, Canonical, SUSE) come with enterprise-grade assistance but also add another element to the list of ongoing costs.
Hidden cost factors of OpenStack include:
- Training and certification due to the need for extensive OpenStack knowledge for effective operations
- Hardware lifecycle management with regular refresh cycles for underlying infrastructure components
- Integration complexity, since most cases require custom development work for enterprise system connectivity
- Operational overhead in the form of monitoring, maintenance, and troubleshooting, all of which require dedicated resources
Opportunities for cost optimization emerge in different ways, including hardware flexibility and economies of scale. OpenStack’s vendor-neutral approach makes hardware procurement competitive, with the possibility of incremental additions to capacity without the architectural constraints that many proprietary solutions impose.
What is Included in the OpenShift Subscription?
OpenShift uses a subscription-based licensing model, which offers predictable costs and comprehensive vendor support. Its pricing models vary significantly, based on both the chosen deployment approach and management preferences.
Self-managed subscriptions use core-based pricing, with organizations paying for computing resources that are dedicated to OpenShift worker nodes. This model is a combination of platform software, updates, and support services, with different tiers to choose from based on operational needs and support level requirements.
Managed service options via cloud providers use a different economic model, with organizations paying for both the OpenShift service and the underlying cloud infrastructure. These services eliminate operational overhead but also create higher per-resource costs, compared to self-managed deployment options.
The biggest advantages of subscription models include comprehensive support, automated updates, integration testing and a range of operational tools. Budget predictability is arguably the greatest advantage any subscription model can offer, enabling much more accurate forecasting while avoiding unexpected infrastructure investment cycles that most hardware-based solutions often need.
There are several cost variables worth mentioning when it comes to OpenShift’s licensing model:
- Deployment model – The choice between self-managed and managed services affects both pricing structure and operational requirements
- Support tier selection – Standard business hours or premium 24/7 support, depending on the subscription type
- Contract terms – Multi-year commitments often create opportunities for substantial discounts
- Resource scaling – Compute resource consumption directly increases total subscription costs
What is the Total Cost of Ownership for Each Platform?
Total cost of ownership analysis reveals fundamentally different economic profiles, with OpenStack emphasizing upfront investment and operational expertise and OpenShift prioritizing predictable ongoing expenses with reduced operational complexity. Here are the most significant cost factors when calculating TCOs for both platforms:
| Cost Factor |
OpenStack TCO |
OpenShift TCO |
| Initial Investment |
Higher upfront costs – substantial hardware, deployment, and training expenses |
Lower initial investment – reduced hardware requirements and faster deployment |
| Ongoing Costs |
Variable expenses – primarily staffing and support, scaling with complexity |
Predictable subscription costs – enabling accurate multi-year budget forecasting |
| Scaling Economics |
Lower marginal costs – capacity additions involve hardware without software licensing |
Transparent scaling costs – resource expansion clearly defined through subscriptions |
| Staffing Requirements |
Operational expertise premium – requires higher-cost specialized infrastructure personnel |
Operational efficiency – platform automation reduces staffing requirements and overhead |
Accurate TCO assessment requires evaluating both direct platform costs and indirect impacts on organizational productivity, risk management, and strategic flexibility over multi-year planning horizons, which is difficult to calculate in a single theoretical article.
Break-even considerations favor OpenStack for most cases of large-scale, stable workloads, where initial investment is easy to amortize across extensive resource utilization. OpenShift economics are comparatively better for dynamic environments, where development velocity and operational simplicity generate business value that justifies its high subscription costs.
Security Considerations for OpenShift and OpenStack
Enterprise security requirements demand comprehensive protection across infrastructure, applications, and data throughout the entire platform lifecycle. Both OpenStack and OpenShift address security concerns via different architectural approaches: OpenStack provides infrastructure-level security controls; OpenShift focuses on application and container security frameworks.
How Do Security Features Compare Between Platforms?
OpenStack and OpenShift use completely different security models, reflecting their distinct purposes as infrastructure and application platforms and approaches to providing comprehensive security measures within their respective domains.
OpenStack’s security architecture centers around infrastructure protection, with multi-tenancy isolation, identity management through Keystone, and network segmentation capabilities. The platform offers role-based access control capabilities to enable granular permissions across projects, users, and resources. Its network security capabilities include security groups, floating IP management, and integration with enterprise firewalls or intrusion detection systems.
OpenShift’s security model focuses on container and application security using network policies, integrated vulnerability scanning capabilities, and Security Context Constraints. The platform assumes that underlying systems are managing the infrastructure system, choosing instead to focus on securing development workflows and containerized workloads.
For the sake of comparison, several major security features of both platforms have been gathered here in a single comparison table:
| Security Feature |
OpenStack |
OpenShift |
| Multi-tenancy and Isolation |
Project isolation with dedicated virtual networks and storage |
Security Context Constraints with fine-grained container privilege control |
| Identity Management |
Keystone with Active Directory, LDAP, and SAML integration |
OAuth integration with enterprise identity providers and SSO |
| Network Security |
Security groups and firewall rules at hypervisor level |
Network policies for microsegmentation and traffic control |
| Encryption |
Volume encryption, object storage encryption, encrypted service communications |
Pod security and runtime security enforcement with anomaly detection |
| Vulnerability Management |
Audit logging for compliance and forensic analysis |
Integrated container image scanning before deployment |
At the end of the day, OpenStack excels at infrastructure-level security controls, multi-tenancy isolation, and integration with traditional enterprise security tools. OpenShift, on the other hand, provides extensive application security features, along with container-specific protections and security integration with development workflows.
The choice between platforms in terms of security features hinges heavily on whether organizations prioritize infrastructure security protocol or application development security automation.
What Compliance and Governance Capabilities Does Each Platform Provide?
Compliance and regulatory requirements are significant drivers of security architecture decisions for enterprises, with OpenShift and OpenStack using different approaches to achieve industry standards and comply with government regulations.
Healthcare organizations often prefer OpenStack’s infrastructure control requirements for HIPAA (Health Insurance Portability and Accountability) compliance. Financial services, on the other hand, focus more on OpenShift for its application security automation and its support for PCI DSS (Payment Card Industry Data Security Standard) requirements. Government deployments also often require OpenStack’s air-gapped deployment capabilities for various security clearance environments.
Both platforms are compliant with certain frameworks, such as SOC 2 (System and Organization Controls), ISO 27001, and industry-specific regulations. However, their implementation approaches and ongoing maintenance requirements differ substantially, based on each platform’s compliance focus.
Regulatory Compliance in OpenStack
OpenStack compliance capabilities focus on infrastructure-level controls, supporting various regulatory frameworks via comprehensive audit trails, data sovereignty features, and integration with compliance management tools. OpenStack’s self-hosted deployment model allows organizations to maintain complete control over data location and processing, something that is paramount for regulations requiring data residency.
Regulatory support features of OpenStack are:
- Data sovereignty – full control over data location and cross-border transfer restrictions
- Audit trail generation – detailed logs of all user and administrative activities across platform services
- Encryption compliance – support for encryption modules validated for FIPS 140-2 (Federal Information Processing Standard), as well as appropriate key management systems
- Access control documentation – role-based permissions generate compliance reports for auditing
- Integration with SIEM systems – connectivity with Security Information and Event Management platforms for continuous monitoring
Regulatory Compliance using OpenShift
OpenShift’s compliance approach emphasizes application-level compliance via automated policy enforcement, security scanning, and development workflows controls. The platform includes compliance-as-code capabilities, embedding regulatory requirements into application deployment processes.
Regulatory support features of OpenShift are:
- Policy automation – enforcement of many security policies and configuration standards without human involvement
- Compliance reporting – built-in dashboards and reports for different regulatory frameworks
- Vulnerability management – continuous security scanning with policy-based remediation
- Secure development lifecycle – security controls are integrated into CI/CD pipelines
- Multi-cluster compliance – consistent policy enforcement in all distributed deployments
Backup and Data Protection Strategies
Enterprise data protection requires comprehensive backup and recovery strategies that align with business continuity requirements, regulatory compliance needs, and operational recovery objectives. OpenStack and OpenShift present different challenges and opportunities in the field of data protection, due to their distinct architectural approaches and data handling methods.
What Backup Options are Available for Each Platform?
OpenStack’s infrastructure-focused backup approach protects the underlying compute, storage, and networking layers that support VM workloads. Volume snapshots offer point-in-time captures of persistent storage, while complete VM image backups preserve entire virtual machine states with complete configurations and data.
Swift’s built-in multi-site replication offers distributed data protection capabilities for object storage, while automated database backup processes secure the service metadata of OpenStack deployments. The platform also uses its comprehensive API connectivity to integrate with a range of established enterprise backup solutions.
OpenShift takes a more application-centric strategy to backups, with a strong focus on container workloads and cluster state. Persistent volume backups leverage Container Storage Interface (CSI) snapshots for volume-level protection, while ETCD database backups preserve cluster configuration and state information.
Application-aware backup solutions understand container dependencies and data relationships, enabling consistent application recovery. The integration with GitOps allows configuration-as-code approaches, as well, with application definitions stored in version-controlled repositories that serve as recovery blueprints. The platform itself supports container-native backup tools like Velero and Kasten, alongside traditional enterprise solutions.
The fundamental difference between the two is the complexity of their backups and areas of focus. OpenStack must be coordinated across different infrastructure layers, which makes backups more complex but offers granular control over data protection. OpenShift’s backup complexity comes from application state consistency and container orchestration metadata, simplifying backup procedures but focusing only on application-level security.
Both platforms support integration with comprehensive enterprise backup solutions, as well. Bacula Enterprise is a good example of a backup solution that supports both: a mature, highly scalable backup solution with an open-source core that natively supports both OpenStack infrastructure components and OpenShift container workloads. Cross-platform backup tools like these enable organizations to maintain consistency in data protection with centralized backup management regardless of the platform type.
How Do Data Protection and Disaster Recovery Requirements Differ?
Data protection and disaster recovery (DR) planning reveal significant architectural differences in the ways OpenStack and OpenShift handle business continuity, with distinct approaches to achieving recovery objectives while maintaining service availability.
OpenStack disaster recovery focuses on infrastructure reconstruction and data restoration across multiple availability zones or geographic regions. OpenShift disaster recovery emphasizes application mobility and cluster federation capabilities, enabling workload migration between different environments. Their primary DR capabilities are summarized in a table below:
| DR Characteristic |
OpenStack |
OpenShift |
| Deployment Strategy |
Multi-site deployment with active-passive or active-active configurations across geographic locations |
Multi-cluster deployment with application workloads distributed across multiple OpenShift clusters |
| Recovery Approach |
Infrastructure recreation through automated rebuilding of compute, storage, and networking services |
Application migration using container images and configurations deployed to alternate clusters |
| Data Protection |
Cross-site replication of volumes, images, and object storage for geographic redundancy |
GitOps-based recovery with infrastructure-as-code approaches enabling rapid environment recreation |
| Recovery Complexity |
High complexity requiring coordination of multiple infrastructure components and service dependencies |
Reduced complexity with application-centric approach simplifying disaster recovery procedures |
| Recovery Objectives |
RTOs/RPOs (Recovery Time Objective/Recovery Point Objective) depend on infrastructure provisioning and data restoration speeds |
Faster recovery times through container deployment speeds enabling shorter RTO objectives |
Both platforms still must address regulatory requirements for data protection, but the implementation approaches they choose differ drastically:
- OpenStack’s infrastructure control enables organizations to implement specific data residency and encryption requirements that are commonly required in regulated industries;
- OpenShift’s application-focused approach brings built-in policy enforcement and automated compliance reporting, simplifying ongoing governance requirements while potentially limiting certain infrastructure-level control options.
Business continuity planning must evaluate whether organizational requirements should prioritize infrastructure resilience or application availability when designing disaster recovery strategies for either platform.
Conclusion
The choice between OpenStack and OpenShift ultimately depends on organizational priorities, technical requirements, and long-term strategic goals. OpenStack excels in businesses that must achieve infrastructure control via hardware flexibility, while OpenShift improves developer productivity with operational simplicity for container-focused strategies.
The final decision must align with existing technical expertise, budget considerations, and business objectives. Organizations with strong infrastructure teams and compliance requirements often find OpenStack’s flexibility valuable, while companies that prioritize rapid application development and deployment velocity tend to benefit more from OpenShift’s integrated platform approach.
Key Takeaways
- OpenStack is ideal for infrastructure-heavy organizations that require complete control over virtualization, storage, and networking, with the ability to customize and optimize at the hardware level
- OpenShift excels for development-focused teams that build cloud-native applications in need of integrated CI/CD pipelines, automated deployment workflows, and container orchestration capabilities
- Cost models differ fundamentally: OpenStack requires a higher upfront investment but with lower ongoing costs, while OpenShift uses predictable subscription pricing with lower operational complexity
- Security approaches reflect general platform focus: OpenStack provides infrastructure-level security controls and multi-tenancy isolation, while OpenShift emphasizes application security and container-specific security measures
- Deployment complexity varies significantly: OpenStack demands 3-6 months of planning and specialized expertise; OpenShift’s guided installation processes can achieve production readiness in 1-3 months
- Both platforms work together in layered architectures: OpenStack provides the infrastructure foundation while OpenShift delivers the container application platform on top
Frequently Asked Questions
Can I use OpenStack and OpenShift together?
Yes. OpenStack and OpenShift work great together in layered architectures, withOpenStack providing the infrastructure foundation and OpenShift working as the container platform on top. Such a combination allows organizations to leverage OpenStack’s infrastructure flexibility while also benefiting from OpenShift’s application development and deployment capabilities.
Which platform is easier for beginners to learn?
OpenShift is comparatively easier to learn than OpenStack, due to OpenShift’s guided installation processes, comprehensive web console, and integrated tooling that aims to reduce complexity. OpenStack has a steep learning curve that requires a deep understanding of virtualization, networking, and distributed systems before achieving productive deployments.
Do I need different technical skills for OpenStack vs. OpenShift?
Yes, the platforms need distinctly different skill sets:
- OpenStack requires infrastructure expertise in Linux administration, networking, storage systems, and virtualization technologies
- OpenShift needs container and Kubernetes knowledge, CI/CD pipeline management, and application deployment skills that are much more development-focused than infrastructure-oriented
Introduction
Enterprise data backup is a comprehensive combination of procedures, policies, and technologies designed to preserve and protect business-critical information in large and complex organizational infrastructures. An enterprise-grade backup solution is the backup software itself, as well as network connections with high bandwidth, immutable storage of various types, internal knowledge bases, employee training programs, and extensive vendor documentation. These solutions were originally made to handle the complex requirements of companies that manage thousands of endpoints, petabytes of data, and diverse IT environments covering on-premises, cloud, and hybrid infrastructures.
The value of a reliable backup solution for a modern business is difficult to overestimate in today’s digital landscape. Ransomware attacks already affect a large portion of businesses worldwide, with data breaches becoming more common and more complex at the same time, while regulatory compliance requirements grow more stringent in many industries. In this environment, enterprise backup software has had to evolve from a simple tool for data protection into a critical foundation for business continuity.
In this comprehensive guide, we will explore the essential aspects of enterprise backup software selection and implementation, offering decision-makers the knowledge they need to protect the most valuable information in their business. We’ll examine:
- The definition of enterprise backup software
- The leading backup software platforms for enterprises
- Critical backup strategies, such as the 3-2-2 rule
- Gartner’s latest evaluation of enterprise backup vendors
- Differences between on-premises and cloud deployment options
- Essential security features for protecting against modern threats
Understanding Enterprise Backup Solutions: Types, Features, and Business Impact
Enterprise backup solutions are categorized into several key areas that determine their effectiveness in large-scale businesses. To make informed decisions about backup software, it is essential to understand the different types of backup software, their features, and the advantages each provides to enterprise environments.
What Makes Enterprise Backups Different from Standard Methods and Approaches?
Enterprise backup software tools are indispensable components of modern-day business operations, as more and more companies increasingly rely on their IT infrastructures. These solutions’ role in safeguarding valuable information from theft, human error, corruption and loss is irreplaceable.
The significance of enterprise data backup goes beyond basic data protection to cover such valued topics as:
- Business Continuity Assurance. Enterprise backup solutions ensure organizations will be able to maintain operations during and after disruptive events, minimizing both revenue loss and downtime.
- Regulatory Compliance. Backup systems must always be adjusted to follow the organization’s regulatory mandates. Depending on the nature of the enterprise, compliance regulations encompass a variety of frameworks, from generic and all-encompassing (GDPR) to industry-specific (HIPAA, CMMC 2.0, ITAR, DORA).
- Cyber Resilience. Enterprise-grade data protection is often the last line of defense against ransomware attacks, especially in the modern landscape of digital threats. Secure backup files offer clean data copies for recovery when primary systems are somehow compromised.
- Scalability Requirements. Backup environments at enterprise scale are comprehensive systems designed to protect, manage, and recover the extremely large volumes of data that businesses generate. These solutions must go far beyond the capabilities of traditional backup methods, providing a variety of scalability and reliability options, along with a range of advanced features to meet the specific needs of large-scale business operations.
What are the Different Types of Enterprise Backup Solutions?
Enterprise backup solutions are categorized into several groups using their deployment architecture and delivery model, with each group addressing specific organizational needs and infrastructure demands. In the following sections we cover the following:
- Software-only solutions
- Integrated backup appliances
- Backup-as-a-Service options
- Hybrid backup software
- Cloud-native backup solutions
- Multi-cloud backup platforms
Software-Only Backup Solutions
Software-only backup solutions offer organizations backup software that is deployed on the existing hardware architecture, providing extensive flexibility and a wide range of customization opportunities. Notable examples of such software-only backup solutions include Bacula Enterprise, Commvault’s software licenses, and IBM Spectrum Protect.
The primary advantages of software-only backup solutions are:
- Deployment capabilities onto existing hardware infrastructure without additional appliance cost
- A high degree of customization and configuration to meet the organization’s specific needs
- Extensive flexibility in scaling decisions and hardware selection
Integrated Backup Appliances
Integrated backup appliances are turnkey solutions – backup software and optimized hardware combined in the same pre-configured system designed with the primary goal of simple deployment and management . Rubrik, Cohesity, and Dell Data Protection are all great examples of backup companies offering hardware backup appliances.
Integrated backup options are best known for:
- Pre-configured hardware and software integration for immediate deployment
- Vendor support for both hardware and software components
- Simplified deployment and management processes that emphasizes vendor optimization
Backup-as-a-Service Options
Backup-as-a-Service options are fully managed backup services delivered from the cloud, eliminating the need for any on-premises infrastructure management or maintenance. Most noteworthy examples of such platforms are HYCU and Druva, among others.
Key benefits of such environments include:
- Backup environments fully managed by a service provider with minimal requirements for consumption of internal resources
- No on-premises infrastructure requirements or maintenance responsibilities whatsoever
- Subscription-based pricing models with highly predictable operational expenses
Hybrid Backup Software
Hybrid backup solutions are a combination of on-premises and cloud components for comprehensive data protection that balances performance, cost, and security requirements. Popular examples of such solutions include Commvault, Bacula Enterprise, Barracuda Backup, and Veeam.
The biggest advantages of hybrid backup solutions are:
- Local backup enables rapid data recovery of the most frequently accessed information
- Cloud replication measures for disaster recovery and long-term data retention
- Flexible deployment options capable of adapting to changing business environments
Cloud-Native Backup Solutions
Cloud-native backup solutions are created specifically for cloud-native applications and cloud environments – offering deep integration with the infrastructure and APIs (Application Programming Interface) of their cloud service providers. Azure Backup, AWS Backup, and N2WS are just a few examples of such options.
These solutions offer the following benefits to their users:
- API-driven automation and extensive integration with cloud management tools
- An environment created specifically for cloud infrastructure, whether Google Cloud Platform, Azure, AWS, or other
- Regular use of pay-as-you-use pricing models that align well with cloud economics and result in substantial savings for certain businesses
Multi-Cloud Backup Platforms
Multi-cloud backup platforms provide unified backup management across several different cloud environments and providers, helping companies avoid vendor lock-in while retaining centralized control. Notable examples of such environments include Rubrik, Cohesity, Bacula Enterprise, and Commvault.
Most noteworthy capabilities of such environments are:
- Vendor-agnostic cloud support across a range of providers
- Centralized management and monitoring for diverse cloud environments
- Data portability between providers, avoiding the disastrous consequences of vendor lock-in
Benefits of Using Enterprise Backup Software for Data Protection
Now that we have covered the different options on the backup software market, it is time to cover the most valuable advantages of an enterprise backup solution. The six main advantages are covered below:
- Cost reduction
- Administration simplification
- Training and support minimization
- Regulatory compliance
- Security and ransomware protection
- Disaster recovery and business continuity
Reduction of Backup and Recovery Costs
When data is stored in the cloud, recovery costs will always be substantial. Cloud storage providers tend to charge less for uploading data, but much more when data is downloaded for recovery reasons. Good backup software minimizes both download volume and storage costs for both disk and tape storage types.
Backup Administration Simplification
The management of enterprise IT infrastructures with tens of thousands of endpoints (computers, servers, Virtual Machines and others) is inherently very complex. Backup processes will be difficult for an administrator who must think about where to backup the specific endpoint, whether there is enough storage or network bandwidth available, what are the retention policies for this data and whether the older copies must be migrated to free up space. Dedicated efficiency tools, like automated copy or migration of backed up data, automated restart of backup jobs after cancellation, job scheduling and sequencing with priorities, reduce the complexity of this process to a certain degree.
Staff Training and Ongoing Support Minimization
Enterprise companies typically have a large IT staff. Teaching new employees how to use the backup system is difficult and time-consuming when done manually by existing professionals. Leveraging intuitive UI and automation features significantly reduces the need for extensive staff training and ongoing support, making enterprise backup management somewhat more efficient and cost-effective.
Regulatory Compliance Improvement
Backup systems must always adjust to the organization’s regulatory mandate. Depending on the nature of the enterprise, compliance regulations are either generic like GDPR, NIST, FIPS, or industry-specific – like HIPAA, DORA, ITAR or CMMC 2.0. Local regulations apply here as well, such as Australia’s Essential Eight, UK’s Government Security Classifications, and more. Enterprise companies have no choice but to carefully navigate and engage with the complex landscape of compliance regulations all over the world.
Security and Ransomware Protection
Enterprise backup solutions offer critical protection against ransomware attacks and cyber threats, using features like air-gapped storage, backup immutability, and comprehensive encryption algorithms. Creating write-once-read-many (WORM) storage is also an option: a storage segment that cannot be modified once written to ensure a clean recovery point, even after a successful cyberattack of sorts.
Disaster Recovery and Business Continuity
Large-scale backup environments using automated failover capabilities, bare metal recovery, and support for high availability infrastructures provide minimal downtime and business continuity. These solutions assist organizations to maintain operations during hardware failures, natural disasters, and major system outages, all while meeting the enterprise’s recovery time objectives (RTO) and recovery point objectives (RPO).
Open-Source vs Commercial Enterprise Backup Solutions
Overview of Open-Source vs Commercial Backup Solutions
Open-source backup solutions offer organizations cost-effective data protection using freely available software and community-driven development; a stark contrast to commercial enterprise backup solutions that provide comprehensive feature sets, professional support, and vendor accountability via paid licensing models.
Open-source solutions may require internal IT expertise for successful implementation, as well as for customization and ongoing maintenance. This makes them much more suitable for organizations with in-house technical capabilities, but small budgets. Commercial solutions, on the other hand, are turnkey platforms with the regular updates, vendor support, compliance certifications, and service level agreements that enterprise environments need for protection of mission-critical data.
Primary Benefits of Open-Source and Commercial Backup Software
Before committing to any option, enterprise organizations must carefully evaluate whether open-source solutions satisfy their specific requirements for scalability, security, compliance, and operational support.
Commercial backup software often provides a wide range of advanced features that may not be available or readily accessible in open-source alternatives, such as enterprise-grade encryption, automated compliance reporting, or integration with enterprise management systems. That being said, open-source backup solutions tend to provide greater flexibility in customization while avoiding vendor lock-in concerns, and are often much more cost-effective for businesses that are willing to invest in internal expertise and development resources. One additional benefit of open source-based solutions such as Bacula is that the code has been downloaded and tested by many thousands of developers worldwide. As a result, open source solutions such as this tend to have very high levels of dependability, security and stability.
Bacula Community and Bacula Enterprise
It is possible to provide examples for both of these solution-types using Bacula Systems and their software offerings.
Bacula Community is a leading open-source backup solution with extensive backup and recovery functionality that relies primarily on community support and documentation. Bacula Enterprise is built on this open-source foundation, adding commercial-grade features like professional support, advanced security, and enterprise scalability, all of which makes it suitable for even large-scale enterprise environments.
This dual approach provides the best of both worlds, and also allows organizations to evaluate the platform’s open-source capabilities using Bacula Community at no additional cost before transitioning to the commercial Bacula Enterprise solution once the organization’s enterprise requirements exceed the limitations of the open-source option.
Top Industry Leading Backup Software
The enterprise backup software market offers a wide range of solutions, each with distinct strengths and capabilities designed to meet specific organizational requirements. To assist in navigating this complex and nuanced landscape, we have comprehensively analyzed 14 of the leading backup platforms, including their features, performance, customer satisfaction, and enterprise-readiness to find the option most suitable for any business scenario.
The Review of Top 14 Enterprise Backup Solutions

Rubrik is one of the best backup and recovery vendors on the market, specializing in hybrid IT environments. Rubrik Cloud Data Management (RCDM) is their own creation, which makes data protection and cloud integration so much easier. Of course, they also have their own data management platform: Polaris. Polaris consists of Polaris GPS for policy management and reporting and Polaris Radar for ransomware detection and rehabilitation.
Customer ratings:
- Capterra – 4.8/5 stars based on 74 customer reviews
- TrustRadius – 7.8/10 stars based on 234 customer reviews
- G2 – 4.6/5 stars based on 94 customer reviews
Advantages:
- Clean and organized administrative interface
- Multi-cloud and hybrid offerings and integrations with multiple cloud storage providers
- Vast automation capabilities
Shortcomings:
- Cannot backup Azure SQL directly to the cloud, requiring extra steps to do so
- First-time setup is long and difficult
- Documentation is scant; could use helpful articles and whitepapers
Pricing:
- Rubrik’s pricing information is not publicly available on its official website; the only way to obtain pricing information is by contacting the company directly for a personalized demo or a guided demonstration.
Customer reviews (original spelling):
- Jon H. – Capterra – “Rubrik has allowed us to stop focusing on the minutiae of running a homegrown backup storage/orchestration product and focus on automation of the infrastructure/deployment instead. Rubrik has improved the performance of our backup jobs, allowing us to perform more backups with fewer resources overall Rubrik has given our clients more choice in how backups function”
- Verified Reviewer – Capterra – “It’s improved operational efficiency, as we now don’t have to spend time scheduling backups, and has created very tangible savings. In the next 5 years we expect to save over 55% switching from our legacy provider to Rubrik. It also mitigated us against any future data centre blackouts through its Azure replication capabilities – while significantly reducing our power consumption and footprint in the data centre.”
The author’s personal opinion about Rubrik:
Rubrik is a reasonably versatile enterprise backup solution that includes many features one expects from a modern backup solution of this scale. It offers extensive backup and recovery options, a versatile data management platform, a host of data protection measures for different circumstances, extensive policy-based management, and so on. Rubrik’s main specialization is in working with hybrid IT environments, but it also works with practically any company – if the customer in question is fine with the price Rubrik charges for its services.

When it comes to Hyper-V and VMware backup solutions, Unitrends is always an option. First, it’s free for the first 1 TB of data, and there are multiple editions (free, essentials, standard, enterprise, and enterprise plus) for customers with different data limits. Other features of Unitrends’ backup solution include instant Virtual Machine (VM) recovery, data compression capabilities, ransomware detection service, protection for virtual and physical files, and, of course, community support.
Customer ratings:
- Capterra – 4.7/5 stars based on 35 customer reviews
- TrustRadius – 8.0/10 stars based on 635 customer reviews
- G2 – 4.2/5 stars based on 431 customer reviews
Advantages:
- The backup process is easy to initiate once it is set up properly
- Granular control over the entire backup process
- Convenient dashboard with centralized access to a wealth of information
Shortcomings:
- Single file recovery is not easy to initiate from the web interface
- Infrequent false alerts
- No instruction sets in the interface itself, only in web forums
Pricing:
- Unitrends’s pricing information is not publicly available on its official website, meaning the only way to obtain such information is by contacting the company directly for a quote, a free trial, or a guided demonstration.
- Unofficial information states that Unitrends has a paid version that starts at $349 USD
Customer reviews (original spelling):
- Yuri M. – Capterra – “it gives us less time to restore in case of an emergency and also the learning curve is quick. The reports are also very informative so we can know exactly what is happening with the backups and make sure we can restore in case we need it.”
- Richard S. – Capterra – “Support has been really good. But they suggested and did a firmware and software upgrade. I had to remove the client from all my servers and reinstall it. Then the backups didn’t run for several days. Have to work with support to get everything working again correctly.”
The author’s personal opinion about Unitrends:
Unitrends’s marketing emphasizes “solving the issue of complex backup solutions.” The software itself is fairly competent. Unitrends’s most popular offering is a backup and recovery platform that covers virtual environments, physical storage, apps, cloud storage, and even endpoints. A centralized approach to managing a multitude of data sources at once greatly boosts the solution’s overall convenience, and most of its processes are highly customizable. It has its own issues, including a confusing pricing model and a problematic granular restoration process, but none of these issues reduce the overall effectiveness of the software as a whole.

If we’re talking about some specific virtual environments such as vSphere, then Veeam could be our first pick, with its technologies that allow flexible and fast data recovery when you need it. Veeam’s all-in-one solution is capable of protecting VMware vSphere/Hyper-V virtual environments and doing basic backup and recovery jobs, as well. The scalability of the solution is quite impressive too, as well as the number of its specific features, like deduplication, instant file-level recovery, and so on. Veeam’s distribution model is not exactly complex, either: there are several versions with different capabilities and variable pricing.
Customer ratings:
- Capterra – 4.8/5 stars based on 75 customer reviews
- TrustRadius – 8.9/10 stars based on 1,605 customer reviews
- G2 – 4.6/5 stars based on 634 customer reviews
Advantages:
- Initial setup is simple and easy
- Most of Veeam’s solutions are available for free for smaller companies, with some limitations
- Good customer support
Shortcomings:
- UI could be more user-friendly
- The pricing of the solution is higher than average
- Mastering all of Veeam’s capabilities requires significant time and resources
- Security levels are questionable
Pricing:
- Veeam’s pricing information is not publicly available on its official website, meaning the only way to obtain pricing information is by contacting the company directly for a quote or a free trial. What it does have is a pricing calculator page that lets users specify the number of different environments they want covered with Veeam’s solution, as well as the planned subscription period. All of that is sent to Veeam to receive a personalized quote.
Customer reviews (original spelling):
- Rahul J. – Capterra – “I have been using Veeam since from February 2021. It’s actually good software but faced many backup issues when Server size was more than 1TB. Otherwise restoration processes are good, Instance recovery processes are also simple and useful for migration also. It’s seriously very good software for full server type backup(Host base backup).”
- Joshua H. – Capterra – “I use this to manage backups of office-facing and production servers in a non-profit business. We have less than 10 servers to care for and the free Community Edition is perfect. I have found the features and reporting to be robust. Practicing restores is no trouble. I have never needed vendor support to operate or configure this Veeam Backup & Replication – it works well and has good documentation!”
The author’s personal opinion about Veeam:
Veeam is the most well-known backup solution on this list, or at least one of the most popular. It does focus on its VM-related backup capabilities, but the solution itself is also suitable, to some extent, for working with other environments: physical, cloud, applications, and more. It is a fast and scalable solution that has plenty to offer to practically every possible client type, from small startups and small businesses to massive enterprises. At the same time, it can be quite difficult to learn all of its capabilities, security levels are questionable, and the pricing of the solution is well above the market average.

Bacula Enterprise is a highly reliable backup and recovery software that presents an assortment of functions, like data backup, recovery, data protection, disaster recovery capabilities and more. It offers especially high security and is primarily targeted at medium enterprises and larger companies. Bacula provides an unusually large range of different features, from various storage types and easy setup to low deployment costs and extra-fast data recovery times. It works with practically any (actually, more than 34) Linux distributions (Debian, Ubuntu, etc.), and many other operating systems, too, like Microsoft, MacOS X, Solaris, and more. Bacula’s unique modular architecture provides even greater protection against ransomware and other attacks. It offers a choice (or combination) of both command line and Web-based GUI’s. Its broad range of security features and many additional high performance, enterprise-grade technologies, such as advanced deduplication, compression, and additional backup levels make it a favorite among HPC and mission-critical, demanding enterprises. The licensing model also avoids charging per data volume, which makes it especially attractive to MSPs, ISVs, Telcos, Military and Research establishments, large data centers and governmental organizations.
Customer ratings:
- TrustRadius – 9.7/10 stars based on 63 customer reviews
- G2 – 4.7/5 stars based on 56 customer reviews
Advantages:
- Especially high security levels and deployment flexibility
- Job scheduling is incredibly useful for many reasons
- Creates an effective backup and disaster recovery framework
- Support for many different data environments, such as servers, database-types, VM-types, Cloud interfaces, in-cloud apps, etc.
- Users pay for only the technology they use, creating even more savings
- Works with practically any kind of storage and storage device
- Easily scales up to petabyte-sized environments
- High flexibility for complicated or demanding workloads
Shortcomings:
- Web interface’s broad functionality requires time to master
- The initial setup process takes time, usually because of its implementation into diverse environments.
- Additional price for plugins that are not included in the basic solution package
Pricing:
- Bacula Enterprise’s pricing information is not publicly available on its official website, meaning that the only way to obtain such information is by contacting the company directly for a quote.
- Bacula Enterprise offers a variety of different subscription plans, although there is no pricing available for any of them:
- BSBE – Bacula Small Business Edition covers no more than 20 agents and 2 contracts, offering features such as web support and BWeb management suite
- Standard covers up to 50 agents and 2 contracts, adds support answer deadlines (from 1 to 4 business days)
- Bronze covers up to 200 agents and 2 contracts, offers phone support and shorter deadlines for customer support (from 6 hours to 4 days)
- Silver covers up to 500 agents and 3 contracts, introduces a deduplication plugin and a lower customer support answer deadline (from 4 hours to 2 days)
- Gold covers up to 2000 agents and 5 contracts, drastically reduces customer support answer deadline (from 1 hour to 2 days)
- Platinum covers up to 5000 agents and 5 contracts, has PostgreSQL catalog support and one training seat per year for Administrator courses
- Unofficial sources claim that Bacula Enterprise’s pricing starts at $500 per month
Customer reviews (original spelling):
- Jefferson Lessa – TrustRadius – “During these two years, we have been using Bacula Enterprise as a backup and disaster recovery solution for our entire data environment. This tool solved the problems we had in monitoring backups and in the agility to recover information. We are currently using this solution for more than 2Tb of data in a primarily virtualized environment. Bacula Enterprise’s technical support has perfectly met all the needs we’ve had in recent years. The installation of the tool was easy and the entire team adapted well to the daily use of this solution.”
- Eloi Cunha – TrustRadius – “Currently, the Brazilian Naval Supply System Command uses Bacula Enterprise to backup and restore the database. As a result, we have advanced features and the ability to handle the high volume of data we need for daily life, performing snapshots, advanced deduplication, single-file restores efficiently and reliably. I can detail as pros & cons the following personal use cases. Reliability and great cost-benefit.
- Davilson Aguiar – TrustRadius – “Here at Prodap, we have been struggling for a long time to access backup software that is good and affordable, we found Bacula as the best value for money. Right from the start, it solved our compression problem because the others we used weren’t very efficient about it. It made us take up less storage.”
The author’s personal opinion about Bacula Enterprise:
I may be a bit biased, but I believe that Bacula Enterprise is one of the best possible options on the backup and recovery market for both large companies and enterprises. It is a versatile backup solution with many features and capabilities. Bacula has a system of modules that extend the functionality in some way, such as native integration into VMware, Proxmox, Hyper-V and Kubernetes. Bacula offers a modular architecture, a broad variety of supported operating systems, and impressively flexible support for specific storage types or data formats. Above all, Bacula’s superior levels of security and its ability to mold those security layers into an organization’s (often very) specific needs cannot be overstated in today’s world of aggressive ransomware and other security attacks. It takes a little time to learn initially, and users should have at least some Linux knowledge, but the wealth of features available to even an average Bacula user is more than worth the effort it takes to learn it.

Acronis is a well-known competitor in the software market, and its Cyber Backup solution upholds the company’s standards, offering a secure and effective backup solution for multiple use cases. Acronis protects your information from a wide variety of threats, including software failures, hardware problems, cyber-attacks, accidents, and so on. There are also more features in the same field, such as in-depth monitoring and reporting, minimized user downtime, the ability to ensure if a backup is authentic or not, and so on.
Customer ratings:
- Capterra – 4.1/5 stars based on 75 customer reviews
- TrustRadius – 5.9/10 stars based on 139 customer reviews
- G2 – 4.3/5 stars based on 700 customer reviews
Advantages:
- Compatible with a large variety of workloads
- AI-based malware protection
- Easy data collection operations
Shortcomings:
- The solution’s pricing is significantly above the market average
- The backup agent is incredibly demanding on system hardware
- The user interface is confusing and is outdated relative to its competitors
Pricing:
- Acronis Cyber Protect’s backup capabilities vary in pricing, depending on the nature of the backup target:
- From $109 for one workstation, be it physical or virtual, macOS or Windows
- From $779 for one server, be it physical or virtual, Linux or Windows
- From $439 for a 3-pack of public cloud virtual machines
- From $1,019 for one virtual host, be it Hyper-V or VMware (no limitations on the number of virtual machines per host)
- From $209 for 5 seats in Microsoft 365 with full coverage (across SharePoint Online, Teams, OneDrive for Business or Exchange Online)
- Acronis Cyber Protect – Backup Advanced offers file-level backups, image-based backups, incremental/differential backups, ransomware protection, vulnerability assessment, group management, AD integration, reports, and more.
Customer reviews (original spelling):
- Gábor S. – Capterra – “Easy to operate because cloud backup can be performed with the same configuration as on-premises. Pricing is more economical than other services. An introductory one for those who do not use cloud services. We only restored the server as a test, but we converted the image to a model different from the physical server. Servers can be restored even in case of fire or disaster damage.”
- Chase R. – Capterra – “A solid backup solution when it works. Once it works it tends to stay working. The only issue is if it’s not working, you will have to figure it out on your own, next to no support!”
The author’s personal opinion about Acronis:
As a company, Acronis offers backup and recovery software for different use cases, primarily large-scale enterprises. Data security is always its sharpest focus and it claims to be able to protect its users against cyber-attacks, hardware failures, software issues, and even the ever-present “human factor” in the form of accidental data deletion. It includes AI-based malware protection, extensive backup encryption, and backup-related features that are really good. However, scalability is limited, integration with some databases, VMs and containers is limited, its interface is a touch confusing at times, and the solution itself is often described as “very expensive.” Still, many small and medium companies would gladly pay Acronis to safeguard their data.

Cohesity is more of an “all-in-one” solution, capable of working with both regular applications and VMs. Its scalability is quite impressive, as well, thanks to its cluster-like structure with nodes. Cohesity stores backups in app-native formats and uses NAS protocols to manipulate a variety of data types. Its data restoration speed is good, as well. Unfortunately, the pricing model isn’t particularly flexible and some specific objectives, like MS Exchange or SharePoint granular recovery, are covered only by separate modules that are separately priced.
Customer ratings:
- Capterra – 4.6/5 stars based on 51 customer reviews
- TrustRadius – 8.5/10 stars based on 86 customer reviews
- G2 – 4.4/5 stars based on 47 customer reviews
Advantages:
- User-friendly interface
- Simple and fast implementation
- Convenience of seeing all clusters in a single screen
Shortcomings:
- Cannot perform backups on a specific date of the calendar
- Database backup process is inconvenient and needlessly convoluted
- Automation capabilities are very basic
Pricing:
- Cohesity’s pricing information is not publicly available on its official website, meaning the only way to obtain it information is by contacting the company directly for a free trial or a guided demo.
Customer reviews (original spelling):
- Justin H. – Capterra – “Backing up entire VM’s through vCenter is a breeze and works well. Application backups (Exchange, SQL, AD) will all require an agent and the agent management is very poor in my opinion. Replication works fine and restore times from locally cached data is quick. There are still a lot of little things that keep this from being a polished solution but the overall product is good.”
- Michael H. – Capterra – “Cohesity has been excellent to work with. The local team is always helpful and responsive, support is excellent, and the product exceeds all expectations. We started small because we were uncertain that they could do all of the things we heard about during the pre-sale process, but we couldn’t be happier with the product. We are currently in the process of tripling our capacity and adding additional features because we were so impressed by every aspect of Cohesity.”
The author’s personal opinion about Cohesity:
Cohesity’s feature set is a good example of a middle-ground enterprise-grade data protection solution. Its feature set has everything you would expect from a backup solution at this level: support for a variety of data types and storage environments, impressive backup/restoration speed, an impressive list of backup-centric features, and more. What’s interesting about Cohesity specifically is its infrastructure: the entire solution is built using a node-like structure that allows for impressive scalability that is both fast and relatively simple to use. Cohesity’s interface is rather user-friendly in comparison with other software on the market, but database backup with Cohesity is not particularly simple or easy, and there are few, if any, automation capabilities available. Container backup needs much more work, and reporting is also limited.

IBM’s prime goal is to make data protection as simple as it gets, no matter the storage type or data type. IBM Storage Protect (formerly known as Spectrum Protect or Tivoli Storage Manager) is one such solution, offering impressive data protection capabilities at scale with impressive security capabilities, like encryption. There are many different features, like basic backup and recovery jobs, disaster recovery, bare metal recovery, and so on. The solution itself is based on an agentless virtual environment and works well with both VMware and Hyper-V environments. The licensing model is charged per TB spent, no matter the data type, which makes it cheaper in some specific cases with large amounts of data processing.
Customer ratings:
- TrustRadius – 7.8/10 stars based on 41 customer reviews
- G2 – 4.1/5 stars based on 77 customer reviews
Advantages:
- The convenience of a single backup solution for a complex environment with multiple storage types
- A wealth of backup-related options, such as granular recovery and integration with third-party tools
- Its documentation and logging capabilities are highly regarded
Shortcomings:
- Setting up and configuring the solution properly requires time and resources
- Solution’s GUI is confusing and takes time to master
- The complexity of the architecture is significantly higher than average
Pricing:
- The only pricing information that IBM offers to the public is the cost of its IBM Storage Protect for Cloud option, which is calculated using a dedicated web page.
- IBM Storage Protect for Cloud is compatible with five primary categories of software, including:
- Microsoft 365 – starting from $1.52 per user per month.
- Microsoft Entra ID – starting from $1.01 per user per month.
- Salesforce – starting from $1.52 per user per month.
- Dynamics 365 – starting from $1.34 per user per month.
- Google Workspace – starting from $1.27 per user per month.
- We should note here that IBM offers volume discounts for companies purchasing 500 or more seats at once.
- At the same time, there is a dedicated toggle that adds “unlimited storage in IBM’s Azure Cloud,” which raises most of the above mentioned prices accordingly:
- Microsoft 365 – starting from $4.22 per user per month.
- Salesforce – starting from $4.22 per user per month.
- Dynamics 365 – starting from $3.37 per user per month.
- Google Workspace – starting from $3.18 per user per month.
Customer reviews (original spelling):
- Naveen Sharma – TrustRadius – “Tivoli (TSM) software is best for the policy-based management of file-level backups with automatic data migration between storage tiers. It’s the best way to save on the cost of storage and other resources. I really like the deduplication functionality of source and destination data, which helps to save the network bandwidth and storage resources. The administration of Tivoli is still complex, which means you need good skills to manage this product. Although a new version is coming with a better GUI, it will still require good command-line skills to make Tivoli do everything.”
- Gerardo Fernandez Ruiz – TrustRadius – “If you also need to have an air-gapped solution, Spectrum Protect has the option of sending the backup to tape (and it can also replicate the information to another site if needed).”
The author’s personal opinion about IBM Spectrum:
IBM Spectrum is a lesser-known backup solution from a well-known technology company. This is the same company that is known more for its hardware than for its software. However, IBM Spectrum is still a good backup and recovery solution for large companies. It is simple, feature-rich, agentless, and supports a wide variety of different storage types. It also excels at what is often perceived as the weakest part of enterprise backup solutions: reporting and logging capabilities. The solution in question is a bit difficult to configure initially, and the overall interface of the solution is regularly described as rather confusing, with the individual elements of the solution creating the most substantial issues. But, taken as a whole, the solution is rather impressive.

Dell Data Protection Suite is a comprehensive data protection solution that should work for most companies of any size. Data protection levels are variable, user-friendly UI allows for easy data protection visualisation, and built-in continuous data protection technology (CDP) allows for fast recovery times in VM environments. There are also several different applications in the package, as well, such as the separate backup in the cloud, the support for more storage types, data isolation/data recovery/data analytics automatization, and so on.
Customer ratings:
- TrustRadius – 8.0/10 stars based on 6 customer reviews
- G2 – 4.1/5 stars based on 20 customer reviews
Advantages:
- Support for plenty of different OS types
- Great for large databases and enterprises
- Interface user-friendliness
Shortcomings:
- Backups could fail if some elements in the system are different from before
- Error reports are somewhat confusing
- A lot of complains about the customer support
Pricing:
- Dell Data Protection Suite’s pricing information is not publicly available on their official website and the only way to obtain such information is by contacting the company directly for a quote or a demo.
- The unofficial information suggests that Dell’s pricing starts at $99 per year per single workspace
Customer reviews (original spelling):
- Cem Y. – G2 – “I like Dell Data Protection very much because it helps me to protect my personal computers as well as my work computers against malicious attacks. It has a very user-friendly interface. You can protect your passwords, personal information perfectly. There are some properties of Dell Data Protection. I don’t understand some reports that it produces. It is hard to figure out what the problem is and which solution I need to apply. Its price could also be much more affordable. There may be some different price policies.”
- Chris T. – G2 – “The compliance reporting dashboard is terrific as it provides a quick overview of endpoint compliance. This tool is very taxing on older systems particularly when it does its initial encryption pass of the entire drive.”
The author’s personal opinion about Dell Data Protection Suite:
This is another good example of enterprise backup software from Dell, a company better known for its hardware appliances than its software. Dell Data Protection Suite is not the first backup solution from this company, but it is a decent enterprise backup tool. It offers a user-friendly interface, plenty of centralization capabilities, a variety of features and functions in the realm of backup operations, and more. It supports many different operating systems and storage types, making it a great fit for large-scale businesses and enterprises. At the same time, the solution has its share of problems, from inconsistent customer support reviews to confusing backup error messages and limits on certain technologies and reporting capabilities.

If you’re looking for a company that has a long history, Veritas is the one for you, with its several decades of company success. Its backup and recovery capabilities are quite extensive, with information governance, cloud data management, and other brand-new functions. You choose from either the deployable version of their solution or the integratable appliance. Veritas is highly favored by older legacy companies that prefer services that have proven themselves over time. However, users report that there are some problems with hardware scaling capacity, as well as other little ’niggles’ here and there.
Customer ratings:
- Capterra – 4.2/5 stars based on 12 customer reviews
- TrustRadius – 6.9/10 stars based on 163 customer reviews
- G2 – 4.2/5 stars based on 272 customer reviews
Advantages:
- The sheer number of features available to customers
- Praise-worthy GUI
- Excellent customer support
Shortcomings:
- Working with LTO tape libraries is problematic
- Cannot export reports to a PDF file without Adobe Reader installed on that same system
- Automated reports cannot be saved to a different location on a different server
Pricing:
- Veritas’s pricing information is not publicly available on their official website and the only way to obtain pricing information is by contacting the company directly.
Customer reviews (original spelling):
- Mark McCardell – TrustRadius – “Veritas Backup Exec is best suited for <1PB environments that deal with typical Windows & Linux file storage arrays. Once you delve into more sophisticated storage environments, there are no available agents for those environments.”
- Taryn F. – Capterra – “Veritas Backup Exec is a good choice for small to medium businesses with a relatively simple set up , not requiring many different agents to be backed up, and without excess amounts of data. The licensing model is complicated and can be expensive, but I have seen great changes in the options supplied now – such as the Per VM model”
The author’s personal opinion about Veritas:
Veritas is considered an average enterprise backup solution, to a certain degree: it offers most of the features that one would expect in a similar solution, be it support for plenty of different environments or a variety of features for data security, data backups, etc. Veritas’ discerning feature is, to a certain degree, its legacy. As a provider of backup software, Veritas has been around a long time, even by this market’s standards, and during that time, it has managed to accumulate many positive reviews over the years. This experience and reputation are what many older and more conservative businesses are looking for, which is why Veritas still has many clients and acquires new ones on a regular basis. Veritas also has several very specific shortcomings, such as the lack of proper LTO tape support as backup storage, which is a massive detriment for specific users.

Nakivo Backup & Replication is another competitor on the list that was developed by a much larger company in general. Its backup solution is reliable, fast and works with both cloud and physical environments, offering enterprise-grade data protection and an entire package of other features, including: file recovery on-demand, incremental backup for different platforms, low backup size, impressive overall performance, and all packaged in a nice, easy-to-use, UI.
Customer ratings:
- Capterra – 4.8/5 stars based on 427 customer reviews
- TrustRadius – 9.3/10 stars based on 182 customer reviews
- G2 – 4.7/5 stars based on 278 customer reviews
Advantages:
- Easy to install and configure
- Simple and clean user interface
- Noteworthy customer support
Shortcomings:
- Error logging is limited and cannot always help to determine the cause of the error
- Limited support for physical servers running on Linux
- Higher than average price tag
Pricing:
- NAKIVO’s pricing is split into two main groups:
- Subscription-based licenses:
- “Pro Essentials” – from $1.95 per month per workload, covers most common backup types such as physical, virtual, cloud and NAS, while also offering instant granular recovery, virtual and cloud replication, storage immutability, and more
- “Enterprise Essentials” – from $2.60 per month per workload, adds native backup-to-tape, deduplication appliance integration, backup to cloud, as well as 2FA, AD integration, calendar, data protection based on policies, etc.
- “Enterprise Plus” does not have public pricing available, but adds HTTP API integration, RBAC, Oracle backup, backup from snapshots, and other features
- There is also a subscription available for Microsoft 365 coverage that costs $0.80 per month per user with annual billing and the ability to create backups of MS Teams, SharePoint Online, Exchange Online, OneDrive for Business, and more
- Another subscription from NAKIVO is its VMware monitoring capability, which comes in three different forms:
- “Pro Essentials” for $0.90 per month per workload with CPU, RAM, disk usage monitoring and a built-in live chat
- “Enterprise Essentials” for $1.15 per month per workload, which adds AD integration, 2FA capability, multi-tenant deployment, and more
- “Enterprise Plus” has no public pricing and adds RBAC and HTTP API integrations
- We should also mention the existence of a Real-time Replication pricing tier that offers the feature with the same name for VMware vSphere environments for $2.35 per month per workload, with 2FA support and Microsoft AD integration.
- All prices mentioned above are presented with a three-year plan in mind; shorter contracts would have different pricing points.
- Perpetual licenses:
- Virtual environments:
- “Pro Essentials” for $229 per socket, covers Hyper-V, VMware, Nutanix AHV, and features such as instant granular recovery, immutable storage, cross-platform recovery, etc.
- “Enterprise Essentials” for $329 per socket, adds native backup to tape, backup to cloud, deduplication, 2FA, AD integration, and more
- “Enterprise Plus” with no public pricing that adds RBAC and HTTP API integrations, as well as backup from storage snapshots
- Servers:
- “Pro Essentials” for $58 per server, covers Windows and Linux, and features such as immutable storage, instant P2V (Physical-to-Virtual), instant granular recovery, etc.
- “Enterprise Essentials” for $76 per server, adds native backup to tape, backup to cloud, deduplication, 2FA, AD integration, and more
- “Enterprise Plus” with no public pricing that adds RBAC and HTTP API integrations
- Workstations:
- “Pro Essentials” for $19 per workstation, covers Windows and Linux, and features such as immutable storage, instant P2V, instant granular recovery, etc.
- “Enterprise Essentials” for $25 per workstation, adds native backup to tape, backup to cloud, deduplication, 2FA, AD integration, and more
- “Enterprise Plus” with no public pricing that adds RBAC and HTTP API integrations
- NAS:
- “Pro Essentials” for $149 per one Terabyte of data, with backup NFS shares, SMB shares, folders on shares, and offer file level recovery
- “Enterprise Essentials” for $199 per one Terabyte of data, adds AD integration, 2FA support, calendar, multi-tenant deployment, etc.
- “Enterprise Plus” with no public pricing that adds RBAC and HTTP API integrations
- Oracle DB:
- “Enterprise Plus” is the only option available for Oracle database backups via RMAN, it offers advanced scheduling, centralized management, and more for $165 per database.
- VMware monitoring:
- “Pro Essentials” for $100 per socket with CPU, RAM, disk usage monitoring and a built-in live chat
- “Enterprise Essentials” for $150 per socket that adds AD integration, 2FA capability, multi-tenant deployment, and more
- “Enterprise Plus” with no public pricing that adds RBAC and HTTP API integrations
- Real-time Replication:
- Enterprise Essentials for $550 per socket with a basic feature set.
- Enterprise Plus with no public price tag that offers RBAC support, HTTP API integration, etc.
Customer reviews (original spelling):
- Ed H. – Capterra – “We got tired of the massive cost of renewals from our past backup software providers and decided to try Nakivo instead. They supported our need for Nutanix AHV, QNAP and Tape backups. I’m looking forward to trying the new PostgreSQL database option soon so that I can build my own reports. Nakivo gets the job done and gets better with each version.”
- Joerg S. – Capterra – “We are using Nakivo B&R for our new server with quite a number of virtual machines (VM Ware). Backup of data is onto a Synology via 10GB/s. The backup makes use of all available network speed. Once you understand how it works, its configuration is straightforward. Whenever we experienced some issues, Nakivo Service was very helpful (GoTo meeting) and pretty fast (next day at the latest). So far no complaints on their response.”
The author’s personal opinion about NAKIVO:
NAKIVO does not have decades of experience behind it, and it is definitely not the most feature-rich solution on this market. However, none of these factors make NAKIVO a poor choice for enterprise data backup software. To the contrary, it is a versatile enterprise backup and recovery system that is fast, responsive, and relatively easy to work with. NAKIVO offers on-demand file recovery, impressive backup performance, easy first-time configuration, and an impressive customer support team. However, NAKIVO’s services are rather expensive, and it shares the bane of most backup solutions: lackluster reporting/logging capability. Storage destinations are also limited.

Commvault is all about applying the cutting-edge technologies of their data backup and recovery solution to provide the best experience possible with various file types, data sources, backup types, and storage locations. Commvault is known for the pinpoint accuracy of its backups for VMs, databases or endpoints, VM recovery, unstructured data backup, data transfer, etc. Commvault integrates with more than a dozen cloud storage providers, including VMware, AWS, Azure, and many more. On the other hand, there are some areas in which Commvault falls short, according to some customer reviews, such as UI friendliness.
Customer ratings:
- Capterra – 4.6/5 stars based on 47 customer reviews
- TrustRadius – 7.7/10 stars based on 226 customer reviews
- G2 – 4.4/5 stars based on 160 customer reviews
Advantages:
- Easy connection with complex IT infrastructures
- A significant number of integrations to choose from
- Backup configuration is simple
Shortcomings:
- Not the most beginner-friendly solution on the market
- Takes a significant amount of time to set up and configure
- Basic logging functions are lacking
Pricing:
- Commvault’s pricing information is not publicly available on its official website and the only way to obtain such information is by contacting the company directly for a demo showcase or a free 30-day trial.
- The unofficial information suggests that Commvault’s hardware appliances’ price ranges from $3,400 to $8,781 per month.
Customer reviews (original spelling):
- Sean F. – Capterra – “We’ve been using Commvault’s backup product for several years now and although a complex product due to all it can do it is still the best I’ve used in a corporate environment. In my opinion it really is only for larger businesses but I can see how a small business could still get some benefits from the product. We use it to backup our File, Email, Database servers and all of our VMware virtual infrastructure. As everything is located in one console you don’t have to go far to find what you need and there are agents for nearly any operating system or application typically used in an enterprise environment.”
- Doug M. – Capterra – “As the title says “Migrated to Hyperscale and no looking back”. We have great sales people and excellent support from Commvault.”
The author’s personal opinion about Commvault:
Commvault is a relatively standard enterprise-grade backup solution that uses a variety of cutting-edge technologies to provide its customers with the best possible user experience. Commvault works with containers, cloud storage, VMs, databases, endpoints, and more. It delivers a fast and accurate backup and recovery experience, it is integratable with a variety of cloud storage providers, and it is relatively easy to set up backup tasks with it. However, Commvault is not known for its low prices. At the same time, it suffers from a lack of logging/reporting data for most of its features, and its first-time setup is notoriously long and complicated.

It is now fairly common for any company’s data to be spread across hundreds of different devices, due to workforce mobility and the rapid rise of various cloud services. Unfortunately, this change also makes it rather difficult to ensure that each and every device storing the company’s data is properly protected. Services like Druva Cloud Platform come in handy in these situations, offering a wealth of data management options across different devices and applications. The platform itself works as-a-service and offers easier backup and recovery operations, better data visibility, less complex device management, as well as a range of regulatory and compliance operations.
Customer ratings:
- Capterra – 4.7/5 stars based on 17 customer reviews
- TrustRadius – 9.7/10 stars based on 489 customer reviews
- G2 – 4.7/5 stars based on 614 customer reviews
Advantages:
- GUI as a whole receives a lot of praise
- Backup immutability and data encryption are just an example of how serious Druva is when it comes to data security
- Customer support is quick and useful
Shortcomings:
- First-time setup is not easy to perform by yourself
- Windows snapshots and SQL cluster backups are simplistic and barely customizable
- Slow restore speed from cloud
Pricing:
- Druva’s pricing is fairly sophisticated, with different pricing plans depending on the type of device or application that is covered. Actual prices have also now been deleted from the public pricing web page, leaving only the detailed explanation of the pricing model itself intact.
- Hybrid workloads:
- “Hybrid business” – calculated per Terabyte of data after deduplication, offering an easy business backup with plenty of features such as global deduplication, VM file level recovery, NAS storage support, etc.
- “Hybrid enterprise” – calculated per Terabyte of data after deduplication, an extension of the previous offering with LTR (long term retention) features, storage insights/recommendations, cloud cache, etc.
- “Hybrid elite” – calculated per Terabyte of data after deduplication, adds cloud disaster recovery to the previous package, creating the ultimate solution for data management and disaster recovery
- There are also features that Druva sells separately, such as accelerated ransomware recovery, cloud disaster recovery (available to Hybrid elite users), security posture & observability, and deployment for U.S. government cloud
- SaaS applications:
- “Business” – calculated per user, the most basic package of SaaS app coverage (Microsoft 365 and Google Workspace, the price is calculated per single app), offers 5 storage regions, 10 GB of storage per user, as well as basic data protection
- “Enterprise” – calculated per user for either/or Microsoft 365 or Google Workspace coverage with features such as groups, public folders, as well as Salesforce.com coverage (includes metadata restore, automated backups, compare tools, etc.)
- “Elite” – calculated per user for Microsoft 365/Google Workspace, Salesforce, includes GDPR compliance check, eDiscovery enablement, federated search, GCC High support, and many other features
- Some features here are also purchasable separately, such as Sandbox seeding (Salesforce), Sensitive data governance (Google Workspace & Microsoft 365), GovCloud support (Microsoft 365), etc.
- Endpoints:
- “Enterprise” – calculated per user, offer SSO (Single Sign-On) support, CloudCache, DLP support, data protection per data source, and 50 Gb of storage per user with delegated administration
- “Elite” – calculated per user, adds features such as federated search, additional data collection, defensible deletion, advanced deployment capabilities, and more
- There are also plenty of features that could be purchased separately here, including advanced deployment capabilities (available in the Elite subscription tier), ransomware recovery/response, sensitive data governance, and GovCloud support.
- AWS workloads:
- “Freemium” is a free offering from Druva for AWS workload coverage, it covers up to 20 AWS resources at once (no more than 2 accounts), while offering features such as VPC cloning, cross-region and cross-account DR, file-level recovery, AWS Organizations integration, API access, etc.
- “Enterprise” – calculated per resource, starting from 20 resources, has an upper limit of 25 accounts and extends upon the previous version’s capabilities with features such as data lock, file-level search, the ability to import existing backups, the ability to prevent manual deletion, 24/7 support with 4 hours of response time at most, etc.
- “Elite” – calculated per resource, has no limitations on managed resources or accounts, adds auto-protection by VPC, AWS account, as well as GovCloud support and less than 1 hour of support response time guaranteed by SLA.
- Users of Enterprise and Elite pricing plans also have the ability to purchase the capability to save air-gapped EC2 backups to Druva Cloud for an additional price.
- It is easy to see how one gets confused with Druva’s pricing scheme as a whole. Luckily, Druva themselves have a webpage dedicated to creating a personalized estimate of a company’s TCO (Total Cost of Ownership) with Druva in just a few minutes (a pricing calculator).
Customer reviews (original spelling):
- Andy T. – Capterra – “Our original POC when testing this product was very thorough and we were given ample time to test it and make sure it was going to fit how we needed it. Setting it up was incredibly easy and we were able to figure out a lot of the features on our own with minimal help. When we needed help, the team we were working with was great. We also had to work with support and that was great as well.”
- Dinesh Y. – Capterra – “My experience with Druva endpoint is amazing. From the time of onboarding this software I am not worried about data loss of the users. But I think Druva should consider more discounts for NGO’s as well as corporate so that everyone can use it extensively.”
The author’s personal opinion about Druva:
Druva’s cloud backup platform was built to solve the rather popular problem of managing hundreds of different devices within the same system, which is why it is rather obvious that Druva’s solution mainly targets large businesses and enterprises. The solution itself is provided on a SaaS basis, capable of protecting a wide variety of devices, including endpoints, databases, VMs, physical storage, and so on. Druva’s solution offers a wealth of backup and recovery features, impressive data protection capabilities, and compliance with a number of legal and regulatory standards. Druva’s pricing model is rather confusing, first-time setup is not an easy process, and it is unlikely to work well for an organization with large data volumes. Integration with some VM’s and databases is also very limited.

Zerto is a good choice in a multifunctional backup management platform with a variety of features. It offers everything you’d want from a modern backup and restore solution: CDP (continuous data protection), minimal vendor lock-in, and more. It is used with many different storage types, ensuring complete data coverage from the start.
Zerto has offered data protection as one of its core strategies from day one, offering applications the ability to be generated with protection from the start. Zerto also has many automation capabilities, is capable of providing extensive insights, and works with different cloud storages at once.
Customer ratings:
- Capterra – 4.8/5 stars based on 25 customer reviews
- TrustRadius – 8.3/10 stars based on 122 customer reviews
- G2 – 4.6/5 stars based on 73 customer reviews
Advantages:
- Management simplicity for disaster recovery tasks
- Ease of integration with existing infrastructures, both on-premise and in the cloud
- Workload migration capabilities and plenty of other features
Shortcomings:
- Is only be deployed on Windows operating systems
- Reporting features are somewhat rigid
- Is rather expensive for large enterprises and businesses
- Limited scalability
Pricing:
- The official Zerto website offers three different licensing categories – Zerto for VMs and Zerto for SaaS
- Zerto for VMs includes:
- “Enterprise Cloud Edition” as a multi-cloud mobility, disaster recovery, and ransomware resilience solution
- “Migration License” as a dedicated license for data center refreshes, infrastructure modernization, and cloud migration
- Zerto for SaaS, on the other hand, is a single solution that covers M365, Salesforce, Google Workspace, Zendesk, and more
- There is no official pricing information available for Zerto’s solution, it is acquired only via a personalized quote or purchased through one of Zerto’s sales partners
Customer reviews (original spelling):
- Rick D. – Capterra – “Zerto software and their amazing support team have allowed my company to bring in tens of thousands of dollars in new revenue by making it easy to migrate clients from Hyper-V or VMware to our VMware infrastructure.”
- AMAR M. – Capterra – “It’s a great software for any large organization. We use it both as a backup utility and DR site. Both sites work flawlessly without any issues. Support is a little hard to get but they are quite fast at responding, just not with the correct tech.”
The author’s personal opinion about Zerto:
Zerto is an interesting option for medium-sized backup and recovery workloads. As a dedicated backup management platform, it was purpose-built to handle such tasks in the first place. Zerto’s main solution offers ransomware resilience, data mobility, and disaster recovery in a single package, while also being capable of working with a variety of different storage options. It is a Windows-exclusive solution, and the price tag tends to scale up quickly for large companies, but the ability to perform workload migrations and integrate with different systems is usually worth far more than any price tag for large companies. Security and scalability may, however, be a significant concern for larger organizations.

Barracuda is a fairly unusual company, in that it offers configurable multifunctional backup appliances as a way to provide backup and recovery features. Barracuda Backup creates backups of applications, emails, and regular data. It offers extensive deduplication, data encryption, centralized data management, and plenty of other features in the backup and recovery department.
Customer ratings:
- TrustRadius – 7.6/10 stars based on 103 customer reviews
- G2 – 4.4/5 stars based on 52 customer reviews
Advantages:
- Barracuda’s user interface is relatively simple and easy to navigate, and creating backup jobs is a rather intuitive process
- Separate schedules could be set up for every single source that is backed up by Barracuda Backup’s appliance
- Data retention is also completely customizable and allows for every backup source to be customized separately
Shortcomings:
- Barracuda’s pricing policy is not what you would call egregious, but it is high enough for plenty of smaller businesses to not use it purely because they cannot afford it in the long run
- The solution’s reporting capabilities are rather basic and filtering through multiple reports is a bit of a problem
- Every first-time loading of the solution takes quite a lot of time, no matter how fast the connection or the hardware in question actually is.
- Lacks Kubernetes support
- Disaster Recovery has some strict limitations
Pricing (at time of writing):
- There is no specific public pricing available for Barracuda Backup, only by requesting a personalized quote.
- The way Barracuda collects data for such a quote is rather interesting: there is an entire configuration tool available that allows potential customers to choose from a number of options for Barracuda to better understand the client’s needs.
- This tool takes the user through five different steps before dropping the user to the last page with the request to “contact Barracuda to proceed,” including:
- Physical Locations – offers the ability to show how many different locations the client wants to cover, as well as the amount of raw data necessary (the basic setting is 1 location and 3TB of data)
- Deployment – the ability to choose between deployment options, there are three options to choose from: physical appliance, virtual appliance, and managed service
- Offsite Replication – an optional feature to replicate your data somewhere as an offsite storage, there is a choice between Barracuda’s own cloud, AWS, network transfer to another physical location, or no replication at all (this particular option is not recommended)
- Office 365 Backup – a short and simple choice between choosing to create backups of existing Office 365 data or to decline the option if you do not wish this data to be backed up or there is no data at all
- Support Options – a choice between three possible options, including the basic update package and the 8-to-5 customer support, an option with instant equipment replacement in case of a hardware failure and the 24/7 customer support, and a separate option for a dedicated team of engineers to be assigned to your specific company’s case
Customer reviews (original spelling):
- Amanda Wiens – TrustRadius – “With the Barracuda Backup tool, we have all unified and centralized management. And regardless of location, we have a single console for managing cloud and simplifying everything. In our scenario, it is a large environment, and we recommend using a virtual infrastructure with a great fiber link. Backups and restoration are speedy and secure. It is undoubtedly the best solution in this field.”
- Josh McClelland – TrustRadius – “For larger environments, with virtual infrastructure in place, and the network bandwidth to support it, a Barracuda backup is great. It’s easy to back up an entire cluster, or just a single server. When it comes to restoring or spinning up a downed machine, the Barracuda Backup is second to none in these sorts of environments. For the smaller clients, with budget concerns, only a few servers, not having the ability to spin up a failed server on the backup appliance itself is a little painful since we’d have to replace the physical hardware before getting services back online. I think having this ability would make for a great selling point to those smaller to medium size businesses that could benefit from this product.”
The author’s personal opinion about Barracuda Backup:
Barracuda Backup is an interesting take on a hardware-based backup solution, using hardware appliances to provide data backups, email backups, application backups, and more. Its interface is easy to work with, and the solution also offers quite a lot of customization at different levels of the backup process. There’s also Barracuda Backup’s rather basic set of reporting features. Because the solution relies heavily on hardware, rather than software, the price of the solution is that much higher, which could be too much for smaller or middle-sized businesses, but that factor is not as important for large-scale enterprises that would be willing to pay a higher price for complete data protection for their information. Overall though, there have been significant questions about Barracuda Backup’s tech support, scheduling manager, and user interface.
Feature and Capability Comparison for Each Backup Solution
The amount of information presented above is sure to overwhelm some readers, especially when comparing specific solutions with one another. To try and mitigate that issue, we have also created a table comparing all software we reviewed, across several different parameters:
- Deduplication support
- Container (OpenStack, Docker, etc.) support
- Mobile app support
- CDP (Continuous Data Protection) support
- Immutable backup support
These specific solutions were chosen for this comparison for one simple reason. Most of these backup solutions are well-known and respected in the enterprise software field, which makes it difficult to find basic features and functions that some solutions do not have. For example, parameters such as cloud support, disaster recovery, and data encryption were excluded simply because every single solution on the list already has them, completely invalidating the whole point of comparing software with one another.
As such, we have chosen five different parameters that are actually comparable across multiple software examples.
| Software |
Deduplication |
Container Support |
Bare Metal Recovery |
CDP Support |
Immutable Backups |
| Rubrik |
Yes |
Yes |
Yes |
Yes |
Yes |
| Unitrends |
Yes |
No |
Yes |
Yes |
Yes |
| Veeam |
Yes |
Yes |
Yes |
Yes |
Yes |
| Commvault |
Yes |
Yes |
Yes |
Yes |
Yes |
| Acronis |
Yes |
Yes |
Yes |
Yes |
Yes |
| Cohesity |
Yes |
Yes |
Yes |
Yes |
Yes |
| IBM Spectrum |
Yes |
Yes |
Yes |
Yes |
Yes |
This table is also separated into two halves equal in size to simplify its navigation for the end user. The separation itself is based solely on the convenience for the reader.
| Software |
Deduplication |
Container Support |
Bare Metal Recovery |
CDP Support |
Immutable Backups |
| Veritas |
Yes |
Yes |
Yes |
Yes |
Yes |
| Dell Data Protection Suite |
Yes |
Yes |
Yes |
No |
Yes |
| NAKIVO |
Yes |
No |
No |
Yes |
Yes |
| Bacula Enterprise |
Yes |
Yes |
Yes |
Yes |
Yes |
| Druva |
Yes |
Yes |
No |
Yes |
Yes |
| Zerto |
No |
Yes |
No |
Yes |
Yes |
| Barracuda |
Yes |
No |
No |
No |
No |
It should be noted that all software is being improved and expanding on a regular basis, which is why it would also be a good idea to double-check the software’s capabilities before choosing one of these options.
Enterprise Backup Software Best Practices: Key Features to Prioritize
Selecting the right enterprise backup solution requires careful evaluation of many technical and business factors that will impact your organization’s data protection strategy. The following key considerations are presented with the goal of helping to identify which backup software best aligns with specific organizational requirements of each company. Considerations in question are:
- Extensive data protection
- Support for different backup policies
- Deduplication and compression
- Disaster recovery and business continuity
- Support for different storage media types
- Flexible data retention
- Scalability and performance requirements
- Performance benchmarks and scalability metrics
- Integration and compatibility needs
- Vendor support and service level agreements
Extensive Data Protection
Features such as backup immutability, backup data encryption, 3-2-1 rule support, and granular access control lists are essential for protecting information against any kind of tampering. Enterprises across the world are constant targets of ransomware attacks of all kinds, so protection of backed up data must be at its strongest.
Support for Various Backup Policies and Backup Levels
Different backup variations are suitable for specific use cases and situations. Full backups are slow, but include all of the folders and files within the backed up environment. Differential backups copy only those files modified since the last full backup. Incremental backups cover only data modified since the previous backup, no matter the type. Enterprise-ready solutions frequently face large datasets, which is why the best of them also provide the opportunity to create synthetic full backups: a new full backup composed of all incrementals since the last full backup, conserving storage space, network bandwidth and budgets.
Deduplication and Compression
Data deduplication and compression are both essential for reducing storage costs and improving backup performance for enterprise environments. Deduplication eliminates redundant data blocks, storing only unique data segments and achieving significant storage reduction ratios, depending on organizational duplication patterns and data types. Compression further reduces storage requirements with efficient data encoding, commonly achieving 2:1 or even 4:1 space savings. Enterprise backup solutions must support both local and global deduplication, while also offering flexible compression options that balance CPU resource consumption and storage savings. These technologies have a direct impact on the TCO, due to their ability to reduce storage infrastructure requirements, network bandwidth utilization during replication, and long-term archival costs.
Disaster Recovery and Business Continuity
Minimal downtime and ensured business continuity are critical parameters for enterprises, so backup solutions for enterprises must offer automated failover for business-critical systems and support high availability infrastructures. Data replication to offsite storage like tape is also necessary for resilience. A very important aspect of a successful DR (Disaster Recovery) is bare metal backup and recovery, which should be supported for both Windows and Linux environments.
Support for Different Storage Media Types
The majority of enterprises run sophisticated systems that consist of multiple storage types with complex infrastructures. The ability to support different storage media types, be it on-premise servers, virtual machine disks, enterprise cloud storage (both public and private), or magnetic tape, is a must-have for any enterprise backup solution. With the rise of 3-2-1 rule, air gapping and other security measures, enterprise-grade backups no longer support only one specific storage type without the ability to backup to others.
Flexibility in Data Retention Options
The capability to implement long-term and short-term data retention policies is a significant advantage in this market, because enterprises and large corporations must adhere to various regulatory requirements (including the necessary data storage time period) on the different types of data they own. A good backup solution should offer flexible retention controls, support custom deletion protocols, and automated pruning jobs.
Scalability and Performance Requirements
Enterprise backup solutions must be able to handle growing data volumes and increases in infrastructure complexity without sacrificing performance. The solution must offer reliable execution of backup and recovery operations in an integral and consistent manner, while supporting concurrent backup instances and tools to optimize data volume transmission. Support for HPC and big data IT infrastructures is also preferred in most cases, because of the need to deal with petabytes of information and millions of files on a regular basis.
Performance Benchmarks and Scalability Metrics
Measurable performance capabilities are necessary for enterprise backup solutions if they are to talk about the specifics of their performance. Backup throughput rates (5-50 TB/hour in enterprise environments in most cases), concurrent backup job handling (ability to work with 100-1000+ operations simultaneously), database backup speed and recovery time measurement (RTOs) are just a few examples of such metrics. As for the scalability metrics, they are data volume capacity limits, network bandwidth utilization efficiency, and deduplication processing speed, among others. Vendor-provided performance data must be evaluated against an organization’s specific infrastructure requirements to ensure that selected solutions would be able to handle current workloads and even accommodate future expansion without performance losses.
Integration and Compatibility Needs
Any backup solution must provide seamless integration with the existing IT infrastructure of your organization, including native support for large-scale databases (Oracle, SQL Server, PostgreSQL, SAP HANA), support for heterogeneous environments (different hardware and software types), and compatibility with enterprise monitoring systems and integration with enterprise BI tools. Cross-platform administration tools that are easy to use and offer extensive functionality are also high on the priority list for any professional backup software.
Vendor Support and Service Level Agreements
Enterprise backup implementations require the following in vendor support:
- Comprehensive vendor support frameworks
- Guaranteed response times for critical issues
- Multiple support channels such as phone, email, on-site, etc.
- Clear definition of escalation procedures attached to dedicated account management (for large deployments).
Service level agreements, on the other hand, must specify:
- Resolution timeframes (tiered support models ranging from basic business-hour coverage to premium 24/7 support)
- System uptime guarantees (99.9% typically)
- Support coverage hours that align with organizational operations
It is highly recommended that organizations evaluate vendor support infrastructure, including the presence of language capabilities, on-site support availability for hardware issues, regional support centers, and the track record of the vendor when it comes to meeting SLA commitments. Different support delivery models include their own range of capabilities, such as:
- Self-Service: Knowledge base, documentation, community forums
- Managed Services: Vendor manages backup infrastructure remotely
- Hybrid: Combination of professional and self-service support
- White-Glove: Dedicated support engineer assigned to account
Evaluating these factors in a systematic fashion against your company’s specific needs, current infrastructure capabilities, and future growth plans would help ensure that the selected backup solution would be able to meet both today and tomorrow’s requirements of your business.
Who are the most frequent enterprise backup solutions users?
Enterprise backup software has a very specific audience of certain user groups. Most common examples of such are:
- Government and military organizations
- HPC data centers
- Research organizations
- Fintech field
- Healthcare field
- E-commerce and retail
- Universities and education
Government and Military Organizations
Both military and government organizations work with information just as often as any other commercial company, if not more often. However, the requirements for data security and backup capabilities in these cases are much more strict and extensive, meaning that most backup solutions could not operate within these boundaries without completely changing their entire backup process. Thus, such organizations require true enterprise-grade solutions for backup.
HPC Data Centers
HPC data centers are created to analyze large data masses for analytical or AI-oriented purposes, and big data in large-scale, high-transactional databases is how these data masses are stored for further analysis or processing. However, protecting massive data volumes is not something that every backup solution is capable of, and in addition, this information must be as secure as every other data type. Enterprise backup software is the only obvious choice for such organizations, but beware: there are barely a handful of solutions that meet the typical needs of a true HPC environment. Currently, Bacula Enterprise, with its ability to handle billions of files and integrate with high performance storage and file systems, appears to be the HPC market leader.
Research Organizations
Many R&D organizations generate massive data amounts regularly. The data in question is necessary for various processes, and protecting this data is paramount for any business. The data in question includes datasets for analysis tasks, data for complex simulations, personal medical information, experiment results, etc. Many of these organizations are running IT environments that are approaching HPC specifications.
Fintech Field
Many financial tech businesses, be they banks, investment firms, insurance brokers, etc., are required to handle massive data volumes on a regular basis, often in real time. Extensive data protection solutions are necessary to protect this data, while remaining compliant with PCI DSS (Payment Card Industry Data Security Standard), SOX (Sarbanes-Oxley Act), and other regulations.
Healthcare Field
The healthcare field is an entirely separate field of work with its own set of regulations regarding sensitive data storage. Businesses dealing with protected health information must comply with regulatory frameworks such as HIPAA. Introducing an enterprise backup solution in this realm is nearly always necessary to correctly protect data, ensuring fast data recovery in case of a disaster and providing data continuity in a very demanding industry.
E-commerce and Retail
Customer data that retailers regularly collect consists of many different pieces of information, from transaction records and payment data to inventory information and more. Much of this data must be protected according to one or several regulatory frameworks. Enterprise backup solutions exist to protect and safeguard information like this, combining compliance with protection in a single package.
Universities and Education
Universities and other educational organizations typically produce and store significant volumes of data, whether students data, administrative personnel data, research data and science projects. Because of the sheer amount of data, the educational sector typically requires enterprise-level backup solutions to mitigate risks, and to manage and protect its data.
Understanding the 3-2-2 Backup Rule in Enterprise Security
The 3-2-2 backup rule is the evolution of the traditional 3-2-1 backup strategy, designed to address the increase in complexity of an average cyber threat, along with the ever-increasing enterprise data protection requirements. It is an enhanced framework that maintains the foundational principles of data redundancy and adds an extra layer of geographic protection – something that has become essential for modern enterprise environments facing increasingly sophisticated ransomware attacks and natural disasters.
What is the 3-2-2 Backup Rule?
The 3-2-2 backup rule suggests using three copies of critical data, stored on two different media types, in two geographically separate locations. It is an improvement over the original 3-2-1 backup rule that required only a single offsite copy, distributing backup data across several locations to eliminate single points of failure capable of disrupting both primary and backup systems at once.
To reiterate, there are three core components to the 3-2-2 backup strategy:
- 3 copies of data: Primary production data and two additional backup copies
- 2 different storage media: A combination of diverse storage technologies, like tape libraries and disk arrays
- 2 separate locations: Geographic distribution across sites, data centers, or cloud regions
Using 3-2-2 backup rule provides businesses with enhanced security using geographic redundancy without sacrificing the performance advantages of on-site backups. In most cases, the users of this strategy store two data copies locally using different media types and maintain a third copy in a secondary data center or a geographically separate location, typically in the cloud.
Enterprise Implementation of the 3-2-2 Rule in Modern Backup Software
Implementing the 3-2-2 rule in enterprise environments requires backup software that supports complex multi-location replication workflows. Luckily, many modern enterprise backup solutions, like Commvault, Veeam, and Bacula Enterprise, have full support for automated replication between sites, which enables organizations to maintain fully synchronized copies of information across multiple geographically separate locations with minimal manual intervention.
The selection of storage media is critical for this framework, with most businesses choosing high-performance disk arrays as primary backup storage, tape libraries as low-cost storage for retention purposes, and cloud storage as the means of achieving geographic distribution.
For the 3-2-2 backup strategy to work, it is critically important to ensure that each media type operates independently, avoiding cascading failures that compromise multiple copies of the data at once. As for long-term archival strategies, they often have dedicated storage tiers, with Amazon Glacier Deep Archive or Azure Archive Storage being prime examples of compliance-driven retention requirements spanning multiple years.
The implementation process itself normally includes three major steps:
- Configuring primary backup jobs to be stored using local storage media
- Establishing automated rules for replication to a secondary on-premises location (or private cloud)
- Setting up cloud integration to create third geographic copy
Most enterprise backup platforms achieve these goals using policy-based automation, which ensures consistent protection levels without becoming an overwhelming burden for the IT department.
Ensuring Recovery Success and Compliance of 3-2-2 Backups
The effectiveness of the 3-2-2 backup approach hinges on regular verification and testing procedures, validating data integrity of all copies and locations. Automated backup verification processes are highly recommended here, checking data consistency, performing recovery tests, and maintaining thorough audit trails for compliance.
Recovery planning must also take into account various failure scenarios, from localized hardware failures to regional disasters, all of which have their own approaches to remediation. Luckily, the 3-2-2 framework offers flexible recovery options. IT teams optimize the organization’s recovery time objectives by choosing the most appropriate backup copy from which to recover, depending on the nature of the incident.
As for organizations that are subject to regulatory requirements, the 3-2-2 rule complies with regulatory frameworks mandating data protection across multiple locations. It also satisfies requirements for business continuity planning and offers documented evidence of robust data protection measures during regulatory reviews or audits.
Gartner’s Magic Quadrant for Enterprise Backup and Recovery Software Solutions
Gartner’s Magic Quadrant for Backup and Data Protection Platforms gives enterprise decision-makers an authoritative assessment of leading vendors in the market. This research is conducted annually by Gartner analysts, evaluating vendors based on their ability to execute current market requirements, along with their completeness of vision for future market direction. This analysis serves as an important reference material for enterprise organizations investing in backup infrastructure, making it easier to understand vendor capabilities, market positioning, and strategic direction in the modern-day backup landscape.
Gartner’s Evaluation Criteria for Enterprise Backup Solutions
Gartner evaluates enterprise backups with a comprehensive two-dimensional framework, assessing the current capabilities and the future potential of different options. The evaluation methodology serves as an objective criteria for comparing vendors across a variety of critical factors.
Ability to Execute measures the vendor’s current market performance and operational capabilities. This dimension evaluates several important factors, including:
- Product or service quality and features
- Overall financial viability
- Sales execution
- Pricing strategies
- Market responsiveness
- Track record
- Marketing execution effectiveness
- Customer experience delivery
Gartner weights these criteria differently, with market responsiveness and product/service capabilities considered the most important factors, followed by customer experience. Marketing execution, on the other hand, is considered the least important factor on this list.
Completeness of Vision measures a vendor’s strategic understanding and future market direction. In this dimension, the assessment focuses on a completely different range of factors, such as:
- Market understanding
- Alignment with customer requirements
- Effectiveness of marketing and sales strategy
- Offering and product strategy innovation
- Sustainability of the business model
- Vertical and industry strategy focus
- Geographic market strategy
- Capabilities of innovation and differentiation
Market understanding, product strategy, and innovation are the most important factors here, according to Gartner, while vertical strategy is the least valuable point on the list.
The intersection of these two dimensions creates four distinct quadrants that provide insight into how each vendor is positioned. Leaders excel in both execution and vision, while Challengers demonstrate strong execution capabilities with limited vision. Visionaries showcase innovative thinking but face challenges with execution, and Niche Players either have a strong focus on specific market segments or are still developing capabilities in both dimensions.
Analysis of the Best Enterprise Backup Solutions According to Gartner in 2025
Based on Gartner’s 2025 Magic Quadrant analysis, presented in an image below, six vendors in total have achieved Leader status. Bacula Enterprise is not assessed in this analysis as it does not disclose its annual revenue:
- Veeam
- Commvault
- Rubrik
- Cohesity
- Dell Technologies
- Druva

Veeam maintains its leadership position with established its market presence in diverse geographic regions, combined with strong ransomware protection capabilities. Its security features include AI-based in-line scanning, Veeam Threat Hunter, and IOC detection, supported by its Cyber Secure program that provides a real-time incident response and ransomware recovery warranty. The platform’s clients can take advantage of versatile data restoration and mobility with cross-hypervisor restorations between major hypervisors, as well as direct restore functionality from on-premises workloads to Azure, AWS, and Google Cloud Platform.
Commvault
Commvault demonstrates its industry leadership with comprehensive cloud workload coverage and strategic acquisition capabilities. It offers broad IaaS and PaaS support with native Oracle, Microsoft Azure DevOps, and government cloud coverage for AWS, Azure, and Oracle Cloud Infrastructure. The acquisition of Appranix has allowed Commvault to enhance its Cloud Rewind strategy, delivering improved cloud application infrastructure discovery, protection, and recovery with completely orchestrated protection for the application stack and improved recovery speeds.
Rubrik
Rubrik is an excellent option for cyberrecovery and detection purposes, with its Security Cloud platform driving comprehensive protection for both data and identity. Rubrik’s solution features AI-based in-line anomaly detection, advanced threat monitoring with hunting capabilities, and even orchestrated recovery across hybrid identity environments. The solution is distributed using a Universal SaaS Application License that supports unlimited storage capacity per user with portability features between supported SaaS applications.
Cohesity
Cohesity gained improved capabilities with its acquisition of Veritas’ NetBackup and Alta Data Protection portfolios, offering comprehensive workload coverage, no matter if they’re on-premises, SaaS, or multicloud. Its newly-combined portfolio provides broad geographic coverage with an expansive global infrastructure and support teams. Enhanced cyberincident response services are also included in the package using their Cyber Event Response Team, partnered with industry-leading providers (Palo Alto Networks, Mandiant).
Dell Technologies
Dell Technologies emphasizes its deep integration with Dell storage infrastructure, using PowerProtect Data Manager’s integration with PowerMax and PowerStore storage arrays, combined with DD Boost and Storage Direct Protection capabilities. Its built-in AI Factory integration for on-premises AI infrastructure includes security measures for Kubernetes metadata, training data models, vector databases, configurations, and parameters. There are also enhanced managed detection and response services that incorporate CrowdStrike Falcon XDR Platform licensing, as well.
Druva
Druva demonstrates powerful execution of its product strategy, using an enhanced SaaS-based platform architecture hosted using AWS. The underlying architecture allows Druva to accelerate delivery of critical offerings, including Azure Cloud storage tenant options, support for Microsoft Entra ID, and optimized protection for Amazon S3, Amazon RDS, and Network-Attached Storage (NAS). The AI-powered operational assistance of Druva through Dru Assist and Dru Investigate enhances user experience and security insights, delivering proactive ransomware defense using managed services.
Other Vendors in the Magic Quadrant
The remaining vendors occupy other quadrants, based on their strengths and current market focus:
- Huawei appears in the role of a Challenger, with strong flash-based scale-out appliance architecture and multiple layers of ransomware detection capabilities (but with a limited scope of multicloud protection)
- HYCU is categorized as a Visionary, offering comprehensive SaaS protection strategy with strong support for Google Cloud Platform
- IBM is also considered a Visionary, delivering AI integration through watsonx and integrated early threat detection capabilities
- Arcserve, OpenText, and Unitrends are all Niche Players, focusing on specific market segments: Arcserve targets midmarket environments, OpenText emphasizes internal product integrations, and Unitrends serves SMB markets via managed service providers
It should also be noted that the absence of a vendor on the Magic Quadrant does not directly translate into any lack of viability. For example, while Bacula Systems did not meet all inclusion criteria, it was still included in the Honorable Mentions section as a software-based offering with open-source and commercially licensed and supported products.
How to Verify the Credibility of Enterprise Backup Software Using Gartner.com?
Enterprise organizations regularly rely on Gartner’s research platform to make informed backup software decisions and validate vendor claims. Although access to complete research from Gartner does require an active subscription, organizations have the ability to use multiple strategies to verify vendor credibility and positioning. There are four primary approaches to verification covered here: direct Gartner research access, vendor reference validation, market trend verification, and supplementary validation sources.
Direct Gartner Research Access
Direct Gartner research access is the most comprehensive verification method, but requires the purchase of a Gartner subscription. The Magic Quadrant research comes with detailed vendor analysis with specific strengths and limitations, as well as customer reference data and financial performance metrics, both of which help validate vendor claims about market position, technical capabilities, or customer satisfaction. When given access to the full report, it is highly recommended to review the complete vendor profiles to gain a better understanding of the specific limitations and competitive advantages of each vendor that are relevant to each organization’s specific requirements.
Vendor Reference Validation
The accuracy of vendor reference validation is improved significantly with Gartner’s peer insights and customer review platforms. Although vendors commonly cite their Gartner’s positioning, customers should verify these claims by accessing research publications, specific quadrant placements, and any limitations or cautions provided in the analysis. Gartner performs a highly thorough research that explains why vendors have achieved their positioning, helping potential clients evaluate whether a specific solution aligns with their organizational needs.
Market Trend Verification
Market trend verification using Gartner’s strategic planning assumptions helps companies understand whether vendor roadmaps align with the general industry’s direction. With access to Gartner’s information, organizations would be able to evaluate vendor claims about AI integration, cloud capabilities, and security features against current industry trends to assess their strategic alignment.
Supplementary Validation Sources
Supplementary validation sources should be used alongside Gartner’s research for the most comprehensive vendor evaluation. Gartner’s findings are then cross-referenced against the reports of other analysts, as well as customer case studies, the results of independent testing, and proof-of-concept evaluations. Such an approach helps verify whether vendor capabilities match both specific organizational requirements and Gartner’s own assessment.
How to Choose an Enterprise Backup Solution?
Picking a single backup solution from a long list of competitors is extremely hard, given the many factors the potential customer must consider. To make the process easier, we have made a checklist that any customer would be able to rely on when attempting to choose a backup solution for their enterprise organization.
1. Figure Out Your Backup Strategy
Large-scale businesses and enterprises require a detailed backup strategy to make it easier to plan ahead and plan appropriate actions for specific situations, such as user errors, system failures, cyberattacks, etc.
Some of the most common topics that should be addressed in a backup strategy are:
- High availability
- Backup scheduling
- Backup policies
- Backup targets
- Audit requirements
- RTOs and RPOs
High Availability
Companies have distinct preferences in backup storage locations. One company may want to store backups in cloud storage, while another favors on-premise storage within its infrastructure. Determining the storage locations for future backups is an essential first step. In the context of the 3-2-1 rule, there must be several locations, both on- and offsite.
Example high availability infrastructure for enterprise:
2 backup servers: the primary one in the main data center, with the second one in another data center or in the cloud. A combination of storage systems following the 3-2-1 rule: on-premise NAS or SAN via RAID, cloud and tape for resiliency. Real-time block-level replication between both servers. Automated failover and load balancers for backup servers to minimize load. High-performance network switches and paths, fibre channel. All of the above with the monitoring system and automated alerts.
Backup Scheduling
Understanding when would be best to perform a system backup is key to ensuring that there are no interruptions or slow-downs in operations caused by a sudden backup process. Many backup solutions prefer to create full backups outside of business hours to avoid interruptions to the businesses themselves. However, it is possible that enterprises have so much data that creating full backups cannot be completed even if done overnight. In such situations, synthetic full backups are a better option.
Example backup schedule for enterprise:
Create full backup during weekends (for example, Sunday at midnight) to minimize impact on application performance. Perform incrementals at the end of each workday (for example, 11:30 PM, Monday to Saturday). A single differential backup on Wednesday night. Of course, for systems with critical importance (high-transactional DBs, for example) execute more incremental backups, probably several times per day.
| Day of Week |
Backup Policy |
Explanation |
| Sunday |
Full |
Complete snapshot of all data |
| Monday |
Incremental |
Capture changes since Saturday |
| Tuesday |
Incremental |
Capture changes since Saturday |
| Wednesday |
Differential |
Capture all changes since last full backup |
| Thursday |
Incremental |
Capture changes since Saturday |
| Friday |
Incremental |
Capture changes since Saturday |
| Saturday |
– |
No scheduled backups, preparation for full backup |
| Last Sunday of the Month |
Full + Offsite Storage |
Comprehensive monthly backup with redundancy (cloud archive or tape) |
Backup Policies
Determining backup policies wisely considers both available storage space and network bandwidth. A full backup would be best performed periodically, (once a week or a month, depending on your situation), and an incremental backup on a regular basis (daily, for example) to ensure data consistency. Differential backups fall between full and incrementals, because they require more storage space than incrementals, but are faster to restore than fulls. Choosing the proper mix of backup policies depends on data size, data type, data change frequency, RTO & RPO, and network and storage resources.
Sample enterprise backup policy:
Perform a full backup once a month during the weekend, when the network usage is at a minimum. Add 2-4 differential backups during the month to track changes since the last full. On top of that, add daily incrementals to track day-to-day differences. Use all incrementals once a month to create a synthetic full backup, in case a new full backup is not possible.
Backup Targets
The average company may have multiple storage types in its infrastructure. The main goal is determining the specific storage types for a backup solution, while also keeping the potential sizes of future backups in mind (since backups tend to grow in size as time goes on, and knowing when it is time to expand the existing storage or purchase more storage is important). Implementing tiered storage is also a good tactic, meaning essential datasets are stored in expensive storage with rapid recovery capabilities, while older or less critical datasets are backed up to slower cloud storage, like Amazon Deep Archive, or to tape media.
Audit Requirements
There are many industry-specific requirements and standards for data storage that the company must adhere to. Having a complete understanding of the regulations your company must adhere to is a great advantage in choosing a backup solution. For example, organizations will almost certainly have to comply with GDPR and CCPA, PCI DSS if you’re accepting online payments, HIPAA if you’re a medical organization, SOX if you’re publicly traded, CMMC if you’re working with US DoD, and others.
RTOs and RPOs
These parameters are some of the most important for any backup strategy. As their names suggest, RTO represents the maximum length of time the company is willing to endure before its operational status is restored. Conversely, RPO shows how much data the company is willing to lose without causing significant damage to its regular operations. Understanding the company’s needs in terms of RPO and RTO also makes it easier to figure out parameters such as recoverability, backup frequency, recovery feature set, and backup software SLAs.
Example RTO & RPO requirements for enterprise:
- Critical apps & high-transactional databases
- 1-2 hours RTO, 10 minutes RPO
- Regular work apps (CRM, ERP, etc)
- 4-6 hours RTO, RPO 1 hour
- Email, messenger and other communication apps
- 2-4 hours RTO, 30 minutes RPO
- File shares
- 24 hours RTO, 4 hours RPO
- Other non-critical and demo systems
- RTO 24-72 hours, 12-24 hours RPO
The process of finalizing the backup strategy as a single document must be a collaboration among multiple departments if the strategy is to adhere to the company’s objectives and business goals. Creating a concrete backup strategy is an excellent first step toward understanding what your company needs from an enterprise backup solution.
Additional Strategic Considerations
Several more factors contribute to the development of a successful backup strategy, such as:
- Data Volume and Classification: Assess the total data volume to be protected, categorized by criticality. High-priority information such as customer records, intellectual property, or financial information will demand more frequent backups with faster recovery capabilities than the systems surrounding archival data.
- Budget Allocation: Establish clear budget limits for hardware infrastructure, software licensing, ongoing maintenance, and staff training. Both capital expenditures (perpetual licenses, hardware) and operational expenses (subscription fees, support contracts, cloud storage) must be considered.
- IT Infrastructure Assessment: Evaluate existing network bandwidth, server resources, and storage capacity. Determine all requirements for integration with current systems, including cloud services, databases, and virtualization platforms.
- Security and Compliance Requirements: Identify applicable industry standards and regulations: GDPR, HIPAA, PCI DSS, SOX, etc. Establish security requirements with all regulatory prerequisites in mind, like audit trail capabilities, encryption standards, and access controls.
2. Research Backup Solutions for Enterprises
This entire step revolves around collecting information about backup solutions. A significant part of this step has already been done in this article, with our long and detailed list of business continuity software tools. Of course, it is possible to conduct a much more thorough analysis by calculating business-critical parameters and comparing different features based on the results of specific tests.
3. Calculate Total Cost of Ownership
Enterprise backup solutions are considered long-term investments, and performing a cost-benefit analysis and calculation of TCO (Total Cost of Ownership) makes it much easier to evaluate the software. Here is what needs to be taken into account during calculations:
- Cost of the license (perpetual or subscription-based model)
- Cost of hardware
- Implementation fees (if you plan to use outsourced integration)
- Cost of ongoing support and updates
- Cost of power, cooling and other utilities to run the backup system
- Cost of additional bandwidth and networks
- Cost of storage (disks, tape, cloud), as well as storage management software costs
- Cost of training personnel
4. Perform “Proof-of-Concept” (PoC) tests
Once you have identified a relatively small list of potential backup solutions, it is time to move on to the testing phase to ensure that the solution meets all your designated objectives. This is also where a more detailed evaluation of features must happen. The idea is to ensure that more essential capabilities are included in the backup solution so that you don’t trade “easy data recovery” for “easy first-time setup,” for example.
A good PoC should work within your IT environment and not on a demo stand, to make sure the system behaves as expected when put into production. The testing itself involves both feature testing and stress testing the whole system under a significant load. You should also test the vendor’s support team, their responsiveness and effectiveness, as well as their documentation. To succeed, define your objectives and success metrics clearly, and set a realistic timeline for all tests to keep the PoC time-efficient.
5. Finalize your choice & update DR procedures
At this point, there should be little or no doubt about the right enterprise backup solution for your situation. Creating your disaster recovery and business continuity plans for your new backup solution and its capabilities is essential. This is the final step of the process: ensuring that you have a detailed rulebook that specifies what actions are taken to protect each and every part of your system and what must be done if your system suffers some sort of data breach.
Enterprise Backup Software Pricing Models and Cost Considerations
Enterprise backup software pricing differs substantially across vendors and different licensing models have a direct impact on TCO and budget predictability. Understanding how different pricing structures operate assists organizations select the solution that best aligns with their financial constraints and growth projections, all while avoiding unexpected cost increases as data volume grows.
What are the Different Enterprise Backup Pricing Models?
Backup vendors that work with enterprise clients use several distinct pricing approaches, each of which has its advantages and limitations for specific organizational profiles:
- Capacity-based licensing charges businesses based on the total data volume protected. It includes raw data capacity, compressed data, or data after deduplication (depending on the vendor). Capacity-based offerings have straightforward cost correlations with data volumes but also result in unpredictable expenses when organizational data grows exponentially.
- Agent-based licensing provides cost calculations based on the number of protected endpoints, servers, or backup clients, irrespective of the total data volume. Organizations must pay for each system that needs backup protection, be they physical servers, virtual machines, or database instances. This model usually remains constant and predictable, even with significant data growth.
- Subscription-based licensing delivers backup software using recurring monthly or annual payments, often covering software updates, support services, and cloud storage allocation. Subscription models ensure access to the latest features and security updates for each client, while converting capital expenditures into operational expenditures.
- Perpetual licensing demands upfront software purchase, while updates and support are delegated to a separate contract with its own terms. Organizations with perpetual licenses own the software permanently but still must pay additional costs for ongoing support and version upgrades.
- Feature-tiered pricing is a range of several product editions with different capability levels, allowing organizations to pick and choose the functionalities that match their budget constraints and requirements. Advanced features like encryption, deduplication, or DR orchestration are rarely included in base pricing tiers.
Hybrid pricing models are also common, combining multiple approaches in the same platform, such as a base licensing fee with additional charges for advanced features. These models offer impressive flexibility but must be evaluated carefully to understand their total cost.
Data Volume Impact on Backup Costs
Data volume growth has a significant impact on the total cost of backup software, especially in capacity-based licensing models where expenses increase directly with data volumes.
Organizations that experience periods of rapid data growth face challenges associated with cost escalations in capacity-based pricing. A company protecting 10 TB of information initially may find its total protection cost doubling or tripling as total data volume reaches 20-30 TB over the span of several years. Such a linear relationship between cost and data volume is known for creating budget planning difficulties, resulting in unexpected infrastructure expenses.
Agent-based licensing models offer cost stability during data growth periods, as their licensing fees are not dependent on total data volume. Organizations with predictable endpoint counts but variable data growth may find agent-based licensing more effective than the rest, achieving budget predictability and accommodating expansion at the same time.
Deduplication and compression technologies are regularly used to reduce effective data volumes for capacity-based pricing, which potentially lowers total licensing costs. However, it is up to each organization to evaluate whether deduplication ratios will remain consistent with different data types and sources over time.
Planning for data expansion requires knowledge of organizational growth patterns, as well as backup frequency policies and regulatory retention requirements. Organizations should model pricing scenarios across 3-5 year periods to evaluate the total cost implications of different licensing methods.
Total Cost of Ownership Planning for Enterprise Backups
Total cost of ownership in enterprise backups extends far beyond software licensing to include hardware infrastructure, implementation services, ongoing maintenance, and operational expenses:
- Hardware and infrastructure costs – backup servers, storage arrays, network equipment, facility requirements. Costs vary significantly between on-premise deployments and cloud-based platforms.
- Implementation and professional services – initial setup, configuration, data migration, staff training. The complexity of a backup solution has a direct influence on this factor.
- Ongoing support and maintenance – software updates, technical support, system monitoring. 24/7 support with guaranteed response times is a common requirement for enterprise organizations, translating into more expensive premium support contracts.
- Operational expenses – power, cooling, facility space, dedicated staff for backup system management. Full-time equivalent staff costs for backup administration, monitoring, and disaster recovery planning are practically mandatory for enterprise organizations.
- Training and certification costs – current expertise with backup technologies and best practices. Regular training investments prevent operational issues while maximizing backup system effectiveness.
Different licensing approaches affect TCO values in different ways. Bacula Enterprise would be an outlier on the list of traditional licensing options, because it uses a subscription-based model that does not rely on volume-based costs, greatly improving the financial burden on enterprise clients with large data volumes. It offers cost predictability for these organizations, with expenses remaining stable regardless of current data growth patterns.
Organizations must evaluate pricing models against their specific growth patterns, budget constraints, and data characteristics to find the most economically suitable option for these enterprise requirements.
Enterprise On-Premise vs Cloud Backup Solutions
The choice between on-premise and cloud backup architectures for enterprises is one of the most critical decisions to address when an enterprise organization is creating a data protection strategy. This single decision directly influences technical capabilities, operational costs, security posture, and even the long-term scalability of the environment. Modern enterprise backup strategies actively incorporate hybrid approaches: a combination of deployment models that optimize for specific workloads and maintain comprehensive data protection at the same time.
On-Premises vs Cloud Backup Solutions for Large Businesses
On-premises backup solutions deploy backup software and storage infrastructure in the company’s own data centers. These solutions offer direct control over all aspects of a backup environment, including network infrastructure, backup servers, dedicated storage arrays, and tape libraries. With this, enterprises maintain complete ownership of their data, but while also bearing full responsibility for maintenance, upgrading, and disaster recovery planning of their infrastructure.
Cloud backup solutions use remote infrastructure managed by third-party providers, with backup services delivered using internet connectivity to secure, geographically distributed, data centers. These services range from simple cloud storage targets to highly sophisticated Backup-as-a-Service platforms capable of handling the entire process remotely. Cloud providers are responsible for maintaining the underlying infrastructure, as well as accommodating enterprise-grade SLAs, multi-tenant security frameworks, and regulatory compliance. They also often provide additional services, such as disaster recovery orchestration.
Hybrid backup solutions are an increasingly popular option in this market, combining on-premises and cloud components to get the best performance, cost, and protection levels from both solution types. Typical implementations of a hybrid backup solution include:
- Local backup appliances for quick recovery of frequently accessed data
- Automated replication capabilities to cloud storage as the means of long-term retention
- Rapid local recovery capabilities with cloud economics for offsite protection
Benefits and Limitations of On-Premise and Cloud Backup Solutions for Enterprises
Each backup deployment type has its distinct advantages and shortcomings that organizations must be aware of, evaluating them against their organizational requirements, budget constraints, and operational capabilities. We have collected the most noteworthy aspects of each platform in a table for the sake of convenience:
| Aspect |
On-Premise Solutions |
Cloud Solutions |
| Performance |
Superior speed with enterprise-grade high-bandwidth local networks, no internet dependency for backup or recovery |
Network-dependent performance, recovery speed is limited by internet bandwidth |
| Control & Security |
Complete enterprise control over retention, policies, and security configurations |
Provider-managed security with enterprise-grade implementations and certifications |
| Scalability |
Limited to hardware capacity, capital investment is necessary for expansion across multiple data centers and geographic locations |
Virtually unlimited scalability with automatic scaling and usage-based pricing |
| Cost Structure |
High upfront capital expenditure with predictable ongoing operational costs, |
Subscription-based model where costs scale with data volume and usage |
| Operational Burden |
Dedicated IT expertise is necessary for maintenance, troubleshooting, and disaster recovery |
Reduced operational burden with updates and infrastructure being managed on the provider side |
| Compliance |
Full customization for specific audit needs and regulatory requirements of enterprises |
Provider certifications may or may not need specific requirements, with potential concerns around data sovereignty |
| Disaster Recovery |
Needs separate DR planning and infrastructure investment |
Built-in geographic redundancy and disaster recovery capabilities |
What Should Be Considered When Choosing Between On-Premises and Cloud Backup Solutions within an Enterprise Market?
Selecting the most optimal backup deployment strategy requires careful evaluation of many interconnected factors that will vary significantly across organizations. The key considerations covered next are just a framework for making informed decisions and must be expanded with case-specific topics in each individual case.
Data and Performance Requirements
Data volume and growth patterns must be evaluated in any case, because cloud storage costs scale linearly with data volumes, while on-premises costs remain relatively flat after the initial investment. Current backup requirements and projected growth over the solution’s lifecycle directly impact the economic viability of both options. Recovery Time Objective also has a measurable effect on deployment choice, with on-premise solutions offering faster recovery for large datasets, while cloud solutions are limited by internet bandwidth, especially when it comes to the data volumes that enterprises deal with regularly.
Regulatory and Compliance Needs
Compliance requirements dictate deployment options on a regular basis, particularly in organizations that are subject to specific security frameworks or data residency restrictions. Enterprises must evaluate whether cloud providers are able to meet specific compliance requirements using appropriate specifications, data residency options, and comprehensive audit capabilities to satisfy regulatory scrutiny.
Technical Infrastructure Assessment
Critical considerations that are paramount for managing backup systems include existing network bandwidth, internet reliability, and the availability of internal IT expertise. Businesses with limited bandwidth or unreliable internet connectivity rarely find cloud backup solutions to be their preferred option for large-scale deployments. The availability of internal IT expertise, on the other hand, has a substantial impact on the viability of on-premise solutions, due to the necessity to conduct backup system management, troubleshooting, and disaster recovery planning on-site.
Financial Analysis Framework
Total cost of ownership must cover the solution’s expected lifecycle, including initial capital expenditures versus operational expenditures for budgeting purposes. Ongoing costs vary substantially between approaches: cloud solutions have predictable monthly costs, while on-premises deployments need power, cooling, and facility management expenses. It is important to model costs across multiple scenarios, not just normal operations but disaster recovery situations as well. Data growth projections must also be taken into account to find the most effective option.
Backup Solutions for Business Security
Enterprise backup solutions are the last line of defense against data breaches, cyber threats, and operational failures capable of crippling entire business operations. Modern-day backup solutions are expected to go far beyond simple data recovery, creating a comprehensive security framework capable of protecting against complex attacks while ensuring rapid restoration.
How Important is Data Security to Enterprise Backup Solutions?
The importance of data security in enterprise-level backup software has reached an all-time high, with cyber attacks becoming more complex and frequent than ever. With ransomware attacks affecting 72% of businesses worldwide (as of 2023) and threat actors specifically targeting backup infrastructure, organizations no longer have the option to treat backup security as an afterthought.
Modern backup solutions need proactive protection against cyber threats, while maintaining the integrity and availability of backup data. These measures are practically mandatory for a company that wants to ensure the viability of its recovery efforts, even when primary environments are compromised.
Security Features to Look For in Backup Software
Enterprise backup software must incorporate several layers of security features to protect against diverse threat vectors, ensuring the recoverability of critical data. Essential security features include:
- Backup immutability and WORM storage to prevent data tampering
- Comprehensive encryption for both at-rest and mid-transit data (AES-256, Blowfish)
- Air-gapped storage options to isolate backups from production networks either logically or physically
- Multi-factor authentication and role-based access control for administrative feature set
- Automated anomaly detection with AI-powered threat scanning capabilities
- Audit logging and monitoring with integration capabilities to SIEM systems for improved security oversight
- Zero-trust architecture principles across solution design and deployment practices
Advanced security capabilities must also cover real-time malware scanning, automated threat response workflows, and integration with enterprise-level security platforms to offer comprehensive data protection during the entire backup lifecycle.
Tips for Improving Security Positioning in Enterprise Backup Solutions
Organizations would significantly improve their backup security posture by using strategic implementation and operational best practices. Regular security testing must cover penetration testing for backup infrastructure, verification of air-gap effectiveness, and recovery procedure validation under simulated attack conditions. Using the aforementioned 3-2-2 backup role with at least one immutable copy helps ensure information availability even during the most dire security incidents.
Operational security enhancements involve:
- Establishing separate administrative credentials for backup systems
- Implementing time-delayed deletion policies to avoid immediate data destruction
- Maintaining offline recovery media for the most critical systems
Additionally, it is important for backup administrators to receive specialized security training with a focus on recognizing social engineering attempts and following incident response procedures. Regular verification of backup integrity and automated compliance reporting are both instrumental for maintaining security standards while creating audit trails for potential regulatory requirements.
2025 objectives and challenges of enterprise backup solutions
In 2025, the importance of data security is at an all-time high, with geopolitical conflicts backed by cyberattacks on a regular basis. Ongoing hacking campaigns, for example, gain more momentum as time goes on, and the number of cyber incidents continues to grow in strength and complexity.
In this context, no security feature is considered excessive, and some of the most sophisticated options have become far more common and widely used than ever. For example, air gapping as a concept works well against most forms of ransomware, due to the ability to physically disconnect one or several backups from the outside world.
A very similar logic applies to backup immutability, the ability to create data that cannot be modified in any way once it has been written the first time. WORM storage works well to provide backup immutability, and many enterprise backup solutions also offer such capabilities in one way or another.
Data security and resilience remain top priorities for enterprises in 2025, driven by evolving threats, fast technological advancements, and the rapid surge in the number of regulatory demands. Although many challenges from previous years persist, there is also a selection of newer trends that have emerged to reshape the objectives for backup strategies in large businesses and enterprises. Here are some of the most recent issues that enterprise-grade backup software must address:
Ransomware Resilience
Improved ransomware resilience, due to the fact that ransomware attacks keep growing in scale and complexity. Features such as air-gapped storage, backup immutability, and advanced recovery orchestration have become the norm for many organizations, despite being nothing more than helpful suggestions just a few years ago. There is also a growing emphasis on AI-assisted anomaly detection to identify threats in real-time for better responses to each issue.
AI and ML Integration
Expanded integration of AI and ML have already transformed backup operations to a certain degree. Now, these technologies optimize backup schedules, predict system failures, and improve data deduplication capabilities of the environment. Additionally, AI-driven insights also help companies to streamline resource allocation, reduce operational overhead, and prioritize critical data when necessary.
Hybrid and Multi-Cloud Environments
Ongoing adaptation to both hybrid and multi-cloud environments requires backup software that is much more complex and versatile at the same time. There is greater demand for cloud-agnostic solutions with centralized management, data encryption, and information portability as primary features.
Continuous Data Protection
Increased emphasis on Continuous Data Protection instead of traditional backup windows has been forced by the need to maintain near-real-time data protection while also reducing RTOs and ensuring business continuity. Both of these requirements have made traditional backup windows much less relevant than ever before.
Regulatory Compliance Requirements
Continuous evolution of regulatory compliance requirements has resulted in many new data protection laws and updates to existing frameworks. 2025 is guaranteed to both continue the demand to support all kinds of existing regulations and to facilitate the introduction of newer regulations that revolve around AI-related governance. Notable examples include:
- EU AI Act Implementation that bans AI systems posing unacceptable risks, introduced with a phased implementation starting from 1 August 2024 and which will go into full effect 2 August 2026
- Trump Administration AI Executive Order, cited as “Removing Barriers to American Leadership in Artificial Intelligence”, focused on revoking directives perceived as restrictive to AI innovation with the intent of improving the “unbiased and agenda-free” development of AI systems
- Colorado Artificial Intelligence Act that adopts a risk-based approach similar to EU AI Act for employment decisions
Containerized and Microservice Architectures
Improved support for containerized and microservice architectures is already extremely common, and it is expected to become the de-facto baseline in 2025, with support for Kubernetes, Docker, and microservices becoming more and more common. Enterprises now need backup solutions that manage both multi-cluster environments, and hybrid deployments, while providing advanced recovery options with containerized workflows in mind.
Sustainability and Green Initiatives
Sustainability and green initiatives are expected to continue their relevance, as environmental sustainability is now a strategic objective for almost all companies. The prioritization of energy-efficient data centers and optimized storage usage with eco-friendly hardware in existing backup infrastructures continues to offer support for broader ESG goals as time goes on. Regarding the sustainability of the product development itself, open source-based solutions such as Bacula tend to score far higher than proprietary solutions due to the efficiency of software testing and development by their communities.
Cost and Value Optimization
Cost and value optimizations now go hand in hand, with cost controls retaining their importance and value optimization coming into focus, both now and during all of 2025. All businesses must now try to balance security, scalability, resilience, and cost-efficiency in the same environment with flexible licensing, advanced deduplication, and intelligent tiered storage as potential solutions.
A good example of such a solution is Bacula Enterprise, with its unique subscription-based licensing model breaking from industry norms by charging based on the total number of backup agents instead of data volume. It offers its customers cost predictability and budget control, allowing them to scale their data storage without the massive escalations in licensing costs that are commonly associated with the capacity-based pricing models of most backup vendors on the market.
Data Sovereignty Concerns
The increase in concerns around data sovereignty has put greater emphasis on navigating cross-border data transfer regulations in 2025. Backup solutions now must support localized storage options with robust data residency controls and complete compliance with relevant international standards.
There are multiple examples of government-specific cloud solutions that are located in a specific country and meet the privacy, sovereignty, governance, and transparency requirements of that country:
Conclusion
The enterprise backup solution market is vast and highly competitive, which is both a positive and a negative factor for all customers.
The positive factor is that competition is at an all-time high and companies strive to implement new features and improve existing ones to stay ahead of their competitors, offering their customers an experience that is constantly evolving and improving.
The negative factor, on the other hand, is that the wealth of options may make it difficult for any company to choose one single solution. There are so many different factors that go into choosing an enterprise backup solution that the process itself becomes extremely difficult.
This article has presented a long list of different enterprise backup solutions, their unique features, their positive and negative sides, their user reviews, etc. Any enterprise-grade backup solution is a sophisticated combination of features and frameworks with the goal of providing a multitude of advantages to end users in the form of large-scale enterprises.
Recommended Enterprise Backup Solutions
Any enterprise-level backup solution consists of many different elements, including flexibility, mobility, security, feature variety, and many others. Choosing the appropriate backup solution for a specific company is a long and arduous process that is made slightly less complicated by using the sequence of different steps presented in this article. As for specific solution recommendations, our list included a variety of interesting enterprise backup software examples for all kinds of clientele.
Commvault is a viable option for a large enterprise that is not shy about spending extra to receive one of the best feature sets on the market. Acronis Cyber Backup is a great choice for larger companies that must deal with much sensitive data, as it offers one of the most sophisticated data security feature sets on the market. Veeam is another highly regarded player in the enterprise backup and disaster recovery market, known for its robust solutions that cater to a wide range of environments, including premium capabilities in virtual environments.
Alternatively, there are also backup solutions such as Bacula Enterprise that offer especially high security, flexibility and scalability. Bacula Enterprise delivers coverage to companies with many different storage types in place, from physical drives to virtual machines, databases, containers and clusters, with up to 10,000 endpoints covered at the same time.
Bacula works with both enterprise-grade commercial infrastructures and government entities. The Warner Bros. Discovery conglomerate uses Bacula Enterprise for its live media broadcast environment, reporting exceptional results with a reasonable price tag and impressive customer support.
One of the most unconventional examples of Bacula Enterprise’s versatility is NASA’s choice of Bacula’s solution. The next quote belongs to Gustaf J. Barkstrom, Systems Administrator at SSAI, NASA Langley contractor.
«Of those evaluated, Bacula Enterprise was the only product that worked with HPSS out -of-the-box without vendor development, provided multi-user access, had encryption compliant with Federal Information Processing Standards, did not have a capacity-based licensing model, and was available within budget»
All in all, choosing the specific solution for any company is no easy task, and we hope that this article will be helpful in providing as much information as possible about a number of different offerings.
Key Takeaways
- Enterprise backup solutions require comprehensive evaluations of data protection capabilities, disaster recovery support, storage compatibility, and retention options to meet complex organizational requirements
- Security features are paramount, with ransomware affecting more than 72% of businesses worldwide, which makes backup immutability, encryption, and air-gapped storage essential for proper security
- Deployment model selection between on-premise, cloud, and hybrid solutions should be decided based on data volume, performance requirements, and regulatory compliance needs
- The 3-2-2- backup rule offers enhanced protection by maintaining three data copies on two different media types at two separate geographic locations
- Systematic vendor evaluation using Gartner’s Magic Quadrant, proof-of-concept testing, and TCO analysis ensures organizations select solutions that are aligned with their individual requirements
Why you can trust us
Bacula Systems is all about accuracy and consistency and our materials always try to provide the most objective points of view of different technologies, products, and companies. Our reviews use many different methods, such as product info and expert insights, to generate the most informative content possible.
Our materials report all types of factors about every single solution presented, be it feature sets, pricing, customer reviews, etc. Bacula’s product strategy is overlooked and controlled by Jorge Gea, the CTO of Bacula Systems, and Rob Morrison, the CMO of Bacula Systems.
Before joining Bacula Systems, Jorge was for many years the CTO of Whitebearsolutions SL, where he led the Backup and Storage area and the WBSAirback solution. Jorge now provides leadership and guidance in current technological trends, technical skills, processes, methodologies and tools for the rapid and exciting development of Bacula products. Responsible for the product roadmap, Jorge is actively involved in the architecture, engineering and development process of Bacula components. Jorge holds a Bachelor degree in computer science engineering from the University of Alicante, a Doctorate in computation technologies and a Master Degree in network administration.
Rob started his IT marketing career with Silicon Graphics in Switzerland, performing strongly in various marketing management roles for almost 10 years. In the next 10 years, Rob also held various marketing management positions in JBoss, Red Hat, and Pentaho, ensuring market share growth for these well-known companies. He is a graduate of Plymouth University and holds an Honours degree in Digital Media and Communications.
Frequently Asked Questions
What are the biggest differences between enterprise-grade and consumer-grade backup tools?
Enterprise backup solutions are designed primarily with large-scale environments in mind, providing advanced features like encryption, deduplication, support for hybrid infrastructures, and more. Consumer-grade tools, on the other hand, use primarily basic file backup and recovery methods without most of the substantial features in automation, security, and scalability that most enterprise tools have.
How can immutability assist with protecting against ransomware attacks?
Backup immutability exists to make sure that, once information has been written, it cannot be altered for a specific retention period. This approach is often referred to as WORM – Write Once Read Many – and it offers substantial security against most ransomware attacks, preventing them from encrypting or otherwise modifying existing immutable data.
What explains air-gapped storage’s apparent importance in enterprise data security?
Air-gapped storage uses physical or logical isolation of backup data from the rest of the environment to prevent any direct access to it from external sources, including cyber-attacks and ransomware. This physical isolation ensures the safety of backup data, even when the primary systems of the environment have been compromised.
What is a Solaris Backup and Why is it Important?
Solaris backup is the process of creating copies of information, system configurations, and application states in Oracle’s Solaris operating system environment. Backups are critical to secure information against data loss, system failures, and security breaches. Backups also contribute positively to business continuity efforts for enterprise operations running Solaris platforms.
The Importance of Data Backup in Solaris Environments
Solaris systems power mission-critical enterprise applications where downtime is unacceptable. Data backup is a primary defense against several potential issues:
- Hardware failures capable of corrupting entire file systems at the same time.
- Human errors during system administration leading to the deletion of critical files.
- Security incidents like ransomware attacks that specifically target enterprise Unix environments.
Solaris environments often manage terabytes of business information across different zones and applications. Without proper backup systems in place, businesses risk losing substantial data, as well as violating requirements of regulatory compliance, extended downtime affecting customers, and even permanent loss of business records or intellectual property.
Enterprise-grade backup strategies help shorten recovery time from days to hours, ensuring that Solaris infrastructure meets the 99.9% uptime expectations that many modern business operations require.
How to Back Up a Solaris System with Zones Installed
Solaris zones create isolated virtual environments within the same Solaris instance, requiring special backup approaches capable of accounting for both global and non-global zone information.
- Global zone backups capture the state of the entire system at once, including kernel settings, zone configurations, and shared resources. The zonecfg command is commonly used to export zone configurations before initiating a full system backup.
- Zone-specific backups target only individual zone data. The zoneadm command halts specific zones during backup tasks, ensuring the consistency of data in the next backup.
Live zone backups are also possible in Solaris, using its snapshot technology to capture information from running zones without service interruptions. This method helps maintain business continuity while creating a reliable recovery point for specific active applications.
All backup schedules within Solaris environments must be configured with zone dependencies and shared storage resources in mind. Zones that share the same file system also require some coordination of their backup processes to avoid data corruption during the backup sequence.
Differences Between Global and Non-Global Zone Backups
Global zones comprise the entire Solaris installation, including the kernel itself, system libraries, and zone management infrastructure. Global zone backups generate a full system image that can be used during complete disaster recovery processes.
Non-global zones work as isolated containers with only limited access to the system information. These backups have a stronger focus on application data, user files, and zone-specific configurations, than on copying system-level components.
Backup scope differs significantly from one zone type to another:
- Global zones must back up device drivers, network configurations, and security policies
- Non-global zones only mustcopy application binaries, data files, and zone-centric settings
- Restoring a global zone affects the entire system, while rebuilding a non-global zone affects only specific applications.
Recovery procedures also vary, depending on the zone type. Global zone failures can be resolved only by using bare metal restoration and bootable media. Non-global zone issues are often resolved by zone recreation and data restoration, which does not affect any other system component in the environment.
Storage requirements for global zones are usually several times larger than for non-global zones, due to the massive difference in scope. It is important to keep this information in mind when planning Solaris backup architecture, especially in terms of backup storage capacity.
To explain simply how Solaris zones differ, we have created this visual representation of their differences:
| factor |
Global Zone |
Non-Global Zone |
| backup scope |
Entire system, including kernel and drivers |
Application data and zone-specific configurations |
| backup size |
Large, needs to cover full system state |
Smaller, focused on application-centric content |
| downtime impact |
Affects entire Solaris environment |
Often isolated only to specific services or applications |
| dependencies |
Contains zone management infrastructure |
Relies on global zone for system resources |
| restoration time |
Several hours in most cases |
Minutes to hours depending on the zone size |
| storage requirements |
High capacity to create a complete system image |
Moderate capacity for application data |
Using Backup Software in Solaris Systems
Modern Solaris zones require specialized backup software capable of understanding the context of zone architecture. Choosing the correct backup solution can dramatically reduce administrative overhead while also providing reliable data protection.
Choosing the Right Backup Software for Solaris
Zone-aware backup software is required in Solaris environments. To be used in Solaris infrastructure, specialized solutions must be able to detect and accommodate zones and to create both global and non-global zone backups.
Scalability is an important factor in enterprise deployments. A competent backup software for Solaris should be able to handle hundreds of zones across different physical systems, without performance degradation, to be considered acceptable.
Integration capabilities are just as important in this context, especially for solutions with existing infrastructure. Choosing solutions that support NDMP (Network Data Management Protocols) for direct storage communication and SNMP (Simple Network Management Protocol) monitoring for centralized management is highly recommended in most cases.
Any backup solution’s Licensing model is extremely important for a business of any size. Per-server licensing works best in smaller deployments, while capacity-based licensing may be a better option for larger environments with an extensive number of servers.
Other essential selection criteria include:
- Real-time zone detection with the ability to apply policies automatically
- Support for concurrent backup streams that function on multiple zones at the same time
- Centralized management capabilities are important in multi-server environments
- Disaster recovery integration should fit within the company’s current business continuity plans
Comparing Open Source and Commercial Solaris Backup Tools
There are many options for both open-source and commercial backup tools for Solaris. One such open-source example is Amanda – a community version of a backup solution that excels at network coordination and which works wonders in Solaris systems. It uses a client-server architecture that scales effectively but does require significant expertise in zone configuration.
Commercial solutions offer comprehensive support with dedicated technical teams, which distinguishes them from open-source options. Veritas NetBackup is one of many examples here: a reputable backup and recovery solution with an extensive feature set. One of its many capabilities is a native Solaris integration with automated zone detection and snapshot coordination capabilities. Support for Solaris in enterprise backup solutions is limited, making solutions like Veritas and Bacula (mentioned further below) unusual and attractive.
Large deployments prefer commercial tools because of their performance, among other factors. Open-source solutions also must be configured manually, which is a much less feasible option for bigger enterprises. Support models are the greatest difference by far here, with open-source solutions relying largely on community forums, while commercial vendors can offer guaranteed response time frames and detailed escalation guidelines.
As such, we can outline the primary comparison factors, beyond everything discussed in this section:
- Initial cost: Open-source options have no licensing hurdles but require a high level of experience with the software
- Scalability: Commercial solutions often have a much better ability to grow with the enterprise
- Feature updates: Commercial tools typically deploy new features and fix bugs more quickly
- Recovery capabilities: Some enterprise solutions provide bare metal restoration options
Our survey would not be complete without mentioning at least one hybrid option for backup tools. Bacula Enterprise is an exceptionally high security comprehensive backup and recovery platform that bridges the gap between open-source and commercial solutions, combining open-source core with commercial support, training, and comprehensive enterprise features. This unconventional approach, combined with a cost-effective subscription-based licensing model, makes Bacula a very attractive option for many large-scale environments, including ones using Solaris.
Bacula supports over 33 different operating-types, including various versions of Solaris. It also integrates natively with an especially broad range of virtual machine-types and different databases. It is storage-agnostic (including any kind of tape technology), and readily integrates into all mainstream Cloud interfaces. Its flexibility and customizability fits Solaris users well, and its choice of either command line interface and/or web based GUI means even more options for Solaris users.
Compatibility Considerations for Legacy Solaris Versions
Solaris 8 and 9 systems lack zone support. These versions require backup solutions capable of working with older kernel interfaces and legacy file systems. Solaris 10 compatibility tends to vary, depending on the software version. Newer backup releases may no longer support legacy zone implementations and older ZFS versions.
Migration strategies must therefore prioritize upgrading to supported versions first. In that way, long-term supportability can be ensured, along with access to modern backup features.
Hybrid environments that run multiple Solaris versions require a separate backup strategy for each version. Software compatibility is an impenetrable barrier between versions, preventing unified management.
Vendor support lifecycles also have a strong effect on impact options. It is highly recommended to research the end-of-life schedules for all backup software to avoid unexpected discontinuations.
Legacy system requirements often include hardware dependencies for older versions of Solaris. Application compatibility is critical during migration planning. Gradual update timelines can help prevent business disruptions when working with legacy Solaris versions. Some businesses will have no choice but to create separate backup architectures for older or unsupported versions of the infrastructure until they can find a more permanent solution.
What Are the Best Practices for Backing Up Solaris Zones?
Effective Solaris zone backup strategies require coordinated approaches capable of accounting for zone interdependencies and requirements to ensure business continuity. Using tried and proven backup practices helps ensure reliable data protection and minimize total system impact.
Creating a Backup Strategy for Solaris Zones
Zone classification is the foundation of any effective Solaris backup approach. Mission-critical production zones require full backups daily with hourly incremental captures. Development zones, on the other hand, may need only weekly-based backups in most cases.
Dependency mapping can reveal critical relationships between zones. Zones that share storage resources or network configurations must be backed up in a specific order to prevent data inconsistency during subsequent restoration procedures.
Recovery objectives also play a large role in determining the final backup strategy. RTOs (Recovery Time Objectives) define maximum acceptable downtime per zone, while RPOs (Recovery Point Objectives) form acceptable thresholds for data loss in business operations.
Other important elements of strategic planning for backups are:
- Storage allocation to ensure sufficient capacity for any retention requirements
- Documentation standards that help maintain current procedures and zone inventories
- Backup windows that are carefully scheduled around high-activity periods
- Performance impact of backup processes that minimizes disruption to production workloads
It must be noted that, to remain effective, a backup strategy cannot remain set in stone once it has been created. Regular strategy reviews ensure that backup practices can evolve with the business’s ever-changing needs. Any application changes or infrastructure growth events must be reflected in the backup strategy in some way.
Scheduling Regular Backups in Solaris
Scheduling automation of backup operations helps eliminate human error while offering consistent protection. Cron-based scheduling granular control over backup timing, coordinating it with application maintenance windows and other potentially sensitive time periods.
Cron is a job scheduler on Unix-like operating systems that is commonly used in many different situations, not only for Solaris backup jobs.
Backup frequency is a functon of zone importance and data change rates. In certain industries, database zones may require several backups per day to meet strict RPO requirements, while static content zones rarely need such strict protection measures.
Peak hour avoidance helps prevent backup operations from consuming resources during peak production workloads. It includes scheduling more resource-intensive operations during low-utilization periods (between midnight and 6 A.M. in most situations), while maintaining great system performance during business hours.
We must also mention the following in the context of Solaris backup scheduling:
- Staggered start times avoid simultaneous operations that can overwhelm storage systems.
- Resource monitoring workflows assist in keeping close watch over the consumption of CPU and memory backup processes.
- Failure retry mechanisms can automatically restart failed backup jobs without any human intervention.
- Monitoring integration is an extension of resource monitoring, with automatic alerts capable of notifying administrators about storage capacity issues or backup failures that need immediate human attention to resolve.
Resolving Permission and Resource Conflicts in Solaris Zone Backups
Permission conflicts appear when backup processes cannot access zone files because of security restrictions in the built-in framework. – Solaris Rights Management. Issues like these commonly appear after security policy changes or during initial backup configuration.
Resource contention is another type of conflict in which multiple zones need limited system resources for backup or other tasks. Unresolved resource conflicts cause performance degradation across the entire environment, and can even result in complete backup failures in more heavily-loaded environments.
File system locks, which occur when case applications with exclusive file handles prevent backup access are less common. These conflicts are easily avoided by coordinating backup timing with application shutdown procedures. They can even be circumvented entirely by using the Snapshot technology as an alternative, for consistent data capture without application interruption.
Common resolution techniques for many of these issues revolve around resource throttling that limits consumption of resources or privilege escalation for backup processes. Zone state management is also an option in certain situations; stopping non-essential zones during critical backup tasks to free up system resources (done using zoneadm halt command).
Proactive monitoring plays a large part in resolving these issues, identifying them before they become a problem for the entire company. Proactive monitoring enables a variety of preventive measures that can maintain the integrity of backup schedules across complex zone environments.
Automation and Scripting Techniques for Solaris Backups
Although specific examples of scripts are outside of this guide’s total scope of capabilities,we can review several recommendations for scripting and automation processes in the context of Solaris backups:
- Shell scripting is commonly used for scripting and automation, making automation capabilities flexible for zone-specific backup requirements.
- Custom-made scripts can easily handle pre-backup preparations, while also coordinating zone shutdowns and managing post-backup verification procedures.
Error handling measures in automated scripts ensure that any process failure will trigger all the necessary alerts or recovery actions. Built-in comprehensive logging assists in tracking backup success rates, while also identifying recurring issues that require administrative attention to resolve.
Partially modular scripts can be reused across different zone configurations, rather than starting from scratch every time. That reduces total development time and ensures that backup procedures remain consistent across the entire Solaris infrastructure.
As for automation efforts specifically, there are several best practices to follow in most cases:
- Performance optimization to adjust backup intensity based on current system load.
- Configuration file management to create a centralized parameter storage and simplify maintenance
- Version control to track deployments and script changes
- Rollback procedures capable of reversing failed operations automatically
Integration capabilities facilitate the interaction of backup scripts with storage management tools and enterprise monitoring systems, creating streamlined operations that significantly reduce manual administrative overhead and improve total reliability.
How to Restore Data from a Solaris Backup?
Successful data restoration in Solaris requires knowledge of both zone architecture and various backup methodologies . Adherence to proper restoration procedures minimizes downtime while also maintaining data integrity in both global and non-global zone environments.
Restoring Data in the Global Zone
Global zone restoration affects the entire Solaris environment, from regular data storage to kernel components and zone management infrastructure. Full system restoration must be initiated from backup media, because it completely rebuilds the server environment.
A bare metal recovery process uses a bootable backup media that contains the full image of a global zone. It restores device drivers, security policies, and network configurations to the exact state they were in during the backup process. The procedure requires several hours in most cases, depending on storage performance and the total data volume to be recovered.When there is no need to rebuild the entire environment, selective restoration is an option. . Selective restoration is ideal for resolving configuration file corruption or accidental system directory deletion, preserving existing zone configurations in the process.
Zone configuration restoration is a self-explanatory process that is also used to recreate container environments. The command used here is zonecfg; it imports previously saved zone configuration data to ensure architectural consistency of zones after a global zone recovery process.
Recovery verification is used after most recovery events to test zone boot capabilities and ensure network connectivity across any restored zones. System validation is also used regularly alongside it, ensuring that all services have been initiated correctly without disrupting zone isolation rules.
Recovering Application and User Information in Non-Global Zones
Non-global zone recovery differs from recovery of global zones, with a focus on recovering application data and user files without interfering with global system components. It is a much more targeted approach that minimizes restoration times and reduces the impact of recovery on other zones within the same physical system.
Zone halting must occur before any attempts at non-global data restoration, to ensure file system consistency. The command in question is zoneadm halt: it shuts down the target zone before restoration procedures can be initiated, preventing data corruption during recovery.
Application-specific restoration processes require knowledge of data dependencies and startup sequences to conduct correctly. For example, web applications often require configuration file restoration and content synchronization, while database applications require recovery of the transaction log.
User data recovery is another field with its own rules to follow to restore home directories, application settings, and custom configurations. File ownership verification is a useful action to take to ensure that restored information maintains proper permission combinations for zone-specific applications or users.
Restoration priorities for non-global zone data look like this in most cases:
- Critical application data is restored as soon as possible to reduce business impact.
- Configuration files also have a certain degree of priority, ensuring applications can initiate with correct settings.
- User environments with profiles and custom configurations are restored next.
- Temporary data is reserved for the very last spot on the list, as it is non-critical in most cases.
Testing procedures are commonly mentioned along with restoration of user and application data, verifying that applications are functional before attempting to return zones to production service. Connectivity testing and performance validation are good examples of processes that are part of these procedures.
Using Snapshots for Quick Restore in Solaris
ZFS snapshots are a great way to create instant recovery points for quick data restoration, without relying on traditional backup media. Snapshots can capture point-in-time consistency, while using significantly less storage than a full backup, by taking advantage of copy-on-write technology.
Snapshots are generated instantly and do not interrupt running applications. The dedicated command for this action is zfs snapshot: it creates named recovery points that remain accessible until deleted by hand. Solaris environments commonly organize regular snapshot scheduling, for granular recovery capabilities throughout the work day.
Rollback procedures can restore file systems to one of the snapshot states in the matter of minutes. This approach works well for configuration errors or accidental data deletion, where only the most recent changes must be reversed. That said, rollbacks affect all data created after the generation of the snapshot, which requires planning and calculation.
Snapshots can also be converted into writable copies with clone operations, used primarily for testing and development purposes. Snapshot clones allow administrators to verify restoration procedures, with no effect on production data or the total consumption of storage resources.At the same time, snapshots are far from a perfect tool. They have their own limitations, including being highly dependent on the health of the underlying storage, as well as finite retention periods imposed by the constraints of total storage capacity. As such, snapshot retention policies must be planned with available storage and recovery requirements in mind.
Handling Partial and Corrupted Backup Restores
Backup verification is the primary process used to identify corruption before information can be restored. Test restorations and checksum validations are the most common methods of backup verification, preventing corrupted information from entering production environments. The integrity of the backup should always be verified before any restoration procedure, especially in mission-critical environments.
Partial restoration is useful for recovering usable data segments when complete backups have become partially corrupted. File-level recovery can extract individual files from damaged backup sets, avoiding corrupted areas that can render the system unstable.
Alternative backup sources are one way to have recovery options immediately available if primary backups fail verification. Using different backup retention periods can also ensure that older and verified backups will remain available for potential emergency restoration scenarios.
Incremental reconstruction is also a viable option in certain situations, combining multiple backup sources to create complete restoration sets. However, it works only when all differential backups are still intact and have not been corrupted in any way.
Noteworthy corruption recovery strategies in Solaris environments include:
- Media replacement to resolve physical storage device failures;
- Alternative restoration locations for recovery process testing before deploying them to production; and
- Network retransmission for corrupted remote backups.
- Professional recovery services are always an option, but are often used only for the most catastrophic backup failures
Documentation requirements are of particular importance in this context, acting as both detailed logs of restoration attempts and the history of lessons learned for future incident response. This information helps improve backup strategies while preventing similar failures from occurring.
What Should Administrators Know About Solaris Backup and Recovery?
Solaris administrators require mastery of backup commands, monitoring procedures, and testing protocols to ensure the reliability of data protection measures. Administrative expertise directly influences backup success rates and recovery capabilities in critical incidents.
Critical Commands for Solaris Backup Administration
Essential backup commands, such as ufsdump, are the foundation of Solaris administration skills. This specific command creates file system backups for UNIX File Systems (UFS) environments. Another important command, zfs send, is used to handle ZFS dataset transfers with stream-based efficiency.
Zone management commands control backup timing and system state.
- zoneadm list -cv displays the status of a current zone, which is important to know before conducting a backup operation
- zoneadm halt shuts down zones to provide consistent data for later backups
Tape device commands, such as mt control status verification and positioning of the backup media. Alternatively, tar and cpio create backups in portable formats that are compatible across a wide range of different Unix systems, making them suitable for a wide range of restoration scenarios.
Verification commands check the integrity of the backup after the process has been completed. ufsrestore -t lists backup contents without extracting them, and zfs receive -n conducts dry-run testing of ZFS stream restoration procedures.
Command mastery also includes the understanding of various device specifications and backup media management. The usage of /dev/rmt/ device naming conventions, as an example, helps control tape driver behavior using density and rewind settings.
The Role of the Administrator in Backup Processes
Administrator responsibilities extend beyond executing backup commands, to cover strategy development and failure response coordination, as well. Modern backup operations require both technical skills to perform these tasks and sufficient business understanding to be aware of their potential implications.
Backup planning consists of analyzing system performance, storage requirements, and business continuity needs. Administrators must balance backup frequency with system resource consumption, while also meeting the necessary recovery objectives.
An administrator’s monitoring duties include tracking different parameters, such as backup job completion, storage capacity utilization, and error pattern identification. Proactive monitoring efforts assist in preventing backup failures, while also ensuring consistent data protection across all systems.
Documentation maintenance requires maintaining all current system inventories, backup procedures, and the results of recovery testing. This information is critical in emergency restoration scenarios, by detailing procedures that were more successful in preventing highly expensive mistakes.
Other potential areas of backup and recovery administration worth mentioning include:
- Resource allocation to ensure CPU and storage capacity are adequate for backup processes
- Schedule coordination is necessary to prevent conflicts between backup jobs and other processes, like maintenance windows
- Security compliance maintains backup encryption and access controls measures in working order
- Vendor relationship management requires coordination among backup software support teams
Cross-training initiatives are common in large and complex environments, ensuring that backup knowledge does not rely on a single administrator in the entire system. Knowledge transfer as a process helps prevent operational disruptions during emergency situations or staff changes.
Testing Backup Restore Processes
Regular restoration testing assists with validating backup procedures, identifying potential recovery issues in the process. Monthly test schedules provide some confidence in the reliability of backups, without spending excessive resource volumes solely on testing.
Setting up test environments is also the responsibility of the administrator, which requires isolating systems that would affect production operations if something went wrong. Luckily, virtual machines are an effective testing platform for backup restoration validation and procedure verification, while also remaining surprisingly cost-effective.
Partial restoration tests can verify specific backup components, rather than test or recover the entire system. Individual zone restorations, database recovery procedures, and application-specific restoration requirements must be tested separately.
Test result documentation tracks restoration success rates while identifying opportunities for improvement. Important performance metrics here include data integrity verification, restoration time, and application functionality confirmation.
Failure scenario testing helps prepare administrators for resolving various types of disasters. Comprehensive preparation measures must be used to perform test restorations from corrupted backup media, partial backup sets, and alternative recovery locations, at the very least.
Zone recreation from backup configurations, bare metal recovery procedures, and cross-platform restoration capabilities (where applicable) must be tested for the best coverage.
Monitoring and Logging Solaris Backup Jobs Effectively
Centralized logging aggregates backup job information from multiple Solaris systems into much more manageable dashboards. Log analysis identifies trends, performance issues, and recurring failure patterns that may need administrative attention.
Real-time monitoring can be paired with custom alerts to notify administrators about backup failures, storage capacity issues, and performance degradation during operation. Alerting automation ensures prompt responses to critical backup issues.
Performance metrics of backup and recovery include:
- Backup duration
- Throughput rates
- Resource utilization patterns, and more.
This information helps optimize backup scheduling, while also identifying systems that need hardware upgrades or certain adjustments to their configuration.
Retention policies must be monitored to ensure that backup storage does not exceed capacity limits and is till contributing to creating necessary recovery points. Cleanup processes can also be automated, removing expired backups according to an established retention schedule.
Best practices for monitoring processes include the following:
- Capacity planning based on trends in the growth of storage Threshold-based alerting for backup durations that exceed normal ranges
- Integration with enterprise monitoring systems to unify operations management
Historical reporting must not be forgotten in this context, as well. It can offer insights into the reliability of backup systems in the long-term, helping justify investments in infrastructure improvements to improve data protection capabilities.
What Are the Storage Options for Solaris Backup?
The performance, capacity, and reliability requirements for any Solaris backup storage must be carefully evaluated. Strategic storage decisions can significantly impact backup speed, recovery capabilities, and even long-term data protection costs for the entire company.
Choosing Between Tape and Disk Storage for Backups
The choice between tape and disk storage for backups ultimately depends on the purpose of the backups:
- Tape storage offers cost-effective long-term retention with high reliability for archival purposes. Modern LTO tape technology provides extremely convenient compression capabilities with over 30 TB of data per cartridge, maintaining data integrity for decades.
- Disk storage results in faster backup and recovery processes, with spinning disk arrays offering immediate data availability while solid-state drives are extremely fast, making them superior for the most critical business applications.
Hybrid approaches are also possible, combining both technologies in a strategic manner. Hybrid approaches can create disk-to-disk-to-tape architectures that use fast disk storage for the more recent backups, while older data is migrated to tape as its cost-effective long-term storage option.
Performance characteristics vary significantly between storage types. Tape systems are great for sequential data streaming but struggle with random access patterns. Disk storage easily handles concurrent access but is much more expensive in terms of cost-per-terabyte.
Reliability considerations often favor tape systems for potential disaster recovery scenarios, because tapes remain functional without network connectivity or power. Disk systems offer greater availability than tape, but require a consistent power source and a controlled storage environment.
Scalability and power consumption are also important factors to consider in this comparison. Scalability favors tape due to its ability to scale to petabyte capacities with ease. Power consumption also favors tape over disk, due to itslow energy requirements during storage.
Utilizing Loopback Files for Backup Storage
As a continuation of the previous comparison, consider loopback file systems: virtual tape devices that use disk storage to simulate the behavior of tape, offering the compatibility of tape with the performance characteristics of disks.
Configuration simplicity is one of many reasons why loopback files are considered attractive for development environments and smaller installations. The lofiadm command is used to create loopback devices that backup solutions can treat as physical tape drives.
Performance benefits of such an option include concurrent access capabilities and elimination of tape positioning delays. In that way, backups can be completed more quickly, while offering immediate verification of backup integrity.
Storage efficiency of loopback files allows thin provisioning, in which loopbacks are consuming space only for actual backup data, rather than the entire tape library. It is a stark contrast to pre-allocated tape cartridges that reserve their entire capacity, regardless of the volume of data written onto them.
This method also has its own limitations, including dependency on underlying disk system reliability, as well as higher per-terabyte cost compared to physical tape. Power requirements are the same as for disk systems, which is more than what tape drives consume.
Integration considerations help ensure backup software will recognize loopback devices properly, applying appropriate retention policies for virtual tape management.
Evaluating Reliable Storage Solutions for Solaris Backups
Enterprise storage reliability requires redundant components and fault-tolerant designs to prevent single points of failure. RAID configurations are one of many ways to protect information against individual disk failures, while maintaining the continuity of backup operations.
Storage system selection must take into account sustained throughput requirements and concurrent backup streams. High-performance storage is more expensive, but helps ensure backup operations are completed within designated windows without impacting production systems.
Vendor support quality is an important consideration, directly affecting incident response and hardware replacement procedures. Enterprise-grade support must include technical assistance 24/7 and guaranteed response times during critical storage failures.
Scalability planning helps ensure that storage systems will accommodate growth without the need to replace entire infrastructures. Modular expansion options create opportunities for future capacity increases without affecting current performance characteristics.
Reliability evaluation criteria are a combination of:
- Field failure statistics from existing deployments in similar environments
- Warranty coverage duration
- MTBF – Mean Time Between Failures – ratings
Data integrity features, such as end-to-end checksums and silent corruption detection, prevent backup data degradation over time while offering highly accurate restoration processes.
Using Network-Attached Storage and SAN with Solaris
Network-Attached Storage (NAS) in Solaris creates centralized backup repositories accessible from different systems simultaneously. NFS-based NAS can be seamlessly integrated with existing Solaris file system architectures.
The advantages of NAS environments include:
- Simplified management and file-level sharing;
- Protocol compatibility; and
- Cross-platform access with consistent security policies.
Storage Area Networks (SAN) provide block-level access with high-performance connectivity using iSCSI protocols or Fibre Channel. SAN environments form dedicated storage networks that do not compete with production traffic, creating many interesting opportunities.
Its primary benefits are as follows:
- Raw performance of network environments;
- Vast storage consolidation capabilities; and
- Centralized storage management for enterprise-grade reliability.
Network considerations for such environments include the need for adequate bandwidth for backup data transfer without affecting production applications. Existing Quality-of-Service (QoS) controls help ensure that backup traffic does not overwhelm the entire network infrastructure.
Security requirements of both options include access controls, data encryption, network isolation, and dedicated authentication mechanisms that prevent unauthorized access to backup repositories.
Network storage implementation is a challenging process that requires careful performance tuning and monitoring integration, ensuring that backup objectives will be met consistently across the enterprise environment.
Additionally, we offer a concise comparison table that highlights some of the most notable features of both SAN and NAS.
| Factor |
Network-Attached Storage – NAS |
Storage Area Network – SAN |
| Access Method |
File-level through NFS protocols |
Block-level using FC/iSCSI |
| Solaris integration |
Native NFS client support |
Multipathing configuration is required to proceed |
| Performance |
Can be limited by network bandwidth |
Operates as a dedicated high-speed storage network |
| Scalability |
Moderate, shared network resources |
High, a dedicated storage infrastructure |
| Cost |
Modest initial investment |
Reasonably high investments because of specialized hardware |
| Management |
File-level permissions and sharing |
Block-level storage allocation |
Key Takeaways
- In Solaris environments, ensure the backup software is zone-aware: any solution must understand container architecture and be able to back up both global and non-global zones.
- Automated scheduling with staggered timing assists in eliminating human error from the backup and recovery sequences.
- ZFS snapshots create instant recovery points with point-in-time consistency and minimal storage consumption.
- Regular restoration testing validates backup reliability on a regular basis.
- Hybrid storage approaches can greatly optimize cost and performance in the environment.
- Administrator expertise has a direct impact on backup success.
- Network storage solutions excel in centralized management tasks for both NAS and SAN
Frequently Asked Questions
What native backup tools are included with Solaris by default?
Solaris has a small selection of built-in backup utilities to choose from:
- ufsdump for UFS file systems
- tar and cpio for portable archives
- zfs send for ZFS data transfers
All three are native tools, offering basic backup functionality without additional software installation – but they do lack many advanced features, such as automated scheduling and centralized backup management.
How do I back up to an NFS-mounted directory with Solaris?
NFS-mounted backup directories enable centralized storage by mounting remote file systems using a dedicated command, mount -F nfs, and directing backup output to these network locations. That said, this method requires that NFS exports be properly configured on the storage server, along with adequate network bandwidth to handle backup data transfer.
Is it possible to encrypt Solaris backups natively or with third-party tools?
Both options are viable. Solaris provides native encryption using ZFS encrypted datasets and can also pipe backup streams through encryption utilities like openssl or gpg for improved security. Third-party backups also have built-in encryption options in most cases, with key management capabilities offering enterprise-grade security for sensitive backup information, both at rest and mid-transfer.
How Does Commvault Handle Data Encryption?
Commvault uses AES-256 and AES-128 encryption across backup, archive, and cloud storage tasks, offering enterprise-grade cryptographic protection for data throughout its lifecycle. Commvault’s backup encryption capabilities operate on multiple levels, protecting information both at rest in storage depositories and in transit between components.
AES Encryption Standards in Commvault
Commvault supports industry-standard Advanced Encryption Standard encryption with 128-bit and 256-bit key lengths, which enables organizations to balance performance requirements and security needs. AES-256 offers maximum cryptographic strength and is recommended for all highly-sensitive content, while AES-128 is an option in high-volume backup operations, with optimal performance and security capabilities.
The platform’s hardware acceleration support leverages modern processor encryption instructions (AES-NI for Advanced Encryption Standard – New Instructions) for minimal impact on performance. The total reduction of throughput rarely exceeds 10% with encryption enabled, making cryptographic protection nearly invisible during backup operations.
Multi-Layer Security Architecture
Encryption is the foundational security control in Commvault’s multi-layered security. Access controls and authentication help secure system perimeters in their own way, but without proper decryption keys, encryption renders backup data unreadable, even if storage systems themselves are physically compromised.
Commvault’s key security mechanisms include:
- Data obfuscation, which neutralizes stolen backup files
- Compliance automation to align with regulations requiring encrypted data storage
- Cloud security improvement in scenarios with limited physical control
- Persistent protection capable of continuing, even when other security controls have failed
Backup vs Archive vs Cloud Encryption Implementation
Backup encryption prioritizes rapid recovery capabilities using symmetric AES encryption, for optimal performance during restoration tasks. Backup jobs use AES-256 most of the time, for maximum security with limited impact on Recovery Time Objectives.
Archive encryption emphasizes long-term data integrity during extended retention periods. Archive encryption keys demand specialized lifecycle management to ensure accessibility for years or decades, while also maintaining suitable security throughout the entire retention period.
Cloud storage encryption uses dual-layer protection, with data encrypted on the client-side before transmission and cloud-provider encryption at the destination. This approach forms multiple security barriers against unauthorized access, while also maintaining compatibility with many useful cloud storage deduplication features.
Understanding Commvault’s Data-at-Rest Encryption
Commvault’s data-at-rest encryption secures backup files stored on disk drives, tape libraries, and cloud storage, using AES-256 encryption applied before data reaches its storage destination. This encryption works transparently within backup workflows and ensures that stored data remains unreadable without specific decryption keys.
Storage-Level Encryption Implementation
Data-at-rest encryption addresses the critical security gap created when backup files remain dormant in storage repositories. Physical storage theft, compromised cloud accounts, or unauthorized datacenter access cannot expose any readable data if all information is properly encrypted beforehand.
Regulatory compliance requirements mandate data-at-rest encryption for specific industries:
- HIPAA: Healthcare organizations are required to encrypt patient data in backup storage.
- CI DSS: Financial institutions require encrypted cardholder data storage.
- SOX: Public companies must encrypt financial records.
- GDPR: EU data protection requires encryption for backups of personal data.
Transparent Encryption Configuration Process in Commvault
Commvault implements transparent encryption (automatic encryption operations in the background) during backup operations, without requiring separate encryption steps or additional storage processing. The encryption process itself proceeds at the MediaAgent level before data is written to storage, ensuring that all backup data is cryptographically protected.
Commvault’s key hierarchy system protects individual file encryption keys using master key encryption. Multiple security layers prevent single-point encryption failures. Storage administrator isolation creates clear separation between storage management and data access privileges, ensuring that personnel with storage repository access do not have read access to backup data content.
Configuration Steps for Encrypted Storage Policies
A CommCell environment is a logical grouping of software elements that secure, move, store, and manage information in Commvault. Here is how to enable encryption using CommCell Concell:
- Navigate to Storage Policy Properties > Security Tab
- Select “Enable Encryption” checkbox
- Choose AES-256 for maximum security, or AES-128 for better performance
- Configure automatic key generation or specify custom encryption keys
- Apply encryption settings to new backup jobs as soon as possible
Granular encryption control allows different data types to be encrypted differently:
- Critical data: AES-256 encryption and extended key retention
- Standard backups: AES-128 encryption for performance balance
- Archive data: AES-256 with dedicated long-term key management
Performance and Compliance Advantages
Optimized encryption algorithms and hardware acceleration mean minimal impact on performance, because:
- Modern processors with AES-NI instructions reduce encryption overhead.
- Hardware acceleration combats encryption bottlenecks in backup windows.
- Transparent processing maintains identical backup and restore performance.
Automated encryption policies simplify compliance auditing. All stored data is automatically encrypted without manual input. Policy documentation provides audit-ready evidence of compliance. Restore operations function identically, whether information is encrypted or not.
Recovery operation compatibility ensures restoration of encrypted backups without additional complexity, eliminating operational overhead in critical recovery scenarios.
How Does Key Management Work in Commvault?
Commvault’s key management system works as the centralized control mechanism for generating encryption keys, as well as managing distribution, storage, and life cycles across enterprise backup environments. The system orchestrates all cryptographic operations while maintaining security separation between encryption keys and protected information.
Hierarchical Key Architecture in Commvault
Commvault implements multi-tier key hierarchy, using master keys to protect individual data encryption keys, and preventing single-point encryption failures by creating multiple security checkpoints.
- Master keys: Secure individual file encryption keys and control access to encrypted backup sets.
- Data encryption keys: Encrypt actual backup content at the file level.
- Session keys: Temporary keys for secure communication between different components of Commvault.
- Archive keys: Long-term keys for extended data retention with dedicated lifecycle management.
This layered security approach prevents individual file keys that have been compromised from exposing entire backup repositories, while master key security helps maintain overall data protection integrity.

Automated Key Generation Process
Cryptographically secure random number generators produce unpredictable encryption keys using multiple entropy sources, including hardware-based randomness when available. System-generated keys eliminate human involvement, which can introduce predictable patterns or security weaknesses.
Key strength configurations:
- Standard encryption: Balanced security and performance for routine backup operations.
- Maximum encryption: Enhanced security for sensitive data and compliance requirements.
- Automatic encryption: Eliminates the possibility of manual key creation errors while ensuring the cryptographic strength.
Key generation is automatic during encryption policy creation, with no administrative intervention, while maintaining enterprise-grade security standards.
RSA Key Pairs for Distributed Deployments
Commvault leverages RSA asymmetric encryption to establish secure communication between distributed system components across different sites or cloud environments. A dual-key system secures distributed Commvault deployments in which multiple sites must exchange data securely across untrusted networks without pre-shared encryption keys.
In this configuration, public keys can be distributed freely to initiate secure communication without compromising security. Private keys, on the other hand, remain confidential to individual systems, enabling authenticated communication channels. Key pair authentication ensures only authorized components can participate in backup operations.
Enterprise Security Integration
Active Directory integration enables authentication centralization for encryption key access, making sure that key permissions align with existing organizational security policies, including the following features:
- Single Sign-On capabilities streamline key access for authorized users.
- Role-based permissions control access to encryption keys based on job functions and data sensitivity.
- Comprehensive audit trails monitor security by documenting every key access attempt.
Hardware Security Module – HSM – support in Commvault provides enterprise-grade key protection using tamper-resistant hardware devices that exceed software-based security measures in several ways:
- Tamper-resistant key storage prevents physical key extraction attempts.
- Hardware-based cryptographic processing ensures key operations occur only in secure environments.
- FIPS 140-2 Level 3 compliance (U.S. federal security standard) for government and high-security environments.
Certificate Authority integration allows key management capabilities that are based on Public Key Infrastructure, leveraging the existing enterprise certificate infrastructure to reduce operational complexity and maintain necessary security standards.
How to Configure Data Encryption in Commvault Backup?
Commvault backup encryption configuration operates using storage policy settings and subclient properties. Commvault’s encryption configuration enables granular encryption controls across different data types, different retention periods, and different backup schedules. The platform’s configuration options support both automated deployment and customized security requirements.
Storage Policy Encryption Setup
The primary configuration path using CommCell Console is as follows:
- Access Storage Policy Properties > Advanced > Encryption
- Enable “Encrypt backup data” checkbox
- Select encryption placement: Client-side or MediaAgent-side processing
- Configure passphrase requirements or enable automatic key derivation
- Apply settings to existing and future backup jobs
There are three options for encryption placement here:
- Client-side encryption: Data is encrypted before network transmission, ensuring maximum security control
- MediaAgent encryption: Reduces client processing overhead, while maintaining comprehensive data protection
- Dual-layer encryption: A combination of client and MediaAgent encryption, for environments that need the strongest security measures imaginable
Comparison table for these options:
| Placement |
Client-side |
MediaAgent-side |
Dual-layer |
| Processing Location |
Source system before transmission |
Storage tier during backup |
Both options at once |
| Security Level |
Slightly above High |
High |
Maximum |
| Performance Impact |
Higher CPU usage for clients |
Lower client overhead |
Highest overhead |
| Best Use Case |
Highly sensitive data, compliance requirements |
High-volume environments, centralized processing |
Maximum security environments, critical information |
Subclient-Level Encryption Controls
Granular encryption management using subclient properties allows different levels of protection for different data types, closely following general guidelines for managing encryption:
- Critical databases: Maximum encryption and extended key retention policies.
- Filesystem backups: Standard encryption with a respectable combination of performance and security.
- Archive operations: Specialized encryption with long-term key management.
- Cloud destinations: Enhanced encryption for environments with little-to-no physical control.
Configuration inheritance allows encryption settings to cascade from storage policies to individual subclients, maintaining override capabilities for specific security requirements.
Network Communication Encryption
SSL/TLS protocol implementation – Secure Sockets Layer and Transport Layer Security, respectively – secures command and control communications among CommServe servers, MediaAgents, and client subsystems:
- Certificate-based authentication ensures only legitimate components establish secure channels.
- Automatic certificate management operates with certificate renewal and validation processes.
- Encrypted control channels protect backup job instructions and system management traffic.
Data stream encryption operates independently of network-level security, providing additional protection for backup data when it crosses potentially compromised network segments.
Encryption Policy Management
Schedule-based encryption policies enable time-sensitive security configuration with the ability to adjust protection levels automatically based on multiple backup types:
- Full backup schedules: Best encryption strength for comprehensive data protection
- Incremental backups: Optimized encryption settings for faster completion windows
- Synthetic full operations: Balanced encryption that maintains security with no major effect on performance.
Policy templates standardize encryption configurations across multiple backup environments, ensuring consistent security implementation while also reducing overall administrative complexity.
Exception handling accommodates special circumstances that require non-standard encryption with comprehensive audit trails and by documenting approval processes.
Advanced Configuration Options
Enabling hardware acceleration leverages processor encryption instructions (the aforementioned AES-NI) to minimize the performance impact of backup operations.
Coordinating compression with encryption ensures optimal data reduction using pre-encryption compression processing, maintaining security and maximizing storage efficiency at the same time.
Cross-platform compatibility settings ensure encrypted backups remain accessible during recovery operations across different operating systems and different versions of Commvault components
Software vs Hardware Encryption Implementation
Commvault supports both software-based encryption processing and hardware-accelerated encryption to accommodate a variety of performance requirements and infrastructure capabilities. Software encryption is universally compatible across diverse environments, while hardware acceleration can improve performance of high-volume backup tasks.
Software Encryption Deployment
Commvault’s universal compatibility with software encryption allows it to be deployed across any hardware platform with no specialized encryption processor requirements. Its primary advantages are:
- Cross-platform support for Windows, Linux, AIX, and Solaris environments
- Virtual machine compatibility with support for VMware, Hyper-V, and cloud instances
- Support for legacy systems, especially important for older hardware that lacks modern encryption instruction sets
- Consistent implementation on practically any hardware, regardless of its underlying infrastructure
This encryption type is also called CPU-based processing, because it uses standard processor capability to complete encryption, with performance directly affected by available computing resources and volumes of backup data.
Hardware Acceleration Benefits
Dedicated encryption instructions, such as AES-NI or SPARC (Scalable Processor ARChitecture) crypto units, offer significant advantages for performing encryption-intensive tasks. Dedicated encryption includes:
- Throughput optimization: Hardware acceleration reduces encryption overhead dramatically, compared with software encryption
- CPU utilization reduction: Dedicated encryption units also free general-purpose CPU cycles for other tasks
- Consistent performance: Hardware processing helps maintain stable encryption performance, regardless of the overall backup load
- Energy efficiency: Specialized encryption hardware consumes less power than its software-equivalent
Automatic detection capabilities allow Commvault to identify and utilize available hardware encryption capabilities without manual configuration.
Encryption Processing Placement
Encryption processing typically occurs either on the client side or on the MediaAgent side.
Client-side encryption completes cryptographic operations before any data transmission, ensuring that sensitive information never traverses networks in a readable form. Client-side encryption offers maximum security control with preliminary encryption, network bandwidth optimization using encrypted data that has been compressed, and compliance alignment with regulations that permit external transmission of only encrypted data. .
MediaAgent-side encryption centralizes cryptographic processing at the storage tier, while also reducing consumption of client-side resources. Its biggest benefits are client performance optimization, by limiting encryption to dedicated backup infrastructure, centralized key management through MediaAgent-controlled encryption operations, and storage integration that coordinates encryption with both deduplication and compression features.
Performance Optimization Strategies
The most common performance options for optimizing encryption tasks employ either optimized resource allocation or coordinated encryption pipelines.
Resource allocation balances encryption processing with other backup operations to achieve better total system performance and backup window compliance.
Coordinated encryption pipelines ensure optimal resource usage by using intelligent processing sequencing:
- Compressing data before encryption to improve storage efficiency
- Creating parallel encryption streams to leverage the capabilities of multi-core processors
- Optimizing memory buffers to prevent encryption bottlenecks during peak loads
- Coordinating network transmission for more consistency in the overall data flow
Deployment Considerations
Infrastructure assessment determines optimal encryption implementation based on existing hardware capabilities and performance requirements. Here are some of the more common examples:
- High-volume environments – Hardware acceleration is often necessary for optimal throughput during large-scale operations
- Distributed deployments – Software encryption can ensure a consistent level of security across varied infrastructure
- Cloud migration scenarios – Once again, software encryption is the best option for maintaining compatibility across different cloud provider environments
- Hybrid implementations – Mixed software and hardware encryption options may be best, depending on the capabilities of the specific system.
Storage Considerations for Encrypted Data
Encrypted backup data can dramatically change the behavior of the storage system, requiring a combination of capacity planning adjustments and performance optimization strategies to maintain backup efficiency. Knowing these impacts can help businesses optimize storage infrastructures and preserve encryption security benefits at the same time.
Deduplication Impact and Source-Side Solutions
Encryption processes disturb traditional deduplication because identical data blocks become unique encrypted sequences, which dramatically lower deduplication ratios across the board.
Commvault’s source-side deduplication preserves storage efficiency by identifying duplicate blocks before encryption begins:
- Pre-encryption analysis finds identical data segments across backup jobs
- Commvault combines deduplication and encryption security with single encryption per unique block
- Encrypted block indexing and management optimizes database deduplication Commvault’s method requires additional storage capacity, compared with unencrypted environments and traditional deduplication, making it a great middle-ground.
Capacity planning adjustments like the ones mentioned must account for both modified deduplication patterns and reduced compression effectiveness when encrypting existing backup infrastructures.
Auxiliary Copy Encryption Management
Automatic encryption inheritance, a great feature, ensures that the protection level given to any auxiliary copies is the same as the primary backup data source, which need not be configured separately. However, there are a few nuances worth mentioning:
- Tape library compatibility requires continuous processing power to support encrypted data streams
- Cross-platform synchronization helps maintain encryption key availability across different storage environments
- Performance validation is required to locate older tape hardware that may struggle with encrypted data throughput.
- Coordination among storage tiers ensures that encrypted data can move between different storage classes quickly and efficiently.
The availability of key management across auxiliary storage destinations prevents recovery failures during disaster scenarios due to missing decryption keys.
Compression Limitations and Workarounds
Inefficiency in encrypted data compression results from random data characteristics resisting compression using traditional algorithms, resulting in meager compression percentages, regardless of the compressibility of the original data. Most common pre-encryption compression strategies prevent this and maximize storage efficiency by using:
- Sequential processing: Applying compression before encryption processing;
- Algorithm selection: Choosing LZ-based compression, which better optimizes pre-encryption data patterns
- Storage calculation adjustments: Planning for roughly 20% larger backups of encrypted data. Tiering policy modifications: Accounting for reduced compression ratios across all storage tiers, when applicable
Long-term archive storage may also require serious capacity adjustments to store large volumes of encrypted data over extended time periods.
Performance Optimization for Large Datasets
Throughput maintenance during large backup operations calls for a careful combination of resource allocation and processing coordination.
Memory buffer scaling translates directly into additional RAM allocation for encryption processing queues. Parallel processing streams are required for multi-core processing of concurrent encryption tasks, as we mentioned earlier. Network bandwidth planning must also account for encrypted data transmission and subsequent expansion of the total data volumes transferred. I/O optimization implies fine tuning the storage subsystem for encrypted data write patterns.
Performance testing and optimization ensures backup window compliance, necessary to ensure that data can be encrypted within previously established timeframes.
Hardware resource monitoring can also identify potential bottlenecks in CPU, memory, or storage systems during encrypted backup operations, which supports more proactive capacity management.
Recovering Encrypted Backup Files in Commvault
Encrypted backup recovery uses automated key retrieval and transparent decryption processes, restoring information to its original readable format without additional administrative steps. Recovery procedures maintain identical workflows, whether data is encrypted or not, providing operational consistency during critical restoration scenarios.
Automated Key Retrieval Process
Seamless key access using integrated key validation and retrieval during recovery operations eliminates the need for manual key management intervention:
- Pre-recovery key validation confirms the availability of decryption keys before initiating the restoration process
- Centralized key management retrieves keys automatically during browsing.
- Session-based key caching maintains decryption capabilities throughout extended recovery sessions
- Transparent decryption processing can transform files back to their original format without user intervention
Consistent recovery operations ensure administrators can use identical procedures for restoration of both encrypted and unencrypted data , which reduces the risk of operational errors in emergency scenarios.
Cross-Platform Recovery Procedures
Multi-platform restoration maintains encryption compatibility across different operating systems and versions of Commvault components. Key format compatibility is required for decryption keys to remain functional across Windows, Linux, and Unix platforms.
Version independence allows encrypted backups that were created using older versions of Commvault to be restored in modern systems. Client system flexibility allows the recovery process to be conducted on different hardware platforms while the data remains accessible.
Network recovery support facilitates remote restoration operations across distributed infrastructures. Yet, destination system preparation requires that key access is properly configured before Commvault can initiate encrypted data recovery across platforms.
Granular Recovery Operations
Selective decryption capabilities allow administrators to restore specific files or folders without disrupting the encryption security of the rest of the backup. There are a few options worth mentioning here:
- File-level key management, which allows recovery of individual files without decrypting the entire backup dataset
- Folder-based restoration as a feature can maintain encryption boundaries for sensitive data compartmentalization
- Database object recovery supports application-specific restoration with appropriate decryption scope
- Point-in-time recovery preserves encryption settings based on specific backup timestamps
Additionally, these environments support mixed-mode recovery scenarios, accommodating situations in which recovered data require different levels of security, based on user access requirements and destination systems.
Emergency Key Recovery Protocols
Centralized key escrow allows emergency access to encryption keys, using secure administrative procedures, when standard key management environments are unavailable for one reason or another. This system includes at least four major elements: multi-person authentication, administrative override, secure key reconstruction, and emergency documentation requirements.
Multi-person authentication prevents unauthorized access to emergency keys using split-knowledge procedures. Administrative override capabilities offer key access to specific persons with sufficient privileges during disaster recovery if normal authentication systems fail.
Secure keys can be reconstructed from distributed key components stored across multiple secure locations. Emergency documentation requirements must cover all these actions and processes to ensure that audit trails of all emergency key access events are comprehensive.
Pre-positioned emergency keys and streamlined authorization procedures optimize recovery times and minimize restoration delays during critical business interruptions. Backup key storage maintains copies of encrypted keys in geographically separated locations to ensure availability during site-wide disasters or infrastructure failures.
Commvault Encryption Use Cases in Enterprise Environments
Enterprise encryption deployments vary substantially from one industry to another, depending on data sensitivity, operational constraints, specific regulatory requirements, and more. Knowing these implementation patterns should help businesses develop targeted encryption strategies that are aligned with their compliance obligations and business requirements. In this section, we dissect the workings of several general examples: situations with specific encryption requirements.
Healthcare HIPAA Compliance Implementation
Patient data protection requires comprehensive encryption across all backup processes to meet the requirements of HIPAA’s Technical Safeguards.
Configuration specifics:
- AES-256 encryption is mandatory for all backups of PHI (Patient Health Information), because all such information is considered highly sensitive.
- Client-side encryption is necessary to ensure PHI never traverses networks in a clear and readable format.
- Key retention policies must be aligned with HIPAA’s minimum 6-year record retention requirements
- Access logging for any and all instances of encryption key usage, correlated with patient identifiers
Operational requirements:
- Business Associate Agreements must be signed with cloud storage providers whenever using encrypted offsite backups
- Breach notification protocols should be simplified whenever encryption data exposure occurs
- Audit trail integration with existing HIPAA compliance monitoring systems is strictly required
- Staff training documentation is required for both encrypted backup procedures and emergency recovery
Financial Services Regulatory Requirements
ulti-framework compliance addresses SOX, PCI DSS, and regional banking regulations using coordinated encryption policies.
SOX compliance configuration:
- Financial record encryption and 7-year key retention for preserving audit trails
- Segregation of duties using different encryption keys for different types of financial data
- Change management controls for modifying encryption policies with approval workflows
- Independent verification of encryption effectiveness with quarterly compliance audits
PCI DSS implementation:
- Encryption of cardholder data with the help of validated cryptographic methods, such as AES-256
- Key management system aligns with the requirements of PCI DSS Key Management (Section 3.6)
- Secure key transmission between processing environments using RSA key pairs
- Annual penetration testing, including security validation for encrypted data storage
Manufacturing IP Protection Strategies
Safeguarding Intellectual property by using encryption to prevent exposure of competitive intelligence during insider threats or data breaches.
Design data protection:
- CAD file encryption using extended key retention periods for patient protection purposes
- Research data isolation using separate encryption domains for different product lines or categories
- Supply chain security is achieved with encrypted backup transmissions to manufacturing partners
- Version control integration maintains encryption across all backups of design iteration files
Cloud backup security:
- Dual-layer encryption using a combination of Commvault encryption and cloud provider encryption
- Geographic key distribution to prevent single-region key exposure for global operations
- Vendor risk management by using encrypted data transmissions to third-party manufacturers
- Export control compliance applied to all encrypted technical data crossing international boundaries
Multi-National Regulatory Coordination
Regional compliance management with the goal of addressing data protection requirements that vary across international jurisdictions.
GDPR implementation (EU-located operations):
- Personal data encryption with key destruction procedures, in accordance with the “right to be forgotten”
- Data sovereignty compliance using region-specific storage of encryption keys
- Privacy impact assessments to document the effectiveness of encryption for protecting personal data
- Cross-border transfer security achieved by replicating encrypted backup between EU and non-EN facilities
Country-specific requirements:
- China Cybersecurity Law: local storage of encryption keys with various procedures for government access
- Russia Data Localization: encrypted backup storage must be maintained within Russian territory
- India PDPB compliance: requirements for encryption of personal data with infrastructure to support local key management tasks
- Canada PIPEDA alignment: privacy protection with comprehensive backup encryption
Coordination strategies:
- Unified encryption policies with regional customization capabilities that are mandatory in many cases
- Multi-region key management to ensure compliance across every single operational territory
- Automated compliance reporting capable of generating region-specific encryption documentation
- Legal framework monitoring to monitor evolving international encryption requirements
Secure Encryption Key Management
Enterprise key security requires physical separation, access controls, and lifecycle management capable of protecting encryption keys throughout their entire operational lifespan. Comprehensive key management procedures balance accessibility for legitimate operations and the prevention of unauthorized access or accidental exposure.
Physical and Logical Key Separation
Geographic distribution ensures encryption keys never reside alongside protected information, maintaining appropriate security levels despite infrastructure compromises:
- Offsite key storage in geographically separated facilities is necessary to prevent single-point exposure
- Network segmentation isolates key management traffic from overall backup data transmission
- Administrative domain separation ensures that key administrators do not have access to encrypted backup content
- Hardware isolation with specialized key management appliances is appropriate for extremely sensitive content, granting extensive security measures separated from backup infrastructure.
Multi-tier separation strategies are popular for the most sophisticated situations, creating multiple security barriers that require coordinated efforts to access both keys and encrypted information at the same time.
Benefits of Centralized Key Management Server
Infrastructure dedicated to key management provides extensive security capabilities that exceed general-purpose server protection measures. These advantages can be divided into security enhancements and operational advantages.
Security enhancements:
- Hardware security modules equipped with tamper-resistant key storage and processing
- FIPS 140-2 Level 3 validation for high-security and government use cases
- Cryptographic key isolation prevents software-based attempts at key extraction
- Secure boot processes ensure the integrity of key management systems from startup
Operational advantages:
- High availability clustering prevents key server failures from disrupting backup operations
- Load distribution across several key servers improves encryption performance for enterprise-scale deployments
- API integration enables programmatic key management for automated backup environments
- Centralized audit logging is necessary to combine comprehensive key access monitoring and compliance reporting
Automated Key Rotation Procedures
A systematic approach to key rotation schedules balances security requirements with operational complexity, made possible with automated key lifecycle management. There are a few rotation frequency recommendations that we must review, along with the automated capabilities of the system itself.
Rotation frequency guidelines:
- Quarterly rotation is best for highly sensitive data and elevated security requirements
- Annual rotation works great for standard business data, balancing security with total operational impact
- Event-triggered rotation follows security incidents or personnel changes
- Compliance-driven rotation satisfies specific regulatory requirements; for example, PCI DSS requires annual key rotation
Automated processes:
- Seamless key transitions maintain the continuity of backup operations during rotation periods
- Historical key preservation ensures the ability to recover data throughout retention periods
- Rollback procedures enable quick reversion if rotation processes encounter difficulties
- Validation testing confirms new key functionality before completing a rotation cycle
Emergency Key Recovery Planning
Multi-layered contingency procedures can help restore key availability without compromising overall security during disaster scenarios – but they must be configured properly beforehand.
Key escrow implementation is based on split-knowledge storage, which distributes key components across multiple secure locations, along with M-of-N key sharing that requires multiple authorized personnel members to reconstruct encryption keys in emergency situations. Other beneficial tactics include time-locked access for preventing immediate key recovery without proper authorization, and geographic distribution to ensure key availability during region-specific disasters.
Recovery authorization protocols are often complex and multifaceted, which is why they warrant their own category:
- Emergency authorization matrix assists in defining the personnel authorized to conduct various key recovery scenarios
- Procedures for escalating various emergency severity levels requiring specific approval processes
- Documentation requirements verifying the validity of comprehensive audit trails for purposes of post-incident analysis
- Recovery Time Objectives aim to balance security validation and business continuity requirements
Post-recovery procedures have their own important elements to consider. Security assessment evaluates potential for key compromises during emergency scenarios, while key rotation scheduling accelerates rotation frequency following emergency access events. Process improvements incorporate lessons learned from earlier emergency recoveries, and compliance reporting documents emergency procedures to satisfy regulatory audit requirements.
Considering Other Options: Bacula Enterprise
To further showcase Commvault’s encryption capabilities, it is important to also compare its capabilities with the competition on the backup software market. Bacula Enterprise from Bacula Systems is a great choice for such a comparison, with exceptionally high security levels and its alternative encryption architecture. This uses, among other features, client-side cryptographic processing and PKI-based key management providing different implementation approaches for organizations to evaluate and consider backup encryption options.Bacula also offers its unique Signed Encryption, which can be critical for some government organizations.
Architecture Differences
Client-side encryption priority makes Bacula’s approach significantly different from Commvault’s encryption placement options. As a general rule, Bacula recommends that all encryption occur at source systems before network transmission, requiring dedicated PKI infrastructure for key distribution when assigning responsibilities. Such open-source transparency offers complete visibility into encryption implementation and its algorithms – which can be critical for organizations requiring security levels and checks that proprietary solutions cannot provide.
Alternatively, Commvault provides flexible encryption placement via client-side, MediaAgent-side, or dual-layer options with integrated key management capabilities (key generation and distribution capabilities are included). The platform offers centralized administration for unified encryption policy management across the enterprise infrastructure, along with proprietary optimizations for vendor-centric performance optimizations.
Encryption Feature Comparison
| Feature |
Bacula Enterprise |
Commvault |
| Encryption placement |
Client-side and/or server-side and dual-layer |
Client-side, MediaAgent-side, or dual-layer |
| Key management |
PKI-based, decentralized |
Integrated, centralized with HSM support |
| Supported algorithms |
AES-256, RSA, PKI and more |
AES-128/256, RSA |
| Administration |
Command-line, GUI-based, configuration files |
GUI-based |
| Cost model |
Subscription-based licensing. No data volume charges. |
Per-TB or per-client licensing |
Performance and Integration Characteristics of Bacula Enterprise
Efficient processing focuses on keeping encryption overhead to a minimum by using optimized cryptographic operations. Bacula provides direct storage integration with practically any kind of storage device, with native coordination of storage device encryption capabilities, combined with Linux ecosystem alignment delivering optimized performance. The platform maintains resource efficiency through lower memory and CPU overhead compared to many other enterprise solutions, while network optimization uses efficient encrypted data transmission to reduce bandwidth requirements.
Implementation considerations of Bacula’s implementation considerations include infrastructure compatibility requirements for Linux-based, and compatible, environments to achieve optimal performance. Scalability planning must account for performance characteristics that can vary substantially, depending on various infrastructure design choices.
Cost and Licensing Advantages
Bacula’s subscription-based licensing eliminates data volume charges by using annual subscription tiers based on the total number of agents, rather than backup data capacity. There are six subscription levels to choose from, with comprehensive support, updates, and unlimited technical assistance included in all of the existing tiers.
Enterprise deployment considerations must include calculations of total cost, while keeping infrastructure environments and administrative expertise in mind. Bacula Enterprise’s licensing costs are highly competitive compared to traditional backup solutions, but it is still important to budget for tape libraries, cloud storage integration, and specialized hardware based on the requirements of the backup architecture.
The vendor independence that accompanies subscription flexibility enables companies to avoid long-term vendor lock-in, while maintaining enterprise-grade support and features. Bacula Enterprise’s transparent pricing structure also eliminates surprise cost increases resulting from data growth, making capacity planning much more predictable.
Decision Framework
Bacula is an advantageous option for specific scenarios:
- Cost-sensitive environments that require advanced enterprise encryption levels without the overhead of proprietary licensing
- Sophisticated infrastructure with existing or diverse Linux-based backup and storage systems
- Customization requirements requiring encryption modification beyond standard vendor offerings
- Vendor diversification approaches to reduce dependency on single backup solution providers
- Security-conscious organizations such as defence, government and National Laboratories.
- Environments that require sustainable solutions due to company policies. Bacula’s open source background and low CO2 footprint is advantageous in Sustainable solutions and for fitting ESG requirements.
- Flexible compatibility – where complex or diverse IT environments require backup and recovery integration with many different databases, virtual environments, SaaS applications and various cloud and edge environments.Bacula is also completely storage agnostic.
- Fast-reaction enterprise support. Bacula offers immediate contact with senior engineers, saving precious time for the end-user.
- Advanced Deduplication. Bacula’s unique Global Endpoint Deduplication offers extremely high efficiency ratios
Commvault’s general benefits for enterprise deployments are:
- Comprehensive integration with the existing enterprise backup and recovery infrastructure
- Simplified administration with unified management interfaces and automated policy enforcement
- Enterprise support with guaranteed response times and established escalation procedures
- Advanced features like cloud integration, deduplication coordination, and various performance optimizations
Key Takeaways
Commvault’s encryption framework delivers enterprise-grade data protection with comprehensive cryptographic capabilities and flexible deployment options:
- Algorithm Support: AES-128 and AES-256 encryption with hardware acceleration through AES-NI processor instructions for best performance
- Flexible Placement: Encryption processing at client-side, MediaAgent-side, or dual-layer implementation, based on security and performance requirements
- Enterprise Key Management: Centralized key administration capabilities with HSM integration, Active Directory authentication, and support for RSA key pairs
- Regulatory Compliance: Built-in support for HIPAA, PCI DSS, GDPR, and SOX compliance requirements, using automated encryption policies and other measures
- Alternative Solutions: Bacula Enterprise delivers source-centric, PKI-based customizable encryption as a strong alternative to Commvault, with a low cost subscription-based licensing model.
Frequently Asked Questions
What encryption standards and algorithms does Commvault support?
Commvault supports AES-128 and AES-256 encryption with FIPS 140-2 validated cryptographic modules for government-grade security. RSA public key cryptography handles secure key exchanges between distributed components, while SHA-256 offers data integrity verification and secure password-based key generation. Support for different methods makes Commvault a versatile option in many situations, with AES-128 used for sufficient performance in high-volume operations, AES-256 providing effective protection for critical information, etc.
Can Commvault integrate with third-party encryption tools or HSMs?
Commvault’s Hardware Security Module integrates with standardized PKCS#11 interfaces supporting major HSM vendors – including SafeNet, Thales, and nCipher. Integration with third-party encryption tools can vary from one vendor to another, but relies on API-based connections to both coordinate cryptographic operations and manage the keys themselves.
What happens if encryption keys are lost or corrupted?
Commvault’s emergency key recovery procedures utilize secure key escrow with multi-person authentication requirements and geographically distributed backup keys. Lost keys without proper escrow arrangements may result in permanent data loss, making comprehensive key backup procedures essential before data is encrypted.
Does encryption work with cloud storage and auxiliary copies?
Cloud encryption implements dual-layer protection, combining client-side encryption before transmission and cloud provider encryption at destination. Auxiliary copies can automatically inherit encryption settings from primary backups, maintaining consistency in protection measures across all storage tiers (including tape libraries and offsite storage).
How does encrypted backup recovery differ from standard recovery?
With automatic key retrieval and decryption, transparent recovery operations work identically, whether data is encrypted or not. Both browse and restore workflows are also unchanged, with the system handling all cryptographic operations without administrator intervention.
At Bacula Systems, we believe that real feedback from IT professionals is the most powerful way to guide others toward reliable and efficient backup solutions. That’s why we’re inviting Bacula Enterprise users to share their experiences through a short online review — and receive a reward of up to $25 for doing so.
This initiative is part of a partnership with SoftwareReviews, a trusted platform that helps IT professionals evaluate software tools based on real user experiences. The goal is simple: empower organizations with authentic insights from hands-on users of Bacula Enterprise — while thanking you for your time and contribution.
Why Your Review Matters
Bacula Enterprise is known for its unmatched flexibility, scalability, and reliability across complex environments. From large enterprises managing petabytes of data to small teams needing rock-solid disaster recovery, Bacula is trusted around the world. But when prospective users look for backup solutions, they rely heavily on peer reviews to make informed decisions.
By taking 5–6 minutes to write a review, you:
- Provide valuable guidance to your peers in the IT, cybersecurity, and DevOps communities
- Highlight use cases, performance benchmarks, and unique features that may benefit others
- Help us understand what we’re doing right — and where we can improve
- Earn up to $25 as a thank-you, paid in your local currency
How It Works
- Visit the review page hosted by SoftwareReviews: Submit Your Bacula Enterprise Review
- Complete the short review form
- Once your submission is approved, you will receive your reward
Reviews must meet SoftwareReviews’ quality standards to be eligible, and each user can submit up to 10 quality reviews over a two-year period. Rewards will be issued in the equivalent amount in your local currency, where available.
What Should You Write About?
While you’re free to share your own perspective, here are some areas to consider:
- Why you chose Bacula Enterprise
- Your backup environment (e.g., virtual, cloud, hybrid, containers, databases)
- Performance and scalability
- Technical support experience
- Favorite features and any customizations
- Challenges you faced and how Bacula helped solve them
Help Others While Being Recognized
We know that IT professionals are often short on time — which makes your review even more valuable. Your insights can help others in the industry make better-informed decisions about backup and recovery platforms. And for your effort, you’ll receive a small reward as a token of appreciation.

 The SC25 conference (officially known under the name of International Conference for High Performance Computing, Networking, Storage, and Analysis) is taking place from November 16 to 21, 2025, in St. Louis, Missouri. It is a special event that operates as a global hub for professionals of the supercomputing community, such as researchers, scientists, educators, engineers, programmers, and developers.
The SC25 conference (officially known under the name of International Conference for High Performance Computing, Networking, Storage, and Analysis) is taking place from November 16 to 21, 2025, in St. Louis, Missouri. It is a special event that operates as a global hub for professionals of the supercomputing community, such as researchers, scientists, educators, engineers, programmers, and developers.