Contents
- How Does Commvault Handle Data Encryption?
- AES Encryption Standards in Commvault
- Multi-Layer Security Architecture
- Backup vs Archive vs Cloud Encryption Implementation
- Understanding Commvault’s Data-at-Rest Encryption
- Storage-Level Encryption Implementation
- Transparent Encryption Configuration Process in Commvault
- Configuration Steps for Encrypted Storage Policies
- Performance and Compliance Advantages
- How Does Key Management Work in Commvault?
- Hierarchical Key Architecture in Commvault
- Automated Key Generation Process
- RSA Key Pairs for Distributed Deployments
- Enterprise Security Integration
- How to Configure Data Encryption in Commvault Backup?
- Storage Policy Encryption Setup
- Subclient-Level Encryption Controls
- Network Communication Encryption
- Encryption Policy Management
- Advanced Configuration Options
- Software vs Hardware Encryption Implementation
- Software Encryption Deployment
- Hardware Acceleration Benefits
- Encryption Processing Placement
- Performance Optimization Strategies
- Deployment Considerations
- Storage Considerations for Encrypted Data
- Deduplication Impact and Source-Side Solutions
- Auxiliary Copy Encryption Management
- Compression Limitations and Workarounds
- Performance Optimization for Large Datasets
- Recovering Encrypted Backup Files in Commvault
- Automated Key Retrieval Process
- Cross-Platform Recovery Procedures
- Granular Recovery Operations
- Emergency Key Recovery Protocols
- Commvault Encryption Use Cases in Enterprise Environments
- Healthcare HIPAA Compliance Implementation
- Financial Services Regulatory Requirements
- Manufacturing IP Protection Strategies
- Multi-National Regulatory Coordination
- Secure Encryption Key Management
- Physical and Logical Key Separation
- Benefits of Centralized Key Management Server
- Automated Key Rotation Procedures
- Emergency Key Recovery Planning
- Considering Other Options: Bacula Enterprise
- Architecture Differences
- Encryption Feature Comparison
- Performance and Integration Characteristics of Bacula Enterprise
- Cost and Licensing Advantages
- Decision Framework
- Key Takeaways
- Frequently Asked Questions
- What encryption standards and algorithms does Commvault support?
- Can Commvault integrate with third-party encryption tools or HSMs?
- What happens if encryption keys are lost or corrupted?
- Does encryption work with cloud storage and auxiliary copies?
- How does encrypted backup recovery differ from standard recovery?
How Does Commvault Handle Data Encryption?
Commvault uses AES-256 and AES-128 encryption across backup, archive, and cloud storage tasks, offering enterprise-grade cryptographic protection for data throughout its lifecycle. Commvault’s backup encryption capabilities operate on multiple levels, protecting information both at rest in storage depositories and in transit between components.
AES Encryption Standards in Commvault
Commvault supports industry-standard Advanced Encryption Standard encryption with 128-bit and 256-bit key lengths, which enables organizations to balance performance requirements and security needs. AES-256 offers maximum cryptographic strength and is recommended for all highly-sensitive content, while AES-128 is an option in high-volume backup operations, with optimal performance and security capabilities.
The platform’s hardware acceleration support leverages modern processor encryption instructions (AES-NI for Advanced Encryption Standard – New Instructions) for minimal impact on performance. The total reduction of throughput rarely exceeds 10% with encryption enabled, making cryptographic protection nearly invisible during backup operations.
Multi-Layer Security Architecture
Encryption is the foundational security control in Commvault’s multi-layered security. Access controls and authentication help secure system perimeters in their own way, but without proper decryption keys, encryption renders backup data unreadable, even if storage systems themselves are physically compromised.
Commvault’s key security mechanisms include:
- Data obfuscation, which neutralizes stolen backup files
- Compliance automation to align with regulations requiring encrypted data storage
- Cloud security improvement in scenarios with limited physical control
- Persistent protection capable of continuing, even when other security controls have failed
Backup vs Archive vs Cloud Encryption Implementation
Backup encryption prioritizes rapid recovery capabilities using symmetric AES encryption, for optimal performance during restoration tasks. Backup jobs use AES-256 most of the time, for maximum security with limited impact on Recovery Time Objectives.
Archive encryption emphasizes long-term data integrity during extended retention periods. Archive encryption keys demand specialized lifecycle management to ensure accessibility for years or decades, while also maintaining suitable security throughout the entire retention period.
Cloud storage encryption uses dual-layer protection, with data encrypted on the client-side before transmission and cloud-provider encryption at the destination. This approach forms multiple security barriers against unauthorized access, while also maintaining compatibility with many useful cloud storage deduplication features.
Understanding Commvault’s Data-at-Rest Encryption
Commvault’s data-at-rest encryption secures backup files stored on disk drives, tape libraries, and cloud storage, using AES-256 encryption applied before data reaches its storage destination. This encryption works transparently within backup workflows and ensures that stored data remains unreadable without specific decryption keys.
Storage-Level Encryption Implementation
Data-at-rest encryption addresses the critical security gap created when backup files remain dormant in storage repositories. Physical storage theft, compromised cloud accounts, or unauthorized datacenter access cannot expose any readable data if all information is properly encrypted beforehand.
Regulatory compliance requirements mandate data-at-rest encryption for specific industries:
- HIPAA: Healthcare organizations are required to encrypt patient data in backup storage.
- CI DSS: Financial institutions require encrypted cardholder data storage.
- SOX: Public companies must encrypt financial records.
- GDPR: EU data protection requires encryption for backups of personal data.
Transparent Encryption Configuration Process in Commvault
Commvault implements transparent encryption (automatic encryption operations in the background) during backup operations, without requiring separate encryption steps or additional storage processing. The encryption process itself proceeds at the MediaAgent level before data is written to storage, ensuring that all backup data is cryptographically protected.
Commvault’s key hierarchy system protects individual file encryption keys using master key encryption. Multiple security layers prevent single-point encryption failures. Storage administrator isolation creates clear separation between storage management and data access privileges, ensuring that personnel with storage repository access do not have read access to backup data content.
Configuration Steps for Encrypted Storage Policies
A CommCell environment is a logical grouping of software elements that secure, move, store, and manage information in Commvault. Here is how to enable encryption using CommCell Concell:
- Navigate to Storage Policy Properties > Security Tab
- Select “Enable Encryption” checkbox
- Choose AES-256 for maximum security, or AES-128 for better performance
- Configure automatic key generation or specify custom encryption keys
- Apply encryption settings to new backup jobs as soon as possible
Granular encryption control allows different data types to be encrypted differently:
- Critical data: AES-256 encryption and extended key retention
- Standard backups: AES-128 encryption for performance balance
- Archive data: AES-256 with dedicated long-term key management
Performance and Compliance Advantages
Optimized encryption algorithms and hardware acceleration mean minimal impact on performance, because:
- Modern processors with AES-NI instructions reduce encryption overhead.
- Hardware acceleration combats encryption bottlenecks in backup windows.
- Transparent processing maintains identical backup and restore performance.
Automated encryption policies simplify compliance auditing. All stored data is automatically encrypted without manual input. Policy documentation provides audit-ready evidence of compliance. Restore operations function identically, whether information is encrypted or not.
Recovery operation compatibility ensures restoration of encrypted backups without additional complexity, eliminating operational overhead in critical recovery scenarios.
How Does Key Management Work in Commvault?
Commvault’s key management system works as the centralized control mechanism for generating encryption keys, as well as managing distribution, storage, and life cycles across enterprise backup environments. The system orchestrates all cryptographic operations while maintaining security separation between encryption keys and protected information.
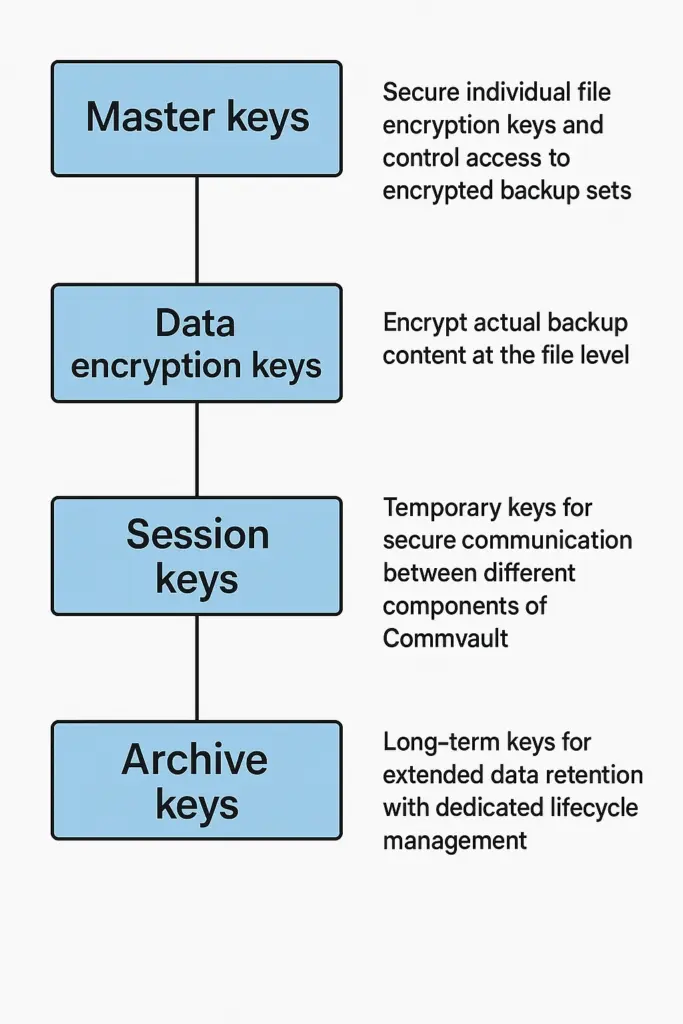
Hierarchical Key Architecture in Commvault
Commvault implements multi-tier key hierarchy, using master keys to protect individual data encryption keys, and preventing single-point encryption failures by creating multiple security checkpoints.
- Master keys: Secure individual file encryption keys and control access to encrypted backup sets.
- Data encryption keys: Encrypt actual backup content at the file level.
- Session keys: Temporary keys for secure communication between different components of Commvault.
- Archive keys: Long-term keys for extended data retention with dedicated lifecycle management.
This layered security approach prevents individual file keys that have been compromised from exposing entire backup repositories, while master key security helps maintain overall data protection integrity.
Automated Key Generation Process
Cryptographically secure random number generators produce unpredictable encryption keys using multiple entropy sources, including hardware-based randomness when available. System-generated keys eliminate human involvement, which can introduce predictable patterns or security weaknesses.
Key strength configurations:
- Standard encryption: Balanced security and performance for routine backup operations.
- Maximum encryption: Enhanced security for sensitive data and compliance requirements.
- Automatic encryption: Eliminates the possibility of manual key creation errors while ensuring the cryptographic strength.
Key generation is automatic during encryption policy creation, with no administrative intervention, while maintaining enterprise-grade security standards.
RSA Key Pairs for Distributed Deployments
Commvault leverages RSA asymmetric encryption to establish secure communication between distributed system components across different sites or cloud environments. A dual-key system secures distributed Commvault deployments in which multiple sites must exchange data securely across untrusted networks without pre-shared encryption keys.
In this configuration, public keys can be distributed freely to initiate secure communication without compromising security. Private keys, on the other hand, remain confidential to individual systems, enabling authenticated communication channels. Key pair authentication ensures only authorized components can participate in backup operations.
Enterprise Security Integration
Active Directory integration enables authentication centralization for encryption key access, making sure that key permissions align with existing organizational security policies, including the following features:
- Single Sign-On capabilities streamline key access for authorized users.
- Role-based permissions control access to encryption keys based on job functions and data sensitivity.
- Comprehensive audit trails monitor security by documenting every key access attempt.
Hardware Security Module – HSM – support in Commvault provides enterprise-grade key protection using tamper-resistant hardware devices that exceed software-based security measures in several ways:
- Tamper-resistant key storage prevents physical key extraction attempts.
- Hardware-based cryptographic processing ensures key operations occur only in secure environments.
- FIPS 140-2 Level 3 compliance (U.S. federal security standard) for government and high-security environments.
Certificate Authority integration allows key management capabilities that are based on Public Key Infrastructure, leveraging the existing enterprise certificate infrastructure to reduce operational complexity and maintain necessary security standards.
How to Configure Data Encryption in Commvault Backup?
Commvault backup encryption configuration operates using storage policy settings and subclient properties. Commvault’s encryption configuration enables granular encryption controls across different data types, different retention periods, and different backup schedules. The platform’s configuration options support both automated deployment and customized security requirements.
Storage Policy Encryption Setup
The primary configuration path using CommCell Console is as follows:
- Access Storage Policy Properties > Advanced > Encryption
- Enable “Encrypt backup data” checkbox
- Select encryption placement: Client-side or MediaAgent-side processing
- Configure passphrase requirements or enable automatic key derivation
- Apply settings to existing and future backup jobs
There are three options for encryption placement here:
- Client-side encryption: Data is encrypted before network transmission, ensuring maximum security control
- MediaAgent encryption: Reduces client processing overhead, while maintaining comprehensive data protection
- Dual-layer encryption: A combination of client and MediaAgent encryption, for environments that need the strongest security measures imaginable
Comparison table for these options:
| Placement | Client-side | MediaAgent-side | Dual-layer |
| Processing Location | Source system before transmission | Storage tier during backup | Both options at once |
| Security Level | Slightly above High | High | Maximum |
| Performance Impact | Higher CPU usage for clients | Lower client overhead | Highest overhead |
| Best Use Case | Highly sensitive data, compliance requirements | High-volume environments, centralized processing | Maximum security environments, critical information |
Subclient-Level Encryption Controls
Granular encryption management using subclient properties allows different levels of protection for different data types, closely following general guidelines for managing encryption:
- Critical databases: Maximum encryption and extended key retention policies.
- Filesystem backups: Standard encryption with a respectable combination of performance and security.
- Archive operations: Specialized encryption with long-term key management.
- Cloud destinations: Enhanced encryption for environments with little-to-no physical control.
Configuration inheritance allows encryption settings to cascade from storage policies to individual subclients, maintaining override capabilities for specific security requirements.
Network Communication Encryption
SSL/TLS protocol implementation – Secure Sockets Layer and Transport Layer Security, respectively – secures command and control communications among CommServe servers, MediaAgents, and client subsystems:
- Certificate-based authentication ensures only legitimate components establish secure channels.
- Automatic certificate management operates with certificate renewal and validation processes.
- Encrypted control channels protect backup job instructions and system management traffic.
Data stream encryption operates independently of network-level security, providing additional protection for backup data when it crosses potentially compromised network segments.
Encryption Policy Management
Schedule-based encryption policies enable time-sensitive security configuration with the ability to adjust protection levels automatically based on multiple backup types:
- Full backup schedules: Best encryption strength for comprehensive data protection
- Incremental backups: Optimized encryption settings for faster completion windows
- Synthetic full operations: Balanced encryption that maintains security with no major effect on performance.
Policy templates standardize encryption configurations across multiple backup environments, ensuring consistent security implementation while also reducing overall administrative complexity.
Exception handling accommodates special circumstances that require non-standard encryption with comprehensive audit trails and by documenting approval processes.
Advanced Configuration Options
Enabling hardware acceleration leverages processor encryption instructions (the aforementioned AES-NI) to minimize the performance impact of backup operations.
Coordinating compression with encryption ensures optimal data reduction using pre-encryption compression processing, maintaining security and maximizing storage efficiency at the same time.
Cross-platform compatibility settings ensure encrypted backups remain accessible during recovery operations across different operating systems and different versions of Commvault components
Software vs Hardware Encryption Implementation
Commvault supports both software-based encryption processing and hardware-accelerated encryption to accommodate a variety of performance requirements and infrastructure capabilities. Software encryption is universally compatible across diverse environments, while hardware acceleration can improve performance of high-volume backup tasks.
Software Encryption Deployment
Commvault’s universal compatibility with software encryption allows it to be deployed across any hardware platform with no specialized encryption processor requirements. Its primary advantages are:
- Cross-platform support for Windows, Linux, AIX, and Solaris environments
- Virtual machine compatibility with support for VMware, Hyper-V, and cloud instances
- Support for legacy systems, especially important for older hardware that lacks modern encryption instruction sets
- Consistent implementation on practically any hardware, regardless of its underlying infrastructure
This encryption type is also called CPU-based processing, because it uses standard processor capability to complete encryption, with performance directly affected by available computing resources and volumes of backup data.
Hardware Acceleration Benefits
Dedicated encryption instructions, such as AES-NI or SPARC (Scalable Processor ARChitecture) crypto units, offer significant advantages for performing encryption-intensive tasks. Dedicated encryption includes:
- Throughput optimization: Hardware acceleration reduces encryption overhead dramatically, compared with software encryption
- CPU utilization reduction: Dedicated encryption units also free general-purpose CPU cycles for other tasks
- Consistent performance: Hardware processing helps maintain stable encryption performance, regardless of the overall backup load
- Energy efficiency: Specialized encryption hardware consumes less power than its software-equivalent
Automatic detection capabilities allow Commvault to identify and utilize available hardware encryption capabilities without manual configuration.
Encryption Processing Placement
Encryption processing typically occurs either on the client side or on the MediaAgent side.
Client-side encryption completes cryptographic operations before any data transmission, ensuring that sensitive information never traverses networks in a readable form. Client-side encryption offers maximum security control with preliminary encryption, network bandwidth optimization using encrypted data that has been compressed, and compliance alignment with regulations that permit external transmission of only encrypted data. .
MediaAgent-side encryption centralizes cryptographic processing at the storage tier, while also reducing consumption of client-side resources. Its biggest benefits are client performance optimization, by limiting encryption to dedicated backup infrastructure, centralized key management through MediaAgent-controlled encryption operations, and storage integration that coordinates encryption with both deduplication and compression features.
Performance Optimization Strategies
The most common performance options for optimizing encryption tasks employ either optimized resource allocation or coordinated encryption pipelines.
Resource allocation balances encryption processing with other backup operations to achieve better total system performance and backup window compliance.
Coordinated encryption pipelines ensure optimal resource usage by using intelligent processing sequencing:
- Compressing data before encryption to improve storage efficiency
- Creating parallel encryption streams to leverage the capabilities of multi-core processors
- Optimizing memory buffers to prevent encryption bottlenecks during peak loads
- Coordinating network transmission for more consistency in the overall data flow
Deployment Considerations
Infrastructure assessment determines optimal encryption implementation based on existing hardware capabilities and performance requirements. Here are some of the more common examples:
- High-volume environments – Hardware acceleration is often necessary for optimal throughput during large-scale operations
- Distributed deployments – Software encryption can ensure a consistent level of security across varied infrastructure
- Cloud migration scenarios – Once again, software encryption is the best option for maintaining compatibility across different cloud provider environments
- Hybrid implementations – Mixed software and hardware encryption options may be best, depending on the capabilities of the specific system.
Storage Considerations for Encrypted Data
Encrypted backup data can dramatically change the behavior of the storage system, requiring a combination of capacity planning adjustments and performance optimization strategies to maintain backup efficiency. Knowing these impacts can help businesses optimize storage infrastructures and preserve encryption security benefits at the same time.
Deduplication Impact and Source-Side Solutions
Encryption processes disturb traditional deduplication because identical data blocks become unique encrypted sequences, which dramatically lower deduplication ratios across the board.
Commvault’s source-side deduplication preserves storage efficiency by identifying duplicate blocks before encryption begins:
- Pre-encryption analysis finds identical data segments across backup jobs
- Commvault combines deduplication and encryption security with single encryption per unique block
- Encrypted block indexing and management optimizes database deduplication Commvault’s method requires additional storage capacity, compared with unencrypted environments and traditional deduplication, making it a great middle-ground.
Capacity planning adjustments like the ones mentioned must account for both modified deduplication patterns and reduced compression effectiveness when encrypting existing backup infrastructures.
Auxiliary Copy Encryption Management
Automatic encryption inheritance, a great feature, ensures that the protection level given to any auxiliary copies is the same as the primary backup data source, which need not be configured separately. However, there are a few nuances worth mentioning:
- Tape library compatibility requires continuous processing power to support encrypted data streams
- Cross-platform synchronization helps maintain encryption key availability across different storage environments
- Performance validation is required to locate older tape hardware that may struggle with encrypted data throughput.
- Coordination among storage tiers ensures that encrypted data can move between different storage classes quickly and efficiently.
The availability of key management across auxiliary storage destinations prevents recovery failures during disaster scenarios due to missing decryption keys.
Compression Limitations and Workarounds
Inefficiency in encrypted data compression results from random data characteristics resisting compression using traditional algorithms, resulting in meager compression percentages, regardless of the compressibility of the original data. Most common pre-encryption compression strategies prevent this and maximize storage efficiency by using:
- Sequential processing: Applying compression before encryption processing;
- Algorithm selection: Choosing LZ-based compression, which better optimizes pre-encryption data patterns
- Storage calculation adjustments: Planning for roughly 20% larger backups of encrypted data. Tiering policy modifications: Accounting for reduced compression ratios across all storage tiers, when applicable
Long-term archive storage may also require serious capacity adjustments to store large volumes of encrypted data over extended time periods.
Performance Optimization for Large Datasets
Throughput maintenance during large backup operations calls for a careful combination of resource allocation and processing coordination.
Memory buffer scaling translates directly into additional RAM allocation for encryption processing queues. Parallel processing streams are required for multi-core processing of concurrent encryption tasks, as we mentioned earlier. Network bandwidth planning must also account for encrypted data transmission and subsequent expansion of the total data volumes transferred. I/O optimization implies fine tuning the storage subsystem for encrypted data write patterns.
Performance testing and optimization ensures backup window compliance, necessary to ensure that data can be encrypted within previously established timeframes.
Hardware resource monitoring can also identify potential bottlenecks in CPU, memory, or storage systems during encrypted backup operations, which supports more proactive capacity management.
Recovering Encrypted Backup Files in Commvault
Encrypted backup recovery uses automated key retrieval and transparent decryption processes, restoring information to its original readable format without additional administrative steps. Recovery procedures maintain identical workflows, whether data is encrypted or not, providing operational consistency during critical restoration scenarios.
Automated Key Retrieval Process
Seamless key access using integrated key validation and retrieval during recovery operations eliminates the need for manual key management intervention:
- Pre-recovery key validation confirms the availability of decryption keys before initiating the restoration process
- Centralized key management retrieves keys automatically during browsing.
- Session-based key caching maintains decryption capabilities throughout extended recovery sessions
- Transparent decryption processing can transform files back to their original format without user intervention
Consistent recovery operations ensure administrators can use identical procedures for restoration of both encrypted and unencrypted data , which reduces the risk of operational errors in emergency scenarios.
Cross-Platform Recovery Procedures
Multi-platform restoration maintains encryption compatibility across different operating systems and versions of Commvault components. Key format compatibility is required for decryption keys to remain functional across Windows, Linux, and Unix platforms.
Version independence allows encrypted backups that were created using older versions of Commvault to be restored in modern systems. Client system flexibility allows the recovery process to be conducted on different hardware platforms while the data remains accessible.
Network recovery support facilitates remote restoration operations across distributed infrastructures. Yet, destination system preparation requires that key access is properly configured before Commvault can initiate encrypted data recovery across platforms.
Granular Recovery Operations
Selective decryption capabilities allow administrators to restore specific files or folders without disrupting the encryption security of the rest of the backup. There are a few options worth mentioning here:
- File-level key management, which allows recovery of individual files without decrypting the entire backup dataset
- Folder-based restoration as a feature can maintain encryption boundaries for sensitive data compartmentalization
- Database object recovery supports application-specific restoration with appropriate decryption scope
- Point-in-time recovery preserves encryption settings based on specific backup timestamps
Additionally, these environments support mixed-mode recovery scenarios, accommodating situations in which recovered data require different levels of security, based on user access requirements and destination systems.
Emergency Key Recovery Protocols
Centralized key escrow allows emergency access to encryption keys, using secure administrative procedures, when standard key management environments are unavailable for one reason or another. This system includes at least four major elements: multi-person authentication, administrative override, secure key reconstruction, and emergency documentation requirements.
Multi-person authentication prevents unauthorized access to emergency keys using split-knowledge procedures. Administrative override capabilities offer key access to specific persons with sufficient privileges during disaster recovery if normal authentication systems fail.
Secure keys can be reconstructed from distributed key components stored across multiple secure locations. Emergency documentation requirements must cover all these actions and processes to ensure that audit trails of all emergency key access events are comprehensive.
Pre-positioned emergency keys and streamlined authorization procedures optimize recovery times and minimize restoration delays during critical business interruptions. Backup key storage maintains copies of encrypted keys in geographically separated locations to ensure availability during site-wide disasters or infrastructure failures.
Commvault Encryption Use Cases in Enterprise Environments
Enterprise encryption deployments vary substantially from one industry to another, depending on data sensitivity, operational constraints, specific regulatory requirements, and more. Knowing these implementation patterns should help businesses develop targeted encryption strategies that are aligned with their compliance obligations and business requirements. In this section, we dissect the workings of several general examples: situations with specific encryption requirements.
Healthcare HIPAA Compliance Implementation
Patient data protection requires comprehensive encryption across all backup processes to meet the requirements of HIPAA’s Technical Safeguards.
Configuration specifics:
- AES-256 encryption is mandatory for all backups of PHI (Patient Health Information), because all such information is considered highly sensitive.
- Client-side encryption is necessary to ensure PHI never traverses networks in a clear and readable format.
- Key retention policies must be aligned with HIPAA’s minimum 6-year record retention requirements
- Access logging for any and all instances of encryption key usage, correlated with patient identifiers
Operational requirements:
- Business Associate Agreements must be signed with cloud storage providers whenever using encrypted offsite backups
- Breach notification protocols should be simplified whenever encryption data exposure occurs
- Audit trail integration with existing HIPAA compliance monitoring systems is strictly required
- Staff training documentation is required for both encrypted backup procedures and emergency recovery
Financial Services Regulatory Requirements
ulti-framework compliance addresses SOX, PCI DSS, and regional banking regulations using coordinated encryption policies.
SOX compliance configuration:
- Financial record encryption and 7-year key retention for preserving audit trails
- Segregation of duties using different encryption keys for different types of financial data
- Change management controls for modifying encryption policies with approval workflows
- Independent verification of encryption effectiveness with quarterly compliance audits
PCI DSS implementation:
- Encryption of cardholder data with the help of validated cryptographic methods, such as AES-256
- Key management system aligns with the requirements of PCI DSS Key Management (Section 3.6)
- Secure key transmission between processing environments using RSA key pairs
- Annual penetration testing, including security validation for encrypted data storage
Manufacturing IP Protection Strategies
Safeguarding Intellectual property by using encryption to prevent exposure of competitive intelligence during insider threats or data breaches.
Design data protection:
- CAD file encryption using extended key retention periods for patient protection purposes
- Research data isolation using separate encryption domains for different product lines or categories
- Supply chain security is achieved with encrypted backup transmissions to manufacturing partners
- Version control integration maintains encryption across all backups of design iteration files
Cloud backup security:
- Dual-layer encryption using a combination of Commvault encryption and cloud provider encryption
- Geographic key distribution to prevent single-region key exposure for global operations
- Vendor risk management by using encrypted data transmissions to third-party manufacturers
- Export control compliance applied to all encrypted technical data crossing international boundaries
Multi-National Regulatory Coordination
Regional compliance management with the goal of addressing data protection requirements that vary across international jurisdictions.
GDPR implementation (EU-located operations):
- Personal data encryption with key destruction procedures, in accordance with the “right to be forgotten”
- Data sovereignty compliance using region-specific storage of encryption keys
- Privacy impact assessments to document the effectiveness of encryption for protecting personal data
- Cross-border transfer security achieved by replicating encrypted backup between EU and non-EN facilities
Country-specific requirements:
- China Cybersecurity Law: local storage of encryption keys with various procedures for government access
- Russia Data Localization: encrypted backup storage must be maintained within Russian territory
- India PDPB compliance: requirements for encryption of personal data with infrastructure to support local key management tasks
- Canada PIPEDA alignment: privacy protection with comprehensive backup encryption
Coordination strategies:
- Unified encryption policies with regional customization capabilities that are mandatory in many cases
- Multi-region key management to ensure compliance across every single operational territory
- Automated compliance reporting capable of generating region-specific encryption documentation
- Legal framework monitoring to monitor evolving international encryption requirements
Secure Encryption Key Management
Enterprise key security requires physical separation, access controls, and lifecycle management capable of protecting encryption keys throughout their entire operational lifespan. Comprehensive key management procedures balance accessibility for legitimate operations and the prevention of unauthorized access or accidental exposure.
Physical and Logical Key Separation
Geographic distribution ensures encryption keys never reside alongside protected information, maintaining appropriate security levels despite infrastructure compromises:
- Offsite key storage in geographically separated facilities is necessary to prevent single-point exposure
- Network segmentation isolates key management traffic from overall backup data transmission
- Administrative domain separation ensures that key administrators do not have access to encrypted backup content
- Hardware isolation with specialized key management appliances is appropriate for extremely sensitive content, granting extensive security measures separated from backup infrastructure.
Multi-tier separation strategies are popular for the most sophisticated situations, creating multiple security barriers that require coordinated efforts to access both keys and encrypted information at the same time.
Benefits of Centralized Key Management Server
Infrastructure dedicated to key management provides extensive security capabilities that exceed general-purpose server protection measures. These advantages can be divided into security enhancements and operational advantages.
Security enhancements:
- Hardware security modules equipped with tamper-resistant key storage and processing
- FIPS 140-2 Level 3 validation for high-security and government use cases
- Cryptographic key isolation prevents software-based attempts at key extraction
- Secure boot processes ensure the integrity of key management systems from startup
Operational advantages:
- High availability clustering prevents key server failures from disrupting backup operations
- Load distribution across several key servers improves encryption performance for enterprise-scale deployments
- API integration enables programmatic key management for automated backup environments
- Centralized audit logging is necessary to combine comprehensive key access monitoring and compliance reporting
Automated Key Rotation Procedures
A systematic approach to key rotation schedules balances security requirements with operational complexity, made possible with automated key lifecycle management. There are a few rotation frequency recommendations that we must review, along with the automated capabilities of the system itself.
Rotation frequency guidelines:
- Quarterly rotation is best for highly sensitive data and elevated security requirements
- Annual rotation works great for standard business data, balancing security with total operational impact
- Event-triggered rotation follows security incidents or personnel changes
- Compliance-driven rotation satisfies specific regulatory requirements; for example, PCI DSS requires annual key rotation
Automated processes:
- Seamless key transitions maintain the continuity of backup operations during rotation periods
- Historical key preservation ensures the ability to recover data throughout retention periods
- Rollback procedures enable quick reversion if rotation processes encounter difficulties
- Validation testing confirms new key functionality before completing a rotation cycle
Emergency Key Recovery Planning
Multi-layered contingency procedures can help restore key availability without compromising overall security during disaster scenarios – but they must be configured properly beforehand.
Key escrow implementation is based on split-knowledge storage, which distributes key components across multiple secure locations, along with M-of-N key sharing that requires multiple authorized personnel members to reconstruct encryption keys in emergency situations. Other beneficial tactics include time-locked access for preventing immediate key recovery without proper authorization, and geographic distribution to ensure key availability during region-specific disasters.
Recovery authorization protocols are often complex and multifaceted, which is why they warrant their own category:
- Emergency authorization matrix assists in defining the personnel authorized to conduct various key recovery scenarios
- Procedures for escalating various emergency severity levels requiring specific approval processes
- Documentation requirements verifying the validity of comprehensive audit trails for purposes of post-incident analysis
- Recovery Time Objectives aim to balance security validation and business continuity requirements
Post-recovery procedures have their own important elements to consider. Security assessment evaluates potential for key compromises during emergency scenarios, while key rotation scheduling accelerates rotation frequency following emergency access events. Process improvements incorporate lessons learned from earlier emergency recoveries, and compliance reporting documents emergency procedures to satisfy regulatory audit requirements.
Considering Other Options: Bacula Enterprise
To further showcase Commvault’s encryption capabilities, it is important to also compare its capabilities with the competition on the backup software market. Bacula Enterprise from Bacula Systems is a great choice for such a comparison, with exceptionally high security levels and its alternative encryption architecture. This uses, among other features, client-side cryptographic processing and PKI-based key management providing different implementation approaches for organizations to evaluate and consider backup encryption options.Bacula also offers its unique Signed Encryption, which can be critical for some government organizations.
Architecture Differences
Client-side encryption priority makes Bacula’s approach significantly different from Commvault’s encryption placement options. As a general rule, Bacula recommends that all encryption occur at source systems before network transmission, requiring dedicated PKI infrastructure for key distribution when assigning responsibilities. Such open-source transparency offers complete visibility into encryption implementation and its algorithms – which can be critical for organizations requiring security levels and checks that proprietary solutions cannot provide.
Alternatively, Commvault provides flexible encryption placement via client-side, MediaAgent-side, or dual-layer options with integrated key management capabilities (key generation and distribution capabilities are included). The platform offers centralized administration for unified encryption policy management across the enterprise infrastructure, along with proprietary optimizations for vendor-centric performance optimizations.
Encryption Feature Comparison
| Feature | Bacula Enterprise | Commvault |
| Encryption placement | Client-side and/or server-side and dual-layer | Client-side, MediaAgent-side, or dual-layer |
| Key management | PKI-based, decentralized | Integrated, centralized with HSM support |
| Supported algorithms | AES-256, RSA, PKI and more | AES-128/256, RSA |
| Administration | Command-line, GUI-based, configuration files | GUI-based |
| Cost model | Subscription-based licensing. No data volume charges. | Per-TB or per-client licensing |
Performance and Integration Characteristics of Bacula Enterprise
Efficient processing focuses on keeping encryption overhead to a minimum by using optimized cryptographic operations. Bacula provides direct storage integration with practically any kind of storage device, with native coordination of storage device encryption capabilities, combined with Linux ecosystem alignment delivering optimized performance. The platform maintains resource efficiency through lower memory and CPU overhead compared to many other enterprise solutions, while network optimization uses efficient encrypted data transmission to reduce bandwidth requirements.
Implementation considerations of Bacula’s implementation considerations include infrastructure compatibility requirements for Linux-based, and compatible, environments to achieve optimal performance. Scalability planning must account for performance characteristics that can vary substantially, depending on various infrastructure design choices.
Cost and Licensing Advantages
Bacula’s subscription-based licensing eliminates data volume charges by using annual subscription tiers based on the total number of agents, rather than backup data capacity. There are six subscription levels to choose from, with comprehensive support, updates, and unlimited technical assistance included in all of the existing tiers.
Enterprise deployment considerations must include calculations of total cost, while keeping infrastructure environments and administrative expertise in mind. Bacula Enterprise’s licensing costs are highly competitive compared to traditional backup solutions, but it is still important to budget for tape libraries, cloud storage integration, and specialized hardware based on the requirements of the backup architecture.
The vendor independence that accompanies subscription flexibility enables companies to avoid long-term vendor lock-in, while maintaining enterprise-grade support and features. Bacula Enterprise’s transparent pricing structure also eliminates surprise cost increases resulting from data growth, making capacity planning much more predictable.
Decision Framework
Bacula is an advantageous option for specific scenarios:
- Cost-sensitive environments that require advanced enterprise encryption levels without the overhead of proprietary licensing
- Sophisticated infrastructure with existing or diverse Linux-based backup and storage systems
- Customization requirements requiring encryption modification beyond standard vendor offerings
- Vendor diversification approaches to reduce dependency on single backup solution providers
- Security-conscious organizations such as defence, government and National Laboratories.
- Environments that require sustainable solutions due to company policies. Bacula’s open source background and low CO2 footprint is advantageous in Sustainable solutions and for fitting ESG requirements.
- Flexible compatibility – where complex or diverse IT environments require backup and recovery integration with many different databases, virtual environments, SaaS applications and various cloud and edge environments.Bacula is also completely storage agnostic.
- Fast-reaction enterprise support. Bacula offers immediate contact with senior engineers, saving precious time for the end-user.
- Advanced Deduplication. Bacula’s unique Global Endpoint Deduplication offers extremely high efficiency ratios
Commvault’s general benefits for enterprise deployments are:
- Comprehensive integration with the existing enterprise backup and recovery infrastructure
- Simplified administration with unified management interfaces and automated policy enforcement
- Enterprise support with guaranteed response times and established escalation procedures
- Advanced features like cloud integration, deduplication coordination, and various performance optimizations
Key Takeaways
Commvault’s encryption framework delivers enterprise-grade data protection with comprehensive cryptographic capabilities and flexible deployment options:
- Algorithm Support: AES-128 and AES-256 encryption with hardware acceleration through AES-NI processor instructions for best performance
- Flexible Placement: Encryption processing at client-side, MediaAgent-side, or dual-layer implementation, based on security and performance requirements
- Enterprise Key Management: Centralized key administration capabilities with HSM integration, Active Directory authentication, and support for RSA key pairs
- Regulatory Compliance: Built-in support for HIPAA, PCI DSS, GDPR, and SOX compliance requirements, using automated encryption policies and other measures
- Alternative Solutions: Bacula Enterprise delivers source-centric, PKI-based customizable encryption as a strong alternative to Commvault, with a low cost subscription-based licensing model.
Frequently Asked Questions
What encryption standards and algorithms does Commvault support?
Commvault supports AES-128 and AES-256 encryption with FIPS 140-2 validated cryptographic modules for government-grade security. RSA public key cryptography handles secure key exchanges between distributed components, while SHA-256 offers data integrity verification and secure password-based key generation. Support for different methods makes Commvault a versatile option in many situations, with AES-128 used for sufficient performance in high-volume operations, AES-256 providing effective protection for critical information, etc.
Can Commvault integrate with third-party encryption tools or HSMs?
Commvault’s Hardware Security Module integrates with standardized PKCS#11 interfaces supporting major HSM vendors – including SafeNet, Thales, and nCipher. Integration with third-party encryption tools can vary from one vendor to another, but relies on API-based connections to both coordinate cryptographic operations and manage the keys themselves.
What happens if encryption keys are lost or corrupted?
Commvault’s emergency key recovery procedures utilize secure key escrow with multi-person authentication requirements and geographically distributed backup keys. Lost keys without proper escrow arrangements may result in permanent data loss, making comprehensive key backup procedures essential before data is encrypted.
Does encryption work with cloud storage and auxiliary copies?
Cloud encryption implements dual-layer protection, combining client-side encryption before transmission and cloud provider encryption at destination. Auxiliary copies can automatically inherit encryption settings from primary backups, maintaining consistency in protection measures across all storage tiers (including tape libraries and offsite storage).
How does encrypted backup recovery differ from standard recovery?
With automatic key retrieval and decryption, transparent recovery operations work identically, whether data is encrypted or not. Both browse and restore workflows are also unchanged, with the system handling all cryptographic operations without administrator intervention.


